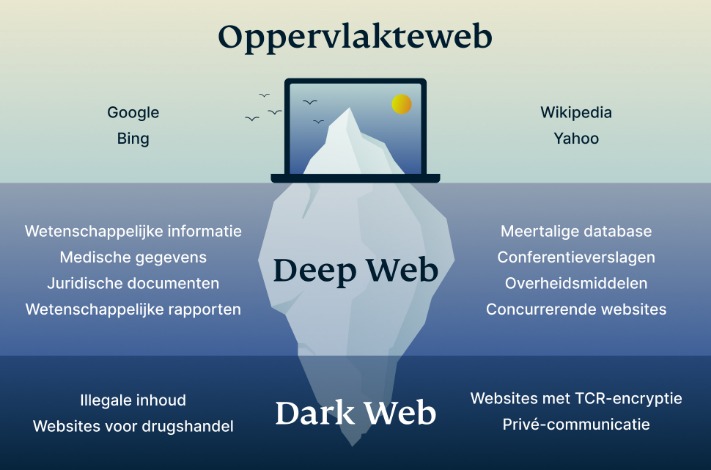
Understanding Darknet Links
Understanding darknet links is essential for navigating the hidden layers of the internet where anonymity and privacy are prioritized. These links lead to websites hosted on the darknet, a part of the internet not accessible through standard search engines or browsers. They often use specialized networks like Tor to ensure user confidentiality. Darknet links typically consist of complex alphanumeric addresses with the “.onion” suffix, providing secure and anonymous access to various online services. Exploring darknet links can reveal a wide range of content, but it also requires caution due to the presence of illicit activities. To better understand how these sites operate, one can examine examples like a darknet site that showcases the diverse and often concealed nature of this part of the internet.
Definition and Purpose of Darknet Links
Darknet links are specialized URLs that provide access to websites operating within the hidden parts of the internet, often referred to as the darknet. These links are distinct from conventional web links because they typically utilize anonymous network protocols, such as Tor or I2P, which ensure user privacy and data security. The primary purpose of darknet links is to facilitate access to online spaces where users can communicate, share information, or conduct activities with a high degree of anonymity and security.

These links often serve as gateway URLs that connect users to hidden services or portals on the darknet. Their unique structure, which may include random or semi-random strings of characters, helps conceal the actual location of the websites and protects them from detection or censorship. Darknet links are vital for maintaining the privacy of individuals engaging in activities that require secure communication channels or for accessing content not available on the surface web.
The purpose of darknet links extends beyond privacy; they are also used to promote secure marketplaces, discussion forums, or information repositories that operate outside the reach of traditional oversight. While they are an essential tool for those seeking privacy or circumventing censorship, they can also be associated with illicit activities. Understanding the function of darknet links is crucial for ensuring safe and informed navigation of these hidden online spaces.
Differences Between Darknet and Surface Web Links
Darknet links refer to the URLs that provide access to hidden parts of the internet, often requiring specialized software and configurations to access. These links typically utilize the “.onion” suffix, which designates sites hosted within the Tor network, providing users with increased anonymity and privacy. Darknet links are commonly associated with secretive forums, marketplaces, and information-sharing platforms that operate outside the reach of conventional search engines and authorities. Understanding these links is essential for grasping the structure and function of the dark web.
In contrast, surface web links lead to websites that are readily accessible through standard web browsers and are indexed by popular search engines. These links are part of the open internet, where content is publicly available and easily discoverable. The key difference between darknet and surface web links lies in their accessibility and visibility. While surface web links are designed for ease of use and wide visibility, darknet links are hidden, often requiring specific tools such as the Tor browser to access and navigate.
Darknet links are typically characterized by their anonymity features, enabling users to browse and communicate without revealing personal information. This attribute makes darknet links attractive for various purposes, including privacy protection, activism, or illicit activities. It is important to understand the nature of darknet links and the significant differences from surface web links to navigate the internet securely and responsibly within both spaces. Recognizing these distinctions helps users comprehend the structure of online networks and the importance of cybersecurity measures in the digital age.
Common Uses of Darknet Links
Darknet links refer to URLs that provide access to websites hosted on the dark web, a part of the internet not indexed by traditional search engines. These links often use specialized domain suffixes and encryption methods to ensure anonymity and security for both site operators and visitors. Understanding the nature of darknet links is crucial for anyone seeking to navigate this hidden segment of the internet, whether for research, privacy, or other purposes.
Darknet links serve a variety of functions and are used in numerous contexts. Some of the most common uses include:
- Providing access to encrypted communication platforms where privacy is a priority.
- Hosting marketplaces that facilitate the anonymous trade of goods and services, both legal and illegal.
- Sharing sensitive information or whistleblowing channels that require anonymity for protection.
- Distributing rare or restricted content that is not available on the surface web.
While darknet links can support legitimate activities such as secure communication and free expression, they are also frequently associated with illicit operations. Users must exercise caution and ensure they understand the risks involved when exploring these links. The dark web continues to evolve as both a haven for privacy advocates and a hub for malicious activities, making awareness and knowledge essential for safe navigation.
Accessing and Identifying Darknet Links
Accessing and identifying darknet links is a critical skill for navigating the hidden parts of the internet securely and effectively. The darknet, consisting of anonymous networks and sites not indexed by conventional search engines, often hosts a variety of content that requires specialized tools and techniques to access. Recognizing legitimate darknet links, such as darknet addresses, and understanding how to verify their authenticity is essential for users exploring this complex environment. Knowing how to identify these links ensures safer browsing and helps avoid malicious or unreliable sites in the darknet landscape.
How Darknet Links Are Structured
The darknet, a part of the internet not indexed by traditional search engines, hosts a variety of websites and links that are often hidden from the general public. Accessing and identifying darknet links requires specialized knowledge and tools, as these links are structured differently from standard web URLs. Typically, darknet links are characterized by their use of specific domain extensions such as .onion, which are only accessible through anonymizing browsers like Tor. These links often appear as long, random strings of characters or complex URLs designed to obscure their destinations, ensuring privacy and anonymity for users and site operators alike.
Darknet links are structured in a way that emphasizes security and privacy over readability. A typical darknet link consists of an alphanumeric address, sometimes with additional directories or parameters, ending with the .onion suffix. For example, a standard darknet link might look like a string of letters and numbers followed by .onion, representing a unique network address. This structure makes it relatively straightforward to identify a link as part of the darknet, especially when compared to traditional web URLs. However, because these links are intentionally complex and obscure, identifying genuine darknet sites requires caution and understanding of their distinctive format.
To access darknet links, users need to utilize anonymizing browsers, with the Tor Browser being the most common choice. This browser is configured specifically for accessing .onion addresses securely and anonymously. When attempting to identify darknet links, it is essential to verify the domain format carefully. Look for the characteristic .onion extension and the irregular string of characters that precedes it. Due to the hidden nature of these sites, many darknet links are distributed through encrypted forums, marketplaces, or directories that often require some level of prior knowledge or authorization to access. Recognizing these links involves understanding their structure and the context in which they are shared, while always exercising caution to avoid malicious content or illegal activities.
Tools and Resources for Finding Darknet Links
Exploring the darknet to access and identify darknet links requires a careful and informed approach due to its complex and often hidden nature. The darknet consists of a collection of networks that operate anonymously, often utilizing special browsers like Tor or I2P to maintain user privacy and security. To navigate safely, it is essential to understand the tools and resources that facilitate finding and verifying darknet links.
One fundamental tool for accessing darknet content is the Tor Browser, which enables users to connect to .onion sites privately and securely. Using Tor, users can access hidden services that are not available through standard browsers, making it a crucial resource for identifying legitimate darknet links. Additionally, indexing sites and directories dedicated to the darknet serve as valuable resources, providing curated lists of active links and resources for different categories of content.
Various search engines optimized for dark web exploration can also assist in locating specific darknet links. These search engines index a subset of darknet pages, allowing users to find relevant links based on keywords or categories. Security-focused forums and online communities are further resources where experienced users share verified darknet links, discuss potential threats, and exchange tips for safe navigation.
Tools like link scanners and verification services can help identify whether a darknet link is active and safe to visit, reducing the risk of malicious content. Users should exercise caution and employ comprehensive cybersecurity measures when exploring these links because predators or malicious actors frequently operate within some dark web sections. Staying informed about the latest tools, security practices, and trusted sources enhances the ability to find and access darknet links responsibly and securely.
Risks Associated with Accessing Darknet Links
Accessing and identifying darknet links can be a complex and potentially risky activity. Darknet links typically refer to URLs that lead to hidden parts of the internet accessible only through specific software like Tor, providing anonymity to users and hosts. These links often have unique structures or domains that distinguish them from regular websites, requiring careful scrutiny to verify their authenticity and purpose. Recognizing darknet links involves looking for certain patterns, such as long numerical addresses or the use of specialized domain extensions, which can be indicators of content hosted on the dark web.
However, navigating the darknet carries significant risks. Many links on the dark web host illegal or harmful content that could compromise your security or lead to legal consequences if accessed unknowingly. Malicious actors frequently use darknet links to distribute malware or conduct scams, making it essential to exercise caution. Understanding the risks associated with accessing darknet links is crucial; these include exposure to illegal activities, potential data breaches, and the danger of encountering harmful content. Always ensure you have adequate cybersecurity measures and legal awareness before attempting to access or analyze darknet links.
Security Considerations for Darknet Links
Exploring darknet links involves understanding the unique security challenges they present. These links often lead to anonymous websites that operate outside the conventional web, providing both privacy and increased risk. When accessing darknet links such as nexusafejew45osqaawl2xqjwmincsfvjwuwtm2fums2kjeon7tbmlid.onion, users must be aware of potential threats including malicious content, scams, and data interception. Ensuring safety requires employing strong security measures, such as using trusted VPNs, maintaining updated security tools, and practicing cautious browsing habits.
Potential Threats from Darknet Links
Darknet links, often associated with anonymous and encrypted online environments, pose significant security considerations for users and organizations alike. While they provide a means for confidential communication and access to restricted information, these links are frequently exploited for malicious activities. Understanding the potential threats linked to darknet links is essential to mitigate risks and maintain cybersecurity integrity.
One primary concern is the exposure to malicious content. Darknet links can lead to illegal marketplaces, malware repositories, and phishing sites that are designed to deceive users or compromise their systems. Clicking on such links without proper verification can result in malware infections, data theft, or ransomware attacks. Additionally, these links are often used to distribute illicit goods and services, increasing the likelihood of encountering scams or fraudulent schemes.
Besides direct threats, darknet links can serve as vectors for infiltrating broader networks. Cybercriminals may embed malware within files accessible through these links, which, when downloaded, can exploit vulnerabilities in the user’s device. This can lead to persistent threats such as backdoors or keyloggers that remain active long after initial access. Moreover, users who engage with darknet links risk unintentionally supporting illegal operations or compromising their anonymity, which could have legal repercussions.
To mitigate these risks, it is crucial to implement comprehensive security measures. This includes educating users about recognizing suspicious links, employing robust antivirus and anti-malware solutions, and restricting access to unknown or untrusted sources. Regular updates to software and security protocols also play a vital role in closing vulnerabilities that could be exploited via darknet links.
- Be cautious of clicking on unfamiliar darknet links, especially those received through unsolicited messages or emails.
- Utilize secure browsing environments and sandboxing tools to analyze suspicious links safely.
- Maintain updated security software that can detect and block malicious content associated with darknet links.
- Limit access to darknet content within organizational networks unless necessary, and monitor network traffic for anomalies.
In summary, darknet links present significant security threats ranging from malware infections to legal and privacy risks. Awareness and proactive security measures are essential to protect individuals and organizations from the potential consequences associated with navigating or engaging with darknet content.
Best Practices for Safe Navigation
Accessing darknet links presents unique security challenges that require careful precautions to ensure safety and privacy. The dark web hosts a variety of content, some of which can pose significant risks if navigated without proper security measures. It is essential for users to understand the potential dangers and adopt best practices to minimize vulnerabilities when exploring these links.
One of the primary considerations when dealing with darknet links is maintaining anonymity. Utilizing trusted tools such as the Tor browser helps safeguard user identities by routing traffic through multiple servers, making tracking more difficult. However, users should ensure their browser and associated software are always up to date to protect against known vulnerabilities that could be exploited by malicious actors.
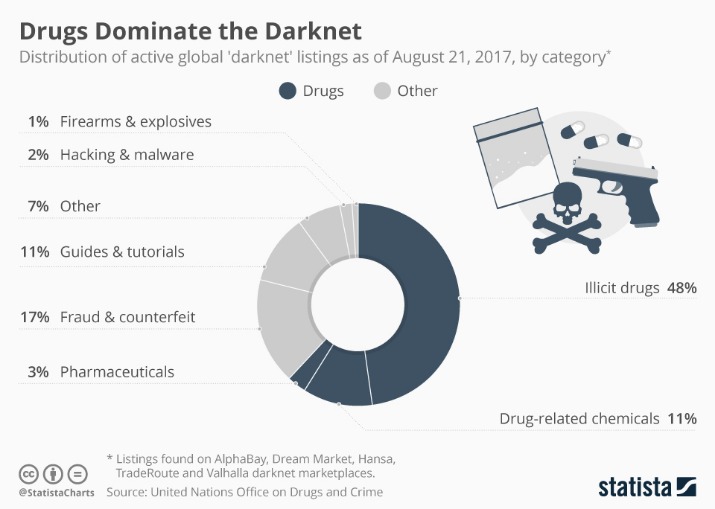
Additionally, it’s crucial to exercise caution when clicking on darknet links, even if they appear legitimate. Always verify sources before visiting unfamiliar sites, as malicious links could lead to phishing schemes, malware downloads, or other cyber threats. Employing security plugins and active malware protection can add an extra layer of defense against potential infections.
When navigating darknet sites, avoid sharing personal information or engaging in transactions that could compromise your safety. Encryption tools and virtual private networks can help obscure your activity, reducing the likelihood of data interception or identification. Regularly reviewing security settings and practicing good digital hygiene are key to mitigating risks associated with darknet links.
In summary, safe navigation of darknet links relies on a combination of anonymity tools, vigilant browsing habits, and robust security measures. By following these best practices, users can explore the dark web more securely while minimizing exposure to threats.
Using Sandboxed Environments to Access Darknet Links
Accessing darknet links requires careful attention to security considerations to protect against potential threats and maintain online safety. The dark web often contains unregulated content that can pose significant risks, including malicious software, scams, and illegal activities. Therefore, approaching darknet links with caution is essential for anyone exploring this part of the internet. Implementing security measures can help mitigate exposure to harmful content and safeguard your devices and personal information.
One of the most effective methods for securely accessing darknet links is to use a sandboxed environment. A sandbox isolates the browsing session from your main system, creating a protected space where potential threats are contained and cannot affect other programs or data. This approach minimizes risks associated with malware or viruses that may be encountered when visiting hidden or untrusted sites like darknet links.
When using sandboxed environments for visiting darknet links, it is crucial to ensure that the sandbox tools are up to date and properly configured. Regularly updating security software and employing strong, unique passwords further enhances protection. Additionally, avoid downloading or opening suspicious files from darknet links, as these are common vectors for malicious threats.
Overall, maintaining security awareness and employing sandboxing techniques are vital steps when accessing darknet links. These measures help maintain privacy, prevent unauthorized access, and mitigate the risks inherent in engaging with less regulated internet spaces. By taking these precautions, users can explore the dark web more safely and responsibly.
Analyzing Darknet Links Safely
Analyzing darknet links safely is essential for anyone exploring this hidden part of the internet. Darknet links often lead to websites that host sensitive or illegal content, making it crucial to approach them with caution. Proper analysis can help identify potential risks and protect your online security. For example, accessing darknet links requires a secure environment and specialized tools to ensure safety. Understanding how to evaluate these links is vital for researchers, cybersecurity professionals, and investigative journalists working to uncover illicit activities without exposing themselves to harm.
Utilizing Virtual Machines and Sandbox Browsers
Analyzing darknet links can pose significant cybersecurity risks, as these links often lead to illegal or malicious content. To minimize exposure to harmful material, it is essential to adopt safe investigative practices such as utilizing virtual machines and sandbox browsers. Virtual machines create an isolated environment that prevents any potential malware from affecting the host system, allowing analysts to explore and examine darknet links securely. By running an entire operating system within a virtual machine, users can experiment with suspicious links — including those found on darknet forums or marketplaces — without risking their primary device’s security.
Sandbox browsers further enhance safety by providing a controlled browsing environment that restricts malicious scripts and isolates browsing sessions from other system components. These tools enable analysts to access darknet links, such as those leading to hidden marketplace pages or forums, while preventing malware from spreading or data from leaking. Employing these methods ensures that any malicious activity remains contained, reducing the likelihood of infection or data compromise. Properly analyzing darknet links with these secure tools is a crucial step in cybersecurity investigations, helping researchers understand threats while maintaining system integrity and personal safety.
Tools for Monitoring Darknet Link Activity
Analyzing darknet links safely is crucial for cybersecurity professionals and researchers aiming to understand illicit activities without compromising their own security. Darknet links often lead to hidden marketplaces, forums, or release sites that can carry significant risks, including exposure to malware or legal issues. To approach such analysis responsibly, it is essential to employ specialized tools and techniques designed to minimize danger while collecting the necessary intelligence.
One effective method involves using virtualized environments or isolated systems that prevent any potential malware from spreading to primary networks. These sandbox environments allow analysts to investigate darknet links without risking contamination of operational infrastructure. Additionally, utilizing tools such as proxy servers, anonymity networks, and VPNs can help mask the origin of the analysis activities, further safeguarding the analyst’s identity and location.
Several monitoring tools are available to keep track of darknet link activity and detect malicious patterns. Network traffic analyzers and intrusion detection systems can identify unusual data flows or unauthorized access attempts associated with darknet links. Automated crawling and scraping tools, when configured with strict safety protocols, can also gather intelligence on darknet sites, keeping the process secure by limiting exposure to harmful content. Regular updates and threat intelligence feeds enhance the capability to recognize emerging threats linked to darknet activity.
- Once you close the browser sandbox, the virtual machine gets destroyed together with all files and running processes.
- Although it is not the largest index on the Web, VL pages are widely recognized.
- They are located in Europe, where privacy laws are among the strictest in the world.
- An online browser sandbox, also known as an online URL sandbox, lets you securely and safely open a website that you don’t trust in a browser that runs in an isolated environment outside of your network.
By combining these strategies with diligent adherence to cybersecurity best practices, analysts can safely explore darknet links such as darknet links to uncover illicit transactions or gather evidence for investigations. The key lies in employing robust protective measures, maintaining a cautious approach, and continuously updating security protocols to stay ahead of evolving cyber threats related to the dark web environments.
Detecting Malicious Content in Darknet Links

Analyzing darknet links safely and detecting malicious content is a critical task for cybersecurity professionals and users exploring the hidden layers of the internet. The darknet hosts a variety of content, some of which can be highly dangerous or illegal. Therefore, understanding how to approach these links responsibly is essential to protect oneself from potential threats such as malware, scams, or other malicious activities.
To analyze darknet links securely, it is important to follow best practices that minimize risk. First, always use a dedicated and isolated environment such as a virtual machine or a sandboxed browser. This setup prevents malicious payloads from affecting your primary system. Additionally, employing robust security tools like antivirus software and network monitoring tools can help detect and block potential threats stemming from darknet links.
Detecting malicious content involves careful examination and verification. Tools that analyze link reputation, perform URL filtering, and check for suspicious patterns are valuable in identifying dangerous sites. It is also recommended to avoid directly clicking on darknet links; instead, utilize intermediate services that preview or scan links for malicious code without exposing your device.
When working with darknet links, be cautious of signs indicating harmful content, such as unusual URL structures, frequent redirects, or unexpected pop-ups. Utilizing security resources and analyzing the link’s behavior before interacting can help prevent infections or data breaches. Remember that the darknet can harbor illegal activities, so vigilance and adherence to legal boundaries are always advised when engaging with its content.
- Use a dedicated, isolated environment such as a virtual machine for analysis.
- Employ reputable link reputation and malware scanning tools prior to visiting darknet links.
- Avoid clicking on suspicious links directly; instead, use link preview services for safer inspection.
- Monitor network activity during analysis to identify unusual behavior or data exfiltration.
- Stay informed about emerging threats and known malicious patterns associated with darknet content.
Legal and Ethical Implications
The darknet presents a complex landscape where legal and ethical considerations play a significant role in navigating its depths. Accessing or sharing darknet links can involve dealing with content that may be illegal or morally questionable, raising serious concerns about responsibility and conduct. It is crucial to understand the potential consequences and legal implications of engaging with such links, especially considering the anonymity and lack of regulation inherent to the darknet. For example, exploring sites like darknet links can expose users to various risks, including involvement in illegal activities, which can have far-reaching legal consequences. Awareness and cautious handling of darknet content are essential to ensure ethical engagement and avoid legal pitfalls. Staying informed about the boundaries and responsibilities associated with darknet links helps maintain a responsible approach in this clandestine part of the internet.
Legal Risks of Accessing Darknet Content
Accessing darknet links raises significant legal and ethical considerations that individuals should carefully evaluate before engaging with such content. The darknet, often associated with anonymous browsing and hidden marketplaces, contains a mix of lawful and unlawful material. Engaging with illegal content found through darknet links can expose users to serious legal risks, including criminal charges such as conspiracy, possession of illegal substances, or involvement in illicit trade. Many jurisdictions have strict laws against accessing or possessing certain types of content, and law enforcement agencies actively monitor illegal activities on the darknet.
Furthermore, accessing darknet links may also pose ethical dilemmas. The anonymity provided by the darknet can facilitate activities that harm others, such as trafficking, hacking, or distribution of illegal substances. Users must consider the moral implications of their actions and the potential impact on victims or society at large. It is important to recognize that simply browsing certain darknet sites may be viewed as complicity or support for illegal activities, which can have legal consequences.
Additionally, the security risks associated with accessing darknet links are notable. Users might encounter malicious software, scams, or seize opportunities for identity theft. Law enforcement agencies increasingly employ digital forensics techniques to trace illegal activities back to individuals, even when anonymity tools are used. Engaging with darknet links that host questionable content can unwittingly expose users to legal jeopardy and ethical complications, emphasizing the importance of maintaining compliance with local laws and ethical standards.
In summary, navigating darknet links involves understanding and respecting the legal boundaries set by authorities, alongside ethical considerations regarding the content accessed. Exercising caution and awareness can help mitigate potential legal and moral risks associated with dark web activities.
Ethical Considerations and Responsibilities
Engaging with darknet links involves navigating a complex landscape of legal and ethical considerations that demand careful attention. While the darknet provides anonymity and privacy for users, it also hosts activities that may be unlawful or ethically questionable. Understanding the responsibilities associated with accessing or sharing darknet links is crucial to ensure compliance with legal standards and uphold moral integrity.
When dealing with darknet links, individuals must be aware of the potential legal implications. Accessing or distributing content that involves illegal activities such as drug trafficking, cybercrime, or illicit marketplaces can lead to serious legal consequences. Many jurisdictions have strict laws against participating in or facilitating such activities, even if unintentionally. It is essential to educate oneself about the local laws and avoid engaging with links that could lead to illegal content or services.
Ethical considerations also play a vital role in the responsible use of darknet links. Respect for privacy, both one’s own and that of others, should guide actions. While anonymity can be a protective feature, it can also enable harmful behaviors, such as the dissemination of illegal material or exploitation. Users should assess whether their interactions align with ethical standards that prioritize safety, respect, and integrity.
Responsibilities include exercising caution when browsing or sharing darknet links. This involves verifying the legitimacy of sources, avoiding participation in malicious activities, and understanding the potential risks involved. Engaging with reputable and lawful content minimizes harm and liability, fostering a safer digital environment for all participants.
- Be aware of and adhere to the laws governing online activities in your jurisdiction.
- Recognize the ethical importance of respecting privacy and avoiding participation in illegal or harmful activities.
- Exercise caution when accessing or distributing darknet links, such as darknet links, to prevent unintentional involvement in illegal enterprises.
- Promote responsible digital behavior by verifying sources and understanding the risks associated with darknet browsing.
Compliance with Laws and Regulations
Exploring the dark web often involves accessing darknet links, which are characterized by their use of encrypted and anonymized networks. While these links can provide access to a variety of content and services, they also raise significant legal and ethical concerns. Engaging with darknet links may inadvertently involve users in activities that violate laws or infringe on ethical standards, such as the distribution of illicit goods or services. It is crucial for users to understand the importance of compliance with applicable laws and regulations when exploring these sites, as failure to do so can result in severe legal consequences.
Legal implications associated with accessing or interacting with darknet links vary by jurisdiction but generally include potential charges related to supporting illegal activities, such as drug trafficking, illegal weapons sales, or child exploitation. Law enforcement agencies have increased efforts to monitor and shut down illegal operations on the dark web, making it essential for individuals to exercise caution. Ethical considerations also come into play, especially regarding privacy, consent, and the potential harm caused by certain types of content accessible through darknet links.
To ensure lawful and ethical use of the dark web, users should be aware of the legal boundaries and respect the regulations in their respective regions. This includes refraining from participating in or endorsing illegal transactions or content. Proper research and understanding of the laws governing online activity can help prevent unintentional involvement in unlawful activities. Ultimately, responsible use of darknet links involves balancing the desire for privacy or anonymity with a firm commitment to legal and ethical standards to avoid infringing on rights or exposing oneself to legal risks.
Darknet Links and Cybersecurity
The darknet has become a shadowy frontier in the realm of cybersecurity, often associated with anonymous activity and illicit exchanges. Darknet links provide access to hidden websites that are not indexed by traditional search engines, making them difficult to monitor or regulate. While these links serve legitimate purposes such as protecting privacy and enabling free speech in oppressive regimes, they are also exploited for criminal activities. Understanding how darknet links work and their implications is essential for cybersecurity professionals aiming to identify threats and safeguard digital infrastructure.
Role in Cyber Threats and Crime
Darknet links are a crucial aspect of the hidden parts of the internet, often associated with illegal activities and illicit marketplaces. These links provide access to anonymous websites that are not indexed by traditional search engines and are typically accessed through specialized software, such as the Tor browser. While the darknet serves legitimate purposes like protecting privacy and free speech, it is also frequently exploited for cybercriminal activities.
In the realm of cybersecurity, darknet links play a significant role in the landscape of cyber threats. Cybercriminals utilize these anonymous channels to exchange stolen data, distribute malicious software, and conduct illegal transactions. The secrecy provided by darknet links complicates law enforcement efforts to trace and dismantle cybercriminal networks. These links often lead to marketplaces and forums where illegal goods and services, including hacking tools and stolen credentials, are sold.
The use of darknet links enhances criminal operations by enabling more secure and covert communication between malicious actors. This environment fosters the growth of various cyber threats, including ransomware attacks, credit card fraud, and the sale of illegal substances and weapons. Cybersecurity experts continuously monitor darknet links, aiming to uncover illegal activities and mitigate potential cyber threats before they impact individuals or organizations.
Understanding the role of darknet links in cyber threats and crime is essential for developing effective cybersecurity strategies. By analyzing these anonymous sites and the links that connect to them, authorities and cybersecurity professionals can better anticipate criminal operations and implement measures to prevent cyberattacks. Overall, darknet links represent both a tool for privacy and a challenge for cybersecurity, making awareness and vigilance critical in today’s digital landscape.
Darknet Links in Malware Distribution
Darknet links play a significant role in the realm of cybersecurity, particularly in the context of illicit activities such as malware distribution. These links serve as access points to hidden parts of the internet, often hosted on the Tor network, which provides anonymity for users and websites alike. Cybercriminals utilize darknet links to facilitate covert communication, data exchange, and the dissemination of malicious software without the risk of easy detection by law enforcement or security systems.
One of the primary uses of darknet links in malware distribution is through the creation of clandestine marketplaces and forums where malicious actors can buy and sell malware, stolen data, and hacking tools. Cybercriminals frequently rely on these hidden URLs to host malware payloads or direct victims to malicious sites, making it difficult for investigators to trace and shut down these operations. The transient nature of darknet links adds an extra layer of complexity, as they can be quickly regenerated or moved to new addresses to evade detection.
Darknet links are also exploited for command and control (C&C) servers that manage botnets and other malware networks. These links provide a resilient way for malware to communicate with its controllers, even if traditional attack vectors are monitored or blocked. By leveraging the anonymity features of the darknet, cybercriminals ensure that their operations remain protected from takedowns and legal actions, thus maintaining the integrity of their malicious infrastructure.
For cybersecurity professionals, understanding how darknet links facilitate malware activities is crucial in developing effective defense strategies. Monitoring suspicious darknet links and analyzing their traffic can provide valuable intelligence on ongoing cyber threats. Enhancing detection mechanisms and educating users about the risks associated with darknet links help mitigate the threat posed by these hidden web addresses in the distribution of malicious software.
Law Enforcement and Darknet Link Tracking
Darknet links are specialized URLs that provide access to websites hosted on the dark web, a part of the internet not indexed by standard search engines and often used for private or illicit activities. These links typically use the “.onion” domain and require specific software such as Tor to access. The nature of darknet links makes them challenging to monitor and regulate, posing significant challenges for cybersecurity professionals and law enforcement agencies alike.
In the realm of cybersecurity, darknet links are often associated with illegal activities such as illegal marketplaces, black hat forums, and illicit communication channels. Monitoring these links is critical for identifying potential threats, tracking criminal operations, and preventing cybercriminal activities. Specialized tools and techniques are employed by cybersecurity teams to analyze darknet links and gather intelligence without exposing their own systems to harm.
Law enforcement agencies play a crucial role in the fight against cybercrime facilitated through darknet links. They employ advanced cyber investigations, ongoing surveillance, and undercover operations to track and dismantle illegal networks. One of the key strategies involves tracking darknet links to map out entire criminal ecosystems, identify key players, and seize illicit assets. Techniques such as network analysis, digital forensics, and cooperation with international agencies enhance their ability to penetrate these covert sites.
Darknet link tracking is an essential component of cybersecurity efforts that seeks to decode the complex web of hidden online activities. By analyzing patterns associated with certain darknet links, authorities can predict potential threats, disrupt cybercriminal operations, and develop robust legal and technical frameworks to combat online crimes. Overall, understanding and monitoring darknet links are vital for maintaining cybersecurity and ensuring the integrity of digital ecosystems.
Future Trends and Challenges
The landscape of the digital world is constantly evolving, presenting both exciting opportunities and significant challenges. With the rise of darknet links, understanding the future trends and associated risks becomes increasingly important. As technologies advance, the accessibility and use of darknet sites are expected to grow, raising concerns about security, privacy, and illegal activities. Navigating this complex environment requires awareness of emerging threats and the development of effective countermeasures.
Evolving Structures of Darknet Links
The landscape of darknet links is continuously evolving, presenting both new opportunities and significant challenges for users and security professionals alike. As technology advances, so do the methods employed to conceal and access these hidden parts of the internet. Darknet links are increasingly adopting complex and dynamic structures, making detection and analysis more difficult than ever before. This evolution is driven by the need for enhanced privacy, anonymity, and security, but also raises concerns about illegal activities and cyber threats.
One prominent future trend is the development of more sophisticated link obfuscation techniques. These methods aim to conceal the true destination and nature of darknet links, complicating efforts to monitor and regulate malicious content. Additionally, the rise of encrypted and decentralized hosting solutions contributes to the resilient nature of darknet sites, often creating links that are harder to track and shut down. As a result, cybersecurity teams must adapt by employing advanced tools such as machine learning algorithms and behavioral analysis to uncover and analyze these elusive links.
Another challenge lies in the dynamic restructuring of darknet links. Many operators regularly change link configurations or migrate to new platforms to evade detection and takedown efforts. This fluidity requires constant vigilance and updated strategies from law enforcement and cybersecurity experts. Furthermore, with the proliferation of anonymous communication channels, darknet links are often embedded within encrypted messaging apps or hidden within legitimate-looking websites, adding layers of complexity to efforts aimed at understanding their structures and functions.
Looking ahead, the ongoing convergence of darknet activities with mainstream internet infrastructure could lead to new hybrid models of link structures, blending open access with invisible networks. This integration may complicate legal and technical responses, necessitating international cooperation and innovative approaches to ensure cybersecurity and public safety. As darknet link structures continue to evolve, staying ahead of these developments remains critical for maintaining a secure digital environment.
Technologies for Safer Navigation
As technology advances, the landscape of cybersecurity and online navigation faces both exciting opportunities and significant challenges. One area of concern is the use of darknet links, which often serve as gateways to illicit activities and can complicate efforts to maintain a safe and secure digital environment. Future trends indicate that developing more sophisticated tools for detecting and monitoring these links will be crucial in preventing cyber threats and illegal transactions.
Emerging technologies such as artificial intelligence and machine learning are increasingly being utilized to identify suspicious patterns associated with darknet links and related activities. These tools can analyze vast amounts of data quickly, helping security professionals anticipate and mitigate potential risks before they escalate. However, the rise of encrypted and anonymized networks also presents challenges, as malicious actors leverage these technologies to obscure their tracks, making it harder to track darknet links and ensure safe navigation for users.
In addition to technical solutions, there is a growing emphasis on international cooperation and policy development to address the complex issues surrounding darknets. Efforts include reinforcing cybersecurity laws, promoting responsible online behavior, and increasing awareness of the dangers associated with accessing or sharing darknet links. As these challenges persist, the ongoing evolution of secure navigation technologies—such as upgraded encryption methods and decentralized verification systems—will be key to fostering a safer digital ecosystem.
Innovators are also exploring new approaches like blockchain-based verification to authenticate the legitimacy of online content and links, including those that may appear on the darknet. These innovations aim to create transparent and tamper-proof systems, reducing the risks of scams and illicit activities. Despite these advancements, continuous vigilance and adaptation remain essential to combat the ever-changing tactics used by those exploiting darknet links for harmful purposes.
Emerging Risks in Darknet Link Exploration
The landscape of darknet link exploration is rapidly evolving, presenting both exciting opportunities and significant challenges. As the darknet continues to grow as a hub for discreet communication and illicit activities, understanding emerging risks and future trends is crucial for cybersecurity professionals, law enforcement agencies, and researchers. The increasing sophistication of darknet links, combined with advancing anonymization technologies, is reshaping how these hidden networks are accessed and monitored.
One of the key future trends involves the development of more resilient anonymization tools that enable users to access darknet links with greater privacy and security. This evolution complicates efforts to trace illicit activities, making traditional detection methods less effective. Additionally, the proliferation of marketplaces, forums, and hidden services hosting darknet links necessitates more advanced detection techniques, such as machine learning algorithms and behavioral analytics to identify suspicious link structures and patterns.
Despite technological advancements, emerging risks continue to threaten cybersecurity and law enforcement efforts. The use of darknet links for illegal activities such as drug trafficking, weapons sales, and cybercrime is intensifying. The encryption and decentralized nature of these links make it difficult to shut down entire networks or track perpetrators effectively. Moreover, the rise of cryptocurrencies as a payment method amplifies the challenge of monitoring illicit transactions associated with darknet links.
- Increasingly sophisticated darknet marketplaces that operate through encrypted and hidden links
- Enhanced anonymity tools that make surveillance and link tracking more challenging
- Emergence of new, undetectable forms of malware that exploit darknet links for distribution
- Potential use of darknet links for coordinated cyberattacks and propaganda campaigns
- Legal and ethical concerns surrounding surveillance and monitoring of private darknet communications
In conclusion, the future of darknet link exploration is marked by technological innovation and heightened risks. While new tools may improve detection capabilities, cybercriminals continuously adapt to evade authorities, complicating efforts to combat illegal activities. Ongoing research and collaboration between cybersecurity experts, law enforcement, and policymakers are essential to address these emerging challenges effectively.