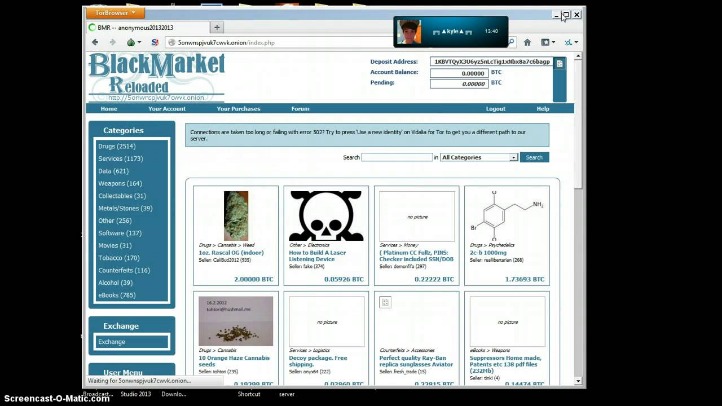
Understanding the Dark Market Onion Ecosystem
The dark market onion ecosystem represents a complex and often concealed segment of the internet where illegal goods and services are traded anonymously. Operating within the hidden layers of the dark web, these markets utilize encryption and specialized browsers to maintain user privacy and security. Understanding how these onion-based marketplaces function is crucial for gaining insight into their impact on cybersecurity, law enforcement, and global commerce. For instance, some marketplaces facilitate the exchange of contraband, stolen data, and counterfeit documents, making them a focal point for authorities and cybersecurity experts alike. One notable example of a dark market onion is dark market onion. Exploring these platforms reveals the clandestine economy thriving beneath the surface of the conventional internet.
Definition and Role of Onion Markets
The dark market onion ecosystem refers to a concealed online environment where numerous illicit activities take place, primarily utilizing anonymous communication channels. These markets operate on the Tor network, commonly known as the “onion” network, which provides users with enhanced privacy and encryption to conceal their identities and locations. Dark markets on this network facilitate the buying and selling of illegal goods and services, including drugs, counterfeit documents, stolen data, and hacking tools. The role of onion markets is pivotal in enabling illicit trade by providing a secure platform that minimizes the risks of detection and law enforcement intervention. These markets typically feature escrow services, user reviews, and anonymous payment options to maintain confidentiality and trust among participants. Understanding the onion ecosystem is crucial for cybersecurity professionals and law enforcement agencies aiming to combat illegal activities thriving within these clandestine online spaces. The persistent rise of dark market onion platforms underscores the ongoing challenges in regulating and policing hidden online economies that operate outside the scope of conventional internet oversight.
Structure and Functionality of Onion Sites
The dark market onion ecosystem represents a hidden segment of the internet that operates beyond the reach of traditional search engines and standard online surveillance. These sites are hosted on the Tor network, which provides anonymity for both operators and users. The structure of onion sites is designed to ensure security and privacy, often featuring layered encryption and complex access protocols to prevent unauthorized detection and shutdown. The functionality of these sites varies widely, ranging from illicit trading platforms to forums dedicated to clandestine activities.
Onion sites are characterized by their distinctive “.onion” domain suffix, which signifies their operation within the Tor network. These sites are accessible only through specialized browsers that anonymize user activity and conceal IP addresses, making tracking difficult. The architecture of the dark market onion is often built around decentralized or semi-decentralized frameworks to reduce vulnerabilities. Features such as escrow services, reputation systems, and encrypted communication channels are commonplace to facilitate safe transactions and preserve user anonymity.
The dark market onion ecosystem relies heavily on trust established through reputation and cryptographic proofs, as direct oversight and regulation are virtually nonexistent. This environment fosters an array of illegal and gray-market activities, including drug trafficking, weapon sales, and stolen data exchanges. Despite the risks and illegality, the onion market continues to thrive due to its resilient structure, effective anonymity measures, and the persistent demand for illicit goods and services.
Comparison with Clear Web Marketplaces
The dark market onion ecosystem is a clandestine segment of the internet that operates on the Tor network, providing a platform for illegal trade and activities that are hidden from traditional web searches and oversight. These markets are characterized by their anonymous nature, relying on encryption and decentralized operations to safeguard both buyers and vendors. Unlike conventional online marketplaces, dark market onion sites often require specialized access and are not indexed by standard search engines, making them inherently secretive and difficult to monitor.
When comparing the dark market onion ecosystem to clear web marketplaces, several fundamental differences emerge. Clear web marketplaces are accessible through standard web browsers and are indexed extensively by search engines, providing transparency, regulation, and ease of use. These platforms typically adhere to legal standards and are designed for legitimate commercial activities, ensuring consumer protection and security protocols. In contrast, the dark market onion spaces prioritize anonymity and operate outside the scope of regulatory oversight, often facilitating the exchange of illicit goods and services.
The anonymity features of the dark market onion sites not only protect vendors and buyers from law enforcement but also foster an environment where illegal activities can flourish without easy detection. This stark contrast highlights the risks involved in navigating such spaces, as well as the challenges authorities face in combating illegal online markets. Despite these differences, both ecosystems serve as vital marketplaces for their respective audiences, with clear web marketplaces dominating legitimate commerce and dark market onion sites catering to clandestine interests.
Understanding this dynamic is crucial for comprehending the broader landscape of digital trade and the ongoing efforts to regulate and secure online transactions. The dark market onion ecosystem remains a complex and evolving environment, distinct from the transparent and regulated nature of clear web marketplaces.
Technical Foundations of Dark Market Onion Sites
The technical foundations of dark market onion sites are complex and involve a combination of specialized tools and secure protocols that ensure anonymity and privacy. These sites operate on the Tor network, which anonymizes the location and identity of users and vendors, making law enforcement efforts significantly more challenging. Understanding how these sites are structured, maintained, and accessed provides insight into their resilience and ongoing evolution. For those interested in exploring these networks further, there are various dark market onion platforms that exemplify the technical intricacies involved in creating and sustaining such clandestine marketplaces.

Use of .onion Domains and Tor Network
The dark market onion sites operate within a hidden part of the internet, utilizing the unique capabilities of the Tor network to maintain user anonymity and secure communication. These sites often rely on .onion domains, which are special types of addresses accessible only through the Tor browser, providing an additional layer of privacy and security. The use of .onion domains is fundamental to the existence of dark markets, as they help conceal the physical location of servers and protect both vendors and buyers from surveillance and legal actions.
The Tor network, short for The Onion Router, is a decentralized system that routes internet traffic through multiple volunteer-run servers or relays. This process encrypts data in multiple layers, similar to layers of an onion, making it extremely difficult to trace the origin or destination of the traffic. As a result, activities carried out on dark market onion sites are challenging to monitor, providing a robust environment for illicit trading and other hidden activities.
Accessing these dark market onion sites requires specialized software such as the Tor browser, which is configured to connect to the Tor network by default. Once connected, users can securely browse .onion sites, which are not indexed by traditional search engines and are intentionally hidden from standard internet visibility. This architecture ensures that both the site operators and visitors remain anonymous, thus maintaining the integrity and secrecy of activities conducted within this ecosystem.
The technical foundations of dark market onion sites combine the use of .onion domain services and the layered encryption methods of the Tor network. Together, they create a resilient environment that supports anonymous commerce and communication. While often associated with illegal activities, it’s important to recognize that this technology also serves legitimate purposes, such as protecting privacy rights and enabling free expression under oppressive regimes.
Encryption and Anonymity Technologies
Dark market onion sites operate within a complex ecosystem that relies heavily on advanced encryption and anonymity technologies to maintain user privacy and security. These platforms are typically hosted on the Tor network, which enables users to access hidden services through onion addresses, providing a higher level of anonymity compared to conventional websites. The underlying technical foundations of these sites are designed to protect both vendors and buyers from surveillance and detection, making them resilient against takedowns and investigations.
Encryption plays a vital role in securing communications and transactions within dark market onion sites. End-to-end encryption ensures that data exchanged between users and the marketplace remains confidential, preventing eavesdropping by third parties. Moreover, the use of cryptographic techniques such as SSL/TLS protocols and encrypted messaging further enhances security, safeguarding sensitive information like payment details and personal data from being exposed.
Anonymity technologies are central to the infrastructure of dark market onion sites. The Tor network anonymizes traffic by routing it through multiple relays across the globe, obscuring users’ IP addresses and making it difficult to trace their online activity. Additionally, many of these sites employ digital cash and privacy-focused cryptocurrencies to carry out transactions without revealing personal identities. Techniques like coin mixing and tumbling services are also used to enhance transaction anonymity, ensuring that exchanges cannot be linked back to specific individuals.
The combination of onion routing, encryption, and anonymous payment methods creates a resilient environment for dark market activities. These technical foundations have enabled such sites to operate covertly and persistently despite ongoing efforts to combat illicit online markets. Understanding these underlying technologies is crucial for recognizing the sophisticated security measures that underpin dark market onion sites and their continued existence in the shadowy corners of the internet.
Operational Security Measures for Sellers and Buyers
Dark market onion sites operate within a complex and clandestine digital environment that requires a comprehensive understanding of their technical foundations. These platforms are typically built on the Tor network, which provides an anonymity layer by encrypting traffic and routing it through multiple relays. This routing makes it difficult to trace user activity and locate servers hosting marketplace content. The architecture of such sites often involves robust encryption protocols, decentralized hosting, and distributed servers to enhance resilience against takedowns and surveillance.
Operational security measures are critical for both sellers and buyers participating in dark market onion sites. These measures include the consistent use of pseudonymous identities that do not reveal personal information, employing encrypted communication channels such as PGP for negotiations and transaction details, and maintaining strict control over digital footprints. Users often utilize disposable devices or virtual machines to prevent malware or tracking scripts from linking their real identities to their activities. Implementing multi-factor authentication and regularly updating security tools further reduces vulnerability to hacking or surveillance.
Additionally, understanding the importance of avoiding common pitfalls—such as revealing personal information, using unsecured connections, or engaging in careless behavior—is vital for safe operation within this environment. Both buyers and sellers should adopt layered security practices, recognize signs of malicious activity, and stay informed about emerging threats and countermeasures. These foundational technical and operational security measures serve to protect anonymity, safeguard assets, and ensure ongoing access to the dark market onion ecosystem.
Types of Goods and Services Offered
Understanding the range of goods and services available is essential when exploring the intricacies of online marketplaces, including the dark market onion. These digital environments facilitate the exchange of various products, from legal commodities to illicit items, serving diverse user needs and interests. The offerings vary widely depending on the platform and its purpose, often accommodating specialized communities and individuals seeking anonymity.
Within this realm, the dark market onion has gained notoriety for hosting a wide array of goods and services that are difficult to find through conventional channels. Participants can access everything from digital data to physical goods, often with an emphasis on privacy and security. It is important to approach such marketplaces with caution, as they involve significant legal and ethical considerations. For more detailed insights into these hidden markets, you might explore reputable resources dedicated to understanding dark market onion operations and security practices.
Illegal Substances and Drugs
The dark market onion networks are known for offering a wide variety of goods and services outside the scope of legal commerce. These marketplaces often facilitate transactions involving illegal substances and drugs, which are among the most common and concerning elements available. Buyers and sellers operate in anonymity, making it challenging for authorities to regulate or monitor these exchanges effectively. On these platforms, illegal drugs such as narcotics, stimulants, and hallucinogens are frequently traded, often with little oversight regarding quality or safety. Additionally, these markets may also feature other illegal goods and services, including counterfeit currencies, stolen data, and hacking tools. The presence of illegal substances and drugs on the dark market onion is a significant factor that raises concerns about public health and safety. Efforts to combat these activities continue as law enforcement agencies work to identify and dismantle these clandestine operations while addressing the broader issues surrounding illicit trade on the dark web. The proliferation of such illegal transactions underscores the importance of ongoing vigilance and enforcement to curb the illegal trade and protect communities from associated harms.
Stolen Data and Personal Information
The dark market onion sites are a part of the hidden corners of the internet where illicit goods and services are exchanged. These marketplaces often cater to a variety of needs, providing both goods and services that are not available through conventional channels. Understanding the types of offerings on these platforms, especially concerning stolen data and personal information, is crucial for awareness and cybersecurity purposes.
On dark market onion sites, the range of goods and services offered typically includes:
- Illegal goods such as counterfeit currencies, drugs, and weapons
- Stolen data including credit card information, login credentials, and personal identification details
- Hacking services and malware for sale or rent
- Forked or fake documents like passports and driver’s licenses
- Services for laundering money or anonymizing online activities
Among the most concerning aspects of dark market onion sites is the sale and distribution of stolen data and personal information. This data theft often involves hacking into corporate databases, phishing schemes, or exploiting vulnerabilities in digital systems. Once compromised, this information can be bought and sold across these clandestine marketplaces, fueling identity theft, financial fraud, and other cybercrimes.
Stolen data on these platforms may include social security numbers, banking details, personal addresses, and even biometric information. The proliferation of such data increases the risk for individuals and businesses alike, emphasizing the importance of robust cybersecurity measures. The dark market onion acts as a hub for these transactions, often facilitating quick, anonymous exchanges that are difficult to track or regulate.
Understanding the types of goods and services, especially the prevalence of stolen data, highlights the importance of vigilance and proactive security strategies to protect personal and organizational information from falling into the wrong hands.
Counterfeit Documents and Fake Identification
The dark market onion platforms are known for offering a wide range of goods and services that often operate outside the boundaries of legal commerce. These markets typically provide various types of goods, including illicit substances, counterfeit documents, and fake identification, catering to individuals seeking anonymity and privacy. The availability of these products makes dark market onion sites a hub for illegal transactions that evade traditional regulatory frameworks.
Among the most frequently traded items are counterfeit documents, which can range from fake passports and driver’s licenses to forged certificates and identification cards. These counterfeit items are typically used for fraudulent activities, such as identity theft, unauthorized access, or illegal migration. The quality and authenticity of these fake IDs vary, but their presence on dark market onion sites underscores the extensive gray and black markets operating online.
In addition to counterfeit documents, fake identification services are highly sought after on dark market onion platforms. These services often offer custom-made IDs tailored to the buyer’s specifications, often providing quick and discreet solutions for those needing legal or illegal identification quickly. Such services pose significant security challenges for authorities attempting to combat identity fraud and related crimes.
The digital ecosystem of dark market onion sites is characterized by their focus on security and confidentiality, making them a preferred marketplace for purchasing illegal goods and services. The proliferation of counterfeit documents and fake IDs underscores the importance of robust verification processes and law enforcement efforts to combat these illegal activities and safeguard public security.

Illegal Weapons and Firearms
The dark market onion ecosystems are known for hosting a wide range of goods and services, often operating outside the bounds of legal regulatory frameworks. These underground markets facilitate transactions that are typically prohibited or heavily regulated in traditional commerce, including various classified items and illicit services. Among the most concerning aspects of these markets are the offerings related to illegal weapons and firearms, which pose significant safety and security risks.
On dark market onion platforms, a variety of goods and services are exchanged, including:

- Illegal weapons and firearms, such as unregistered guns, assault rifles, and homemade firearms
- Illicit drugs and narcotics in various quantities and strains
- Counterfeit identification documents and financial credentials
- Stolen digital data, such as credit card information and hacking tools
- Unlicensed pharmaceuticals and counterfeit medicines
- Unauthorized hacking services and cyberattack tools
- Black-market electronics and stolen gadgets
- Various counterfeit luxury items, such as designer clothes and accessories
The presence of illegal weapons and firearms on dark market onion sites raises serious concerns for law enforcement agencies worldwide. These platforms often facilitate the sale of untraceable and unregulated arms, making it difficult to monitor or control the proliferation of dangerous weapons. Such transactions increase the risk of violence, terrorism, and criminal activities. Consequently, efforts to combat illicit sales on dark markets are ongoing, with authorities continuously working to track and shut down these illicit operations to ensure increased safety and security for the public.
Other Illicit Services and Goods
The dark market onion is a segment of the clandestine online marketplace where various goods and services are exchanged outside the bounds of legal regulation. These markets operate using encrypted networks to ensure anonymity for both buyers and sellers. The range of offerings on dark market onion sites is vast, including both legitimate and illicit items. Understanding the types of goods and services available, as well as the illicit activities conducted, is crucial for awareness and security considerations.
Types of goods and services offered on dark market onion sites vary widely. They often include legal items such as digital goods, software, and manuals, but primarily focus on illicit products. Common categories include:
- Drugs and controlled substances
- Stolen data, such as credit card information and login credentials
- Counterfeit documents and currency
- Illegal firearms and weapons
- Unlawful intellectual property products, like pirated software and media
- Dark web hacking services and malware
- Adult content that violates legal boundaries
- Anonymous pharmaceutical products
In addition to physical goods, the dark market onion hosts a variety of illicit services. These services often involve illegal activities and pose significant risks:
- Money laundering services
- Hitman or contract killing arrangements
- Fraud and scam facilitation
- Cyberattack and hacking assistance
- Unlawful transportation or smuggling services
- Counterfeit document creation and distribution
- Illegal surveillance or bugging services
The realm of the dark market onion also includes other illicit goods that are commonly associated with unlawful activities. These include stolen intellectual property, exotic animals, and unregulated pharmaceuticals that bypass safety standards. It is important to recognize that while some transactions on dark market onion sites are intended for lawful purposes, a significant proportion involves illegal activities that can have serious legal and ethical repercussions.
Marketplace Dynamics and User Engagement
Marketplace dynamics and user engagement are critical factors shaping online commerce, especially within specialized environments like the dark market onion. These platforms operate in a complex ecosystem where trust, anonymity, and transaction security play pivotal roles in attracting and retaining users. Understanding how users interact with these marketplaces and what drives their engagement can reveal important insights into the evolving nature of illicit online activities. The dark market onion network, known for its anonymity-driven transactions, exemplifies these unique marketplace dynamics, emphasizing the importance of secure and reliable channels for buyers and sellers alike. For those interested in exploring more about these hidden marketplaces, there are numerous onion sites that serve as hubs for various transactions and services.
Registration and Verification Processes
The dynamics of online marketplaces, especially those operating on the dark web, are complex and continually evolving. These platforms typically facilitate anonymous transactions involving a variety of illicit goods and services, making them a focal point for both law enforcement and cybersecurity experts. Understanding how dark markets operate requires a deep dive into their user engagement strategies, registration procedures, and verification processes, which are designed to maintain secrecy while ensuring user trust and platform integrity.
In dark market onion sites, user engagement is crucial for ensuring ongoing activity and marketplace sustainability. These platforms often rely on reputation systems, reviews, and feedback to foster trust among users and vendors without compromising anonymity. Active participation relies heavily on maintaining a secure environment where users feel safe to conduct transactions discreetly, which is a key aspect of dark market onion sites’ operational dynamics.
Registration processes in these marketplaces are typically streamlined to encourage new users to join while maintaining strict privacy protections. Users often register with pseudonymous accounts, avoiding the use of any personally identifiable information. Some platforms may require a minimal registration step to access their services, while others implement more elaborate onboarding procedures to restrict access to verified vendors or trusted members.
Verification processes in dark market onion platforms are designed to balance access control with anonymity. Vendors, in particular, may undergo strict verification protocols, including proof of product authenticity, reputation checks, and sometimes even encryption keys to authenticate their identities. Buyers usually rely on feedback scores and transaction histories to assess trustworthiness, as official identity verification is often intentionally minimal or non-existent to preserve privacy.
Understanding the operational frameworks of dark market onion sites highlights the importance of security and trust mechanisms that underpin their ongoing activity. Despite the illegal nature of many offerings, these marketplaces exhibit a sophisticated approach to user engagement, registration, and verification, ensuring that participants can operate with a high degree of anonymity while managing risks effectively.
Listing and Bidding Procedures
Dark markets on the onion network operate as clandestine online marketplaces where users can buy and sell a wide array of goods and services beyond the reach of traditional regulatory frameworks. These platforms are characterized by complex marketplace dynamics and high levels of user engagement, driven by the desire for anonymity and access to illegal or restricted commodities.
In such marketplaces, listing and bidding procedures are designed to prioritize user confidentiality and security. Sellers typically create listings that describe their offerings in detail, often employing encryption and secure communication channels to maintain privacy. Bidders then review these listings and place bids securely, frequently using pseudonymous accounts to avoid identification.
Marketplace dynamics are influenced by various factors such as the reputation scores of users, feedback systems, and escrow services that ensure transaction security. A robust review and rating process encourages trustworthy participation and discourages fraudulent activities, which are prevalent concerns on dark markets like dark market onion. User engagement is further intensified by the community aspects of these platforms, including forums and chat features that allow buyers and sellers to communicate discreetly.
- Market listings are regularly updated to reflect current availability and pricing, ensuring users have access to accurate information.
- Bidding procedures typically involve setting maximum bid limits, with automated bidding systems often used to compete effectively without revealing bid amounts directly.
- Escrow services secure transactions by holding funds until both parties fulfill their contractual obligations, reducing the risk of scams.
- Feedback mechanisms allow participants to rate their experience, influencing the trustworthiness of sellers and overall marketplace reliability.
- Anonymity protocols ensure that the identities of users remain protected throughout the transaction process, fostering a safer environment for trading illicit or sensitive goods.
Overall, the intricate interplay of marketplace dynamics and user engagement strategies on onion markets creates a unique ecosystem that emphasizes security, trust, and discretion—key factors that sustain these anonymous trading platforms, including the dark market onion.
Payment Methods and Cryptocurrency Use
The landscape of dark markets on the onion network is constantly evolving, driven by shifting marketplace dynamics and user engagement strategies. These hidden marketplaces operate outside the conventional web, often facilitating anonymous trading of various goods and services. Understanding the underlying factors that influence user participation and transaction methods is crucial for comprehending the stability and growth of these platforms.
Momentum within these marketplaces heavily relies on the diversity of payment options available to users. Traditional methods like bank transfers or credit cards are often limited due to the need for verification, prompting many to adopt alternative payment methods that prioritize anonymity. Cryptocurrency use, especially Bitcoin and other privacy-focused coins, is prevalent in dark market onion transactions, providing pseudonymity and security for buyers and sellers alike. The integration of cryptocurrencies has significantly contributed to the ease and rapidity of transactions, encouraging increased user engagement and facilitating a broader user base.
User engagement in these marketplaces is also influenced by the robustness of the platform’s features, security measures, and community trust. As competition intensifies, operators continuously innovate to enhance user experience, which includes streamlined interfaces, reputation systems, and escrow services to ensure transaction security. The success and longevity of a dark market onion depend on maintaining user confidence while managing the inherent risks associated with anonymous trading.
Overall, the dynamic interplay of marketplace operations, diverse payment methods, and the widespread adoption of cryptocurrencies underpin the resilient growth of dark markets on the onion network. These factors collectively shape user behavior, transaction flows, and the ongoing evolution of these clandestine digital economies.
Feedback and Reputation Systems
Dark market onion platforms have emerged as clandestine marketplaces that operate within the deep web, leveraging encryption and anonymity to facilitate transactions outside traditional financial systems. These markets thrive on the principles of decentralization and user autonomy, creating a unique ecosystem where buyers and sellers interact in a largely unregulated environment. Understanding the dynamics of these markets involves examining how user engagement, feedback, and reputation systems function to sustain trust among participants.
In dark market onion communities, user engagement is often driven by the promise of privacy and security, attracting individuals seeking goods and services not accessible through conventional channels. This engagement is reinforced through interactive forums, direct messaging, and review systems, which serve as critical components for establishing credibility. Because anonymity is paramount, reputation systems play a vital role in motivating honest participation and deterring malicious activity. Users often leave detailed feedback and ratings after transactions, forming a decentralized reputation system that influences future interactions.
Feedback and reputation mechanisms in these markets are designed to create a self-regulating environment, where trustworthy vendors can build a solid standing while dishonest actors face consequences such as negative reviews or isolation. This transparent yet opaque interaction fosters a sense of accountability, encouraging vendors to maintain quality and security standards. Despite operating in a largely unregulated space, the efficacy of these reputation systems is essential for market survival, as they help mitigate fraud and build community trust.
Overall, the success of dark market onion platforms depends on intricate marketplace dynamics that balance user engagement with robust feedback and reputation systems. These components are fundamental to establishing a functioning underground economy where participants can transact with a relative degree of confidence amidst the inherent risks of the environment.
Law Enforcement Challenges and Actions
Law enforcement agencies around the world face increasing challenges in tackling illegal activities conducted on dark markets, particularly on the elusive onion networks. These hidden marketplaces facilitate the exchange of illicit goods, including weapons, drugs, and counterfeit documents, often operating beyond the reach of traditional legal frameworks. To combat these threats, authorities are employing advanced investigative techniques and international collaboration. One example of ongoing efforts involves monitoring the dark market onion sites to identify transactional patterns and disrupt illegal operations. Accessing specialized resources and encrypted channels, such as via onion addresses like dark market onion, enables investigators to better understand the scope of illicit activity and develop effective strategies for enforcement.
Detection and Monitoring of Onion Markets
Dark markets operating on the onion network pose significant challenges for law enforcement agencies worldwide. These clandestine marketplaces facilitate the exchange of illegal goods and services, often involving narcotics, weapons, stolen data, and other illicit commodities. Due to the encrypted and anonymous nature of the onion network, tracking and monitoring these markets require advanced technological strategies and coordinated efforts across multiple jurisdictions. Law enforcement agencies continually develop sophisticated tools and techniques to detect and dismantle such illegal operations, aiming to reduce their impact on public safety and security.
Detection of onion markets involves analyzing various digital footprints and behavioral patterns associated with illicit activities. Agencies employ cyber intelligence tactics, including monitoring darknet forums, user activities, and transaction patterns. The use of specialized software allows investigators to identify potential marketplaces and link activities to specific users or vendors. Additionally, techniques like undercover operations, infiltration, and information sharing between countries are crucial in uncovering hidden marketplaces.
Monitoring these dark markets requires continuous surveillance and adaptation to evolving tactics used by vendors and administrators. Automated algorithms help flag suspicious transactions, emerging markets, or new patterns of trade. Metadata analysis and blockchain tracking can be employed to trace monetary flows, even when transactions are pseudonymous. Despite these efforts, the inherent anonymity of the onion network makes comprehensive monitoring a complex and ongoing challenge for authorities.
To counter the proliferation of illegal activities on the dark market onion, law enforcement agencies collaborate internationally to share intelligence and resources. Such joint operations aim to disrupt vendor networks, seize assets, and dismantle entire marketplaces. Ongoing innovation in detection technologies and international cooperation remain vital in addressing the persistent challenges posed by these clandestine digital ecosystems.
Seizures and Legal Cases
Dark markets operating on the onion network present unique challenges for law enforcement agencies aiming to combat illegal activities online. These clandestine marketplaces facilitate the exchange of illicit goods and services, often utilizing anonymizing technologies to hide user identities and transaction locations. As a result, traditional investigative methods become less effective, requiring specialized actions to track and dismantle these operations.
- Before it was shut down in 2013, Silk Road was the most popular darknet market.
- Stakeholders, from law enforcement to market operators, will need to continuously adapt to the evolving environment.
- Users could exchange funds online without sharing credit card numbers or other identifying information.
- Meanwhile be on the lookout for phishing or copycats, if it’s not signed by us it’s not us.
- Regularly inspect your onions, removing any that start to soften or show signs of mold.
Law enforcement agencies employ a variety of actions to address the threats posed by dark markets. These include covert infiltration, cyber forensics, and international cooperation to identify key players and disrupt their networks. Seizures of digital assets, servers, and relevant hardware are common measures taken to gather evidence and weaken the infrastructure supporting these illicit marketplaces. Additionally, targeted legal cases aim to bring offenders to justice, often involving complex litigation that spans multiple jurisdictions.
Legal cases related to dark markets on the onion network typically involve charges such as conspiracy, money laundering, and distribution of illegal substances or counterfeit items. Prosecutors rely on digital forensics and undercover operations to build robust cases. Successfully prosecuting individuals involved in these activities not only removes specific threats but also discourages other potential offenders from engaging in such illicit commerce.
Efforts to combat dark markets must continually evolve in response to the rapid technological advances and new anonymization techniques employed by offenders. Coordinated international initiatives, combined with technological innovation, are essential to effectively counter the criminal activities facilitated by these hidden online marketplaces.
Technological Countermeasures and Challenges
The dark market onion networks present a complex and evolving landscape for law enforcement agencies worldwide. These clandestine marketplaces facilitate the exchange of illicit goods and services, often exploiting the anonymity of the Tor network and cryptocurrency transactions to evade detection. Tackling these illegal activities requires a nuanced combination of technological tools and strategic operations.
Law enforcement agencies face numerous challenges when attempting to monitor and shut down illegal activities on the dark market onion sites. The primary obstacle is maintaining user anonymity while conducting investigations. Criminals leverage encryption techniques, VPNs, and anonymizing technologies to mask their identities and locations, making traditional surveillance methods less effective. Additionally, the decentralized nature of these marketplaces, with frequently changing addresses and operational models, hampers efforts to track and dismantle them efficiently.
In response to these challenges, authorities are deploying advanced technological countermeasures. These include network analysis tools to identify patterns of activity, digital forensics to analyze seized data, and undercover operations to infiltrate these markets. Furthermore, collaborations across international jurisdictions help coordinate efforts and share intelligence. Cryptocurrency tracing techniques have also improved, enabling law enforcement to follow the money and identify key players behind dark market onion sites.
Despite these advancements, dark market onion sites continue to evolve, employing anti-detection strategies such as decentralized hosting and multi-layered encryption. This ongoing cat-and-mouse game makes it essential for law enforcement to stay updated with emerging technologies and adapt their tactics continuously. Combating illicit activities on the dark market onion remains a persistent challenge requiring a balanced approach that combines technology, legal frameworks, and international cooperation.
Risks and Rewards for Participants
Participating in dark markets on the onion network involves a complex balance of potential risks and rewards. Individuals engaging with these hidden marketplaces often seek access to goods and services that are unavailable through traditional channels, promising lucrative opportunities. However, the illicit nature of these markets also exposes participants to significant dangers, such as legal repercussions, scams, and security breaches. It is crucial for anyone considering involvement to weigh these factors carefully, understanding that while the rewards can be substantial, the risks are equally high. For those exploring this underground world, learning about different marketplaces, such as dark market onion, can provide valuable insights into the landscape and safety precautions necessary to navigate it securely.
Security Vulnerabilities and Scams
The dark market onion provides a platform for a variety of illicit transactions, attracting participants seeking anonymity and access to unregulated goods and services. While engaging in such markets can offer certain benefits, it is crucial to understand the associated risks and potential rewards. Participants often value the privacy and broad selection of items that are difficult to find through traditional channels, but these advantages come with significant security concerns.
Risks and Rewards for Participants
Engaging in activities on dark market onion sites presents a complex mix of benefits and dangers. On the reward side, users benefit from increased privacy, access to diverse products, and the ability to conduct transactions without revealing personal identity. These features appeal to those seeking discretion for various reasons. However, the risks include exposure to scams, fraud, and legal repercussions. The clandestine nature of these markets makes it difficult to verify seller credibility, increasing the possibility of losing money or receiving counterfeit goods.
Additionally, participants face the threat of security vulnerabilities that can compromise their personal data or financial information. Law enforcement agencies continually target dark markets, and illicit participants risk legal prosecution if caught. The reliance on cryptocurrencies for transactions, while offering anonymity, also introduces vulnerabilities due to potential hacking or loss of digital assets.
Security Vulnerabilities and Scams
- Malware and Phishing Attacks: Dark market onion sites are frequent targets for cybercriminals who deploy malware or phishing schemes to steal user credentials or infect devices.
- User Account Compromise: Inadequate security measures can lead to user account hacking, exposing identities or financial details.
- Fake Sellers and Scams: Without regulatory oversight, many sellers may deceive buyers with counterfeit or substandard products, or fail to deliver goods after payment.
- Payment and Cryptocurrency Risks: Transactions done via cryptocurrencies are irreversible and susceptible to hacks or scams, leading to loss of funds.
- Law Enforcement Disruption: Authorities conduct operations on dark market onion sites, resulting in arrests, takedowns, and financial losses for users.
Overall, individuals participating in dark market onion activities must weigh the potential benefits of increased anonymity and access against the serious security vulnerabilities and the ever-present threat of scams. Vigilant security practices and cautious engagement can help mitigate some risks, but they cannot eliminate the inherent dangers present in these clandestine environments.
Legal Risks and Penalties
Participating in the dark market onion networks can present a complex mix of risks and rewards for individuals seeking to engage in these anonymous online environments. While some users are attracted by the potential for discreet transactions and access to illicit goods or services, it is crucial to understand the legal implications and associated penalties that accompany such activities.
One of the primary risks involves legal repercussions. Engagement in dark market onion sites often violates laws related to drug trafficking, illegal weapons, counterfeit items, or other prohibited transactions. Law enforcement agencies globally have increased efforts to monitor and shut down these networks, leading to significant legal penalties including hefty fines, criminal charges, and imprisonment. Additionally, participants can be targeted by scams, fraud, or theft, which can result in financial loss and jeopardize personal safety.
On the other hand, some users perceive rewards such as increased privacy, reduced surveillance, and access to a marketplace that bypasses traditional regulation. The decentralized and anonymous nature of onion networks can offer a sense of security for those involved in illicit activities or seeking confidential exchanges. However, these perceived benefits do not come without substantial risks, and potential participants need to carefully weigh the dangers of legal consequences and exposure to malicious actors.
Understanding the legal framework and the severe penalties associated with dark market onion activities is essential. Authorities continue to develop sophisticated methods to track and prosecute individuals involved in illegal operations within these hidden networks. Consequently, engaging in such activities involves significant risks that can outweigh any perceived rewards, emphasizing the importance of remaining compliant with applicable laws and regulations.
Privacy and Anonymity Benefits
Participating in activities within the dark market onion network involves a range of risks and rewards that users should carefully consider. While these platforms may offer access to goods and services not available through traditional channels, they also pose significant security and legal challenges.
One of the primary risks associated with dark market onion sites is the potential for encountering illegal or counterfeit products. Transactions on these platforms often operate outside the boundaries of legal oversight, which increases the likelihood of fraud, scams, or exposure to illicit activities. Users may also face dangers related to hacking, phishing, or malware attacks designed to steal personal information or funds. Additionally, law enforcement agencies continuously monitor and crack down on illicit activities, meaning participants risk legal penalties if identified.
However, engaging with the dark market onion can also offer certain rewards for users seeking privacy and anonymity. These platforms typically employ advanced encryption methods and anonymizing tools, providing a layer of protection that can shield users from surveillance and tracking. For some, this level of privacy is an essential benefit when seeking to transact securely without exposing their identity or location.
Another advantage is the capacity to access products or services that are otherwise restricted or unavailable in their region. This includes rare or banned items, making the dark market onion a resource for individuals with specific needs or interests. Nonetheless, users must weigh these benefits against the substantial risks involved, emphasizing the importance of understanding both the potential rewards and dangers before engaging in such activities.
Emerging Trends and Future Outlook
Emerging trends in the dark market onion landscape highlight a rapidly evolving environment driven by technological advancements and shifting user behaviors. As digital anonymity becomes more sophisticated, new opportunities and challenges arise for both vendors and buyers operating within these hidden marketplaces. Anticipated developments include enhanced security features, the integration of alternative cryptocurrencies, and improved methods for ensuring transaction privacy. The future outlook suggests a continued growth of dark market onion platforms, catering to the increasing demand for discreet and uncensored commerce. For those interested in understanding the current state of these clandestine networks, exploring reputable dark market onion sites can provide valuable insights into the latest trends and operational strategies.
Innovations in Anonymity and Security
Emerging trends in the realm of dark markets, particularly on the onion network, are shaping the future landscape of online anonymity and security. As technology advances, so do the methods used by both users seeking privacy and entities aiming to enhance security measures. Innovations in encryption, decentralized systems, and anonymity protocols are at the forefront of this evolution, promising to provide more robust and resilient platforms for the exchange of goods and information while maintaining user confidentiality.
One significant trend is the development of improved encryption techniques that safeguard user identities and transaction details. These advancements enable more secure communication channels, making it increasingly difficult for third parties to trace activities within dark markets on the onion network. Additionally, the implementation of decentralized architectures reduces reliance on centralized servers, thereby decreasing vulnerabilities and the risk of shutdowns or censorship.
Future outlooks indicate a continued integration of cutting-edge privacy technologies, such as zero-knowledge proofs and advanced routing protocols, which will further obscure user identities and transaction data. Innovations like these aim to strike a balance between operational transparency and user anonymity, fostering safer environments for legitimate activities while complicating illicit ones. As a result, dark markets like dark market onion platforms are likely to evolve with enhanced security features, adapting to increasing regulatory pressures and technological challenges.
Overall, the landscape of anonymity and security on the onion network is set to become more sophisticated, reflecting ongoing efforts to protect privacy rights and secure digital exchanges. Stakeholders across the spectrum will need to stay informed and adapt to these emerging innovations to navigate the future of dark market transactions securely and responsibly.
Market Evolution and New Entrants
The landscape of the dark market onion has been evolving rapidly, shaped by technological advancements and shifting seguridad landscapes. As anonymity tools and encryption methods improve, these underground markets are becoming more sophisticated and harder to trace. The future outlook suggests a continuous trajectory of innovation, where emerging trends focus on enhancing privacy and security measures to protect users and vendors alike.
Market evolution within the dark web ecosystem is driven by increasing demand for illicit goods and services, fueling the entry of new players. These new entrants often leverage cutting-edge technologies such as decentralized networks and cryptocurrency-based transactions to bypass law enforcement efforts. As a result, the dark market onion platforms are becoming more resilient, adaptable, and user-centric, offering a broader range of products and services that cater to a growing clandestine customer base.
Emerging trends indicate a shift towards more specialized niche markets, with vendors focusing on unique and high-demand categories. Additionally, there is a notable rise in reputation systems and escrow services to establish trust among anonymous participants. The integration of automation and artificial intelligence may further streamline operations, making transactions more efficient and less susceptible to detection. Overall, the evolution of the dark market onion reflects a dynamic interplay between technological innovation and ongoing legal challenges, ensuring its persistence and adaptability into the future.
Impact of Global Law Enforcement Campaigns
The dark market onion sphere continues to evolve rapidly, reflecting broader shifts in technology, security measures, and law enforcement strategies. As these anonymous marketplaces grow in complexity and scale, understanding emerging trends and their future outlook becomes essential for stakeholders across legal, security, and technological domains. The increasing sophistication of encryption and anonymity tools provides users with enhanced privacy, but also presents significant challenges for law enforcement agencies aiming to curb illegal activities. Dark market onion platforms are employing advanced techniques such as decentralized architectures and layered obfuscation to evade detection and shutdown efforts.
The impact of global law enforcement campaigns on dark markets has been profound, disrupting revenues and forcing many operators to adapt or exit. Coordinated international efforts have targeted server infrastructure, financial transactions, and user networks, leading to significant seizures and arrests. However, these campaigns often result in the emergence of newer, more resilient marketplaces that utilize cryptocurrencies and encrypted communication channels to maintain operational continuity. Looking ahead, the future of dark market onion platforms suggests a continuous cat-and-mouse game, with innovative security features, decentralized exchanges, and the growing use of privacy-centric cryptocurrencies shaping the landscape.
Technological advancements such as blockchain analysis and artificial intelligence are becoming crucial tools for investigators seeking to penetrate these hidden networks. Meanwhile, economic factors, including fluctuating cryptocurrency values and changing user preferences, influence the stability and longevity of dark markets. As global cooperation intensifies and legal frameworks adapt, there is potential for more effective dismantling of illicit operations. Nonetheless, the resilient nature of dark market onion ecosystems highlights the need for ongoing innovation, vigilance, and strategic planning among law enforcement and cybersecurity professionals to stay ahead of evolving threats.