Dark Web Marketplaces and Structures
The dark web hosts a complex and clandestine network of marketplaces that operate outside the regular internet. These dark web marketplaces are designed to facilitate anonymous transactions for a wide range of products and services, often including illicit goods. Understanding the structures of these markets is crucial to grasping how they function and remain largely hidden from law enforcement. They typically use encrypted platforms, layered security measures, and decentralized systems to evade detection. One notable example of a dark web market is accessible through specialized links, which serve as gateways for users seeking anonymous trading environments. Such sites often feature a variety of categories and listing protocols that maintain operational integrity amid ongoing security challenges.
Overview of Dark Web Marketplaces
The dark web market is a part of the internet that operates beneath the surface of the conventional web, accessible only through specialized software such as Tor. These marketplaces serve as platforms where various goods and services, often illegal or illicit, are bought and sold. Understanding their structures and how they operate is essential for grasping the complexities of the dark web environment and its impact on cybersecurity and law enforcement efforts.
Dark web marketplaces typically consist of decentralized or semi-structured networks that facilitate anonymous transactions. They use cryptographic protocols and encryption to ensure user privacy and secure communications. These platforms often feature user reviews, escrow services, and reputation systems to build trust among anonymous users. Despite these security measures, the dark web market remains a challenging space due to its association with illegal activities and constantly changing operational structures.
Common structures of dark web marketplaces include:
- Centralized Marketplaces: These are large, often multi-purpose platforms that host numerous vendors and buyers. They operate similarly to mainstream e-commerce sites but focus on illicit goods and services. These markets tend to have administrative teams overseeing the platform, managing listings, and enforcing rules.
- Decentralized Networks: These function without a single controlling authority, relying on peer-to-peer technology to facilitate transactions. Such structures are more resilient to shutdowns but pose higher challenges in regulation and law enforcement.
- Escrow and Reputation Systems: These features ensure that transactions are secure and trustworthy, despite the anonymous nature of users. Escrow services hold funds until buyers confirm receipt of goods or services, helping to reduce fraud.
The dark web market is known for its dynamic environment, with marketplaces frequently shutting down and reemerging under different names or structures to evade detection and legal actions. This continual evolution makes monitoring and regulation extraordinarily difficult. Nonetheless, understanding the educational aspects of these platforms assists in cybersecurity defenses and law enforcement interventions aimed at disrupting illegal activities.
Main Features of Dark Web Marketplaces
Dark web marketplaces are specialized online platforms that operate on the hidden parts of the internet, accessible only through anonymous networks such as Tor. These marketplaces facilitate the exchange of a wide range of illegal goods and services, often including drugs, firearms, counterfeit documents, and hacking tools. Their structure is typically decentralized, consisting of multiple vendor shops and forums where buyers and sellers interact under pseudonymous identities. The architecture of these markets is designed to maintain user anonymity and security, making it difficult for authorities to track transactions or shut down operations.
The main features of dark web marketplaces often include encrypted communication channels, escrow services to hold funds until transactions are verified, and reputation systems to assess vendor reliability. These platforms frequently employ sophisticated security measures such as multi-signature transactions and PGP encryption to protect user identities and financial information. Additionally, dark web markets often have their own internal currencies, usually cryptocurrencies like Bitcoin, which provide further anonymity compared to traditional payment methods.
Another characteristic of dark web marketplaces is their ability to adapt quickly to law enforcement efforts. They often utilize multiple layers of moderation, community reporting systems, and decentralized hosting to ensure ongoing operation despite crackdowns. The marketplaces’ structures can vary from simple listings to complex layered networks that enhance security and anonymity for both vendors and buyers. Overall, these markets exemplify the clandestine, resilient nature of the dark web’s economic ecosystem, continuously evolving to stay ahead of detection and legal actions.
Marketplace Policies and Enforcement Practices
The dark web market represents a hidden segment of the internet where various anonymous marketplaces facilitate the exchange of goods and services outside the reach of conventional law enforcement and regulatory oversight. These marketplaces operate on overlay networks, primarily using anonymity-preserving technologies, to ensure privacy and security for both vendors and buyers. Understanding the structures of these markets is crucial to grasp how they function and how authorities attempt to regulate and disrupt illegal activities within them.
Dark web marketplaces are typically organized as decentralized or semi-decentralized platforms, often featuring multiple tiers of vendors, escrow systems, and specialized categories such as illicit drugs, stolen data, counterfeit documents, and hacking tools. These marketplaces tend to rely on cryptographic protocols and anonymizing networks to maintain user privacy, making detection and enforcement challenging. The architecture often includes robust verification processes, reputation systems, and secure communication channels to foster trust among participants in a largely unregulated environment.
Marketplace policies within the dark web are usually characterized by a lack of formal governance, with rules and norms enforced informally through reputation and community consensus. Vendors are often required to adhere to specific guidelines related to product quality, transaction procedures, and communication to maintain their standing in the community. Enforcement practices are primarily driven by the community or marketplace administrators, who may remove malicious vendors, address disputes, and implement sanctions like suspension or banning to uphold marketplace integrity.
Law enforcement agencies and cybersecurity experts continuously monitor and develop strategies to combat illegal activities centered around dark web market sites. These efforts include infiltration, stealth operations, and technological countermeasures aimed at identifying operators and disrupting illicit trades. Despite these challenges, dark web marketplaces persist, evolving in structure and security features to evade detection and continue serving as hubs for illegal transactions. Effective enforcement requires a combination of technological innovation, international cooperation, and understanding of the complex ecosystem that sustains these clandestine markets.
Market Retirement and Transition Trends
The dark web has become a complex and often clandestine ecosystem primarily driven by anonymous marketplaces and structured networks. These markets facilitate the exchange of a wide range of illicit goods and services, often operating under decentralized or semi-decentralized frameworks that make detection and shutdown challenging for authorities. Typically accessed through specialized anonymity-preserving tools, such as Tor, these marketplaces employ layered security protocols and market structures that allow vendors and buyers to connect in a relatively secure environment.
Over time, the landscape of dark web markets has evolved significantly. Many platforms face retirement or transition due to increased law enforcement activity, internal operational challenges, or technological advancements that render older systems outdated. This has led to a phenomenon where markets frequently disappear and are replaced by newer, more resilient platforms, often featuring improved security measures and user interfaces. The trend towards market transition is driven by a combination of factors including efforts to evade detection, shifts in marketplace governance, and technological innovations that enhance user anonymity and transaction security.
Furthermore, the structure of these markets commonly includes features like escrow services, vendor reputation systems, and multisignature transactions to foster trust among participants. The decentralized or semi-decentralized nature of some markets further complicates takedown efforts, allowing them to survive despite intermittent shutdowns. As part of ongoing adaptation, many marketplaces now employ more sophisticated encryption and anonymization techniques, making them more difficult to infiltrate or disable.
In response to the challenges faced by existing platforms, market owners and operators are frequently transitioning to new models that emphasize decentralization or leverage emerging technologies such as cryptocurrency innovations. These trends demonstrate a continuous cycle of market retirement and rebirth, reflecting the dynamic and resilient nature of the dark web ecosystem. Entrepreneurs visible in this space are constantly exploring ways to enhance stability, security, and user privacy, contributing to the persistent and evolving presence of dark web marketplaces.
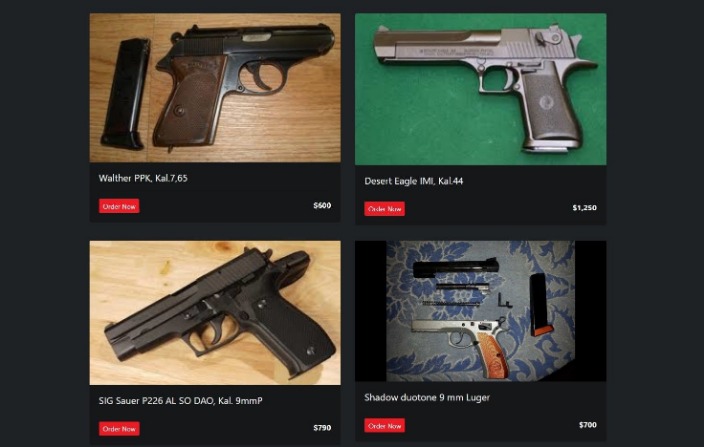
Illicit Goods and Services on the Dark Web
The dark web has become a hub for various illicit goods and services, attracting individuals seeking anonymity for illegal activities. Black markets operating on the dark web facilitate the trade of drugs, stolen data, counterfeit documents, and other prohibited items. These underground markets pose significant challenges for law enforcement agencies worldwide, as they often employ sophisticated encryption and decentralized platforms to evade detection. For those interested in exploring the depths of these anonymous marketplaces, a dark web market(http://abacusborncrffug2ytuqx3fczqbou4mrev56pfliv7ipjfi4uib7cad.onion) provides a glimpse into the transactions and networks that underpin this clandestine economy. Understanding the dynamics of the dark web market is crucial for developing effective strategies to combat illegal activities associated with illicit goods and services.
Common Types of Illegal Substances Sold
The dark web market is a concealed part of the internet that hosts various illegal activities, including the sale of illicit goods and services. One prominent aspect of these markets is the trade in illegal substances, which can range from recreational drugs to more dangerous and controlled substances. Buyers and sellers operate in a clandestine environment, often evading law enforcement by utilizing anonymizing technologies such as Tor networks. This anonymity makes it challenging to track transactions and apprehend those involved in trading illegal substances.
Among the most common types of illegal substances sold on dark web markets are recreational drugs such as opioids, synthetic drugs, cannabinoids, and hallucinogens. These substances are often shipped directly to consumers, who seek anonymity and convenience unavailable through traditional channels. In addition to these, the dark web market also facilitates the trade of prescription medications without proper authorization, posing significant health risks. Some markets also feature the sale of more dangerous and controlled substances, such as methamphetamines and cocaine, which are highly addictive and illegal in most jurisdictions.
Furthermore, the dark web market hosts vendors offering various other illicit items related to illegal substances, including precursor chemicals used in drug manufacturing, paraphernalia, and tools for clandestine production. The proliferation of these illegal goods underscores the need for ongoing efforts by authorities and cybersecurity experts to monitor and dismantle such activities. Consumers and vendors alike should be aware of the illegal nature of these transactions, which contribute to public health issues and criminal enterprises worldwide.
Mechanisms for Concealing Illicit Content
The dark web market has garnered significant attention due to its role in facilitating the trade of illicit goods and services. These markets operate in hidden parts of the internet, often accessed through specialized software that ensures anonymity and privacy for users. This environment enables the exchange of a wide range of illegal items, including drugs, counterfeit currency, stolen data, and weapons, making it a hub for illicit commerce.
One of the primary mechanisms for concealing illicit content on the dark web involves the use of encrypted networks, which mask both the identities of users and the locations of the sites hosting illegal activities. Technologies such as onion routing, which underpins the Tor network, enable communications to be routed through multiple servers, making tracing individuals or content remarkably difficult. This layered encryption is vital for the protection of those involved in illegal transactions, as well as for evading law enforcement efforts.
Dark web markets employ a variety of techniques to hide illicit content further. These include domain hopping, where illicit sites frequently change addresses to evade detection and takedown efforts. They also utilize encrypted messaging platforms and anonymized payment methods, often involving cryptocurrencies to obscure financial trails. Additionally, some marketplaces embed illicit content in coded or encrypted files, making it challenging for automated detection systems to identify prohibited items rapidly.
Overall, the combination of sophisticated encryption methods, frequent domain changes, and the use of encrypted communication channels allows illicit goods and services to be concealed effectively on dark web markets. While these mechanisms provide anonymity and security for users engaged in illegal activities, they also pose significant challenges for law enforcement agencies seeking to combat illegal trade and ensure the safety of online environments.
Brands, Aliases, and Disguises Used by Vendors
The dark web market is a hidden part of the internet where vendors often engage in the sale of illicit goods and services. This clandestine environment facilitates transactions involving prohibited items such as drugs, counterfeit currency, stolen data, and weapons, making it a significant concern for law enforcement agencies worldwide. Vendors on these markets employ various tactics to evade detection, including the use of aliases, disguises, and complex digital footprints.
One common strategy among vendors is the use of multiple aliases and pseudonymous identities. These aliases serve as shields to protect their real identities and make it difficult for authorities to track their activities across different platforms. Often, vendors will adopt names that are unrelated to their genuine identities, integrating a layer of anonymity into their operations.
Disguises are also a critical aspect of vendor tactics. This can include the use of encrypted messaging, anonymizing tools, and frequently changing digital profiles. Vendors may also use code words or obscure references to disguise the nature of their offerings, especially when communicating with potential buyers. Such disguises help them avoid detection and maintain an element of secrecy around their transactions.
As the dark web market continues to evolve, so do the methods used by vendors to conceal their activities. The combination of aliases and disguises creates a complex environment that complicates efforts to combat illegal trading. Staying informed about these tactics is essential for cybersecurity professionals and law enforcement to better understand and disrupt networks involved in the sale of illicit goods and services.
Emerging Trends in Dark Web Commodities
The dark web has become a clandestine marketplace for a variety of illicit goods and services, attracting both illicit vendors and buyers seeking anonymity. These hidden markets facilitate transactions that are prohibited or heavily regulated in the open economy, making them a focal point for law enforcement and cybersecurity efforts. Understanding the emerging trends in dark web commodities is essential for comprehending the scope and scale of these activities.
In recent years, the dark web market has seen a diversification of offerings beyond traditional illegal items such as drugs and weapons. Instead, a range of new and evolving commodities has gained prominence, reflecting shifts in demand and technological advancements. These emerging trends include the proliferation of counterfeit documents, stolen data, and hacking tools, along with new categories like digital currencies and encrypted communication services.
Some notable trends in dark web commodities include:
- Increasing availability of stolen financial information, such as credit card details, banking credentials, and cryptocurrency wallets.
- Growth in the sale of malware, ransomware kits, and exploit kits that enable cybercriminals to compromise systems.
- Expansion of marketplaces for counterfeit documents like fake IDs, passports, and diplomas, which facilitate identity theft and illegal immigration.
- Emergence of services offering encrypted communication tools and VPNs as privacy becomes more prioritized among illicit users.
- Rising trade in illegal substances, including new psychoactive substances and synthetic drugs, often with discreet packaging options.
- Development of dark web market mechanisms that accommodate multiple cryptocurrencies, making transactions more anonymous and harder to trace.
Understanding these trends is vital for law enforcement agencies, cybersecurity professionals, and policymakers aiming to combat crimes facilitated through the dark web market. As the ecosystem continues to evolve, staying informed about the latest commodities and technological adaptations remains crucial in addressing and mitigating illegal activities.
Cryptocurrency Use in Dark Web Markets
The dark web has become a shadowy marketplace where various illicit activities take place, with cryptocurrency serving as a primary method of transaction. The anonymous and decentralized nature of digital currencies makes them ideal for facilitating trades on these hidden networks. As a result, cryptocurrencies have gained significant popularity among dark web markets, enabling users to buy and sell a wide range of illegal goods and services with relative ease. Exploring the dynamics of cryptocurrency use in these markets provides insight into the challenges faced by law enforcement and the importance of advancing cybersecurity measures. For those interested in exploring a reputable dark web marketplace, additional resources can be found online, including secure access points and trading platforms.
Preference for Crypto Payments and Anonymity
The dark web market has become a notable hub for various illicit activities, with cryptocurrency playing a central role in facilitating transactions. One of the primary reasons for the widespread adoption of cryptocurrencies in these markets is their ability to offer a level of financial privacy that traditional payment methods lack. Users can transfer funds without revealing their identities, which is especially appealing for transactions that are meant to remain confidential. This preference for crypto payments stems from the desire to maintain anonymity and reduce the risk of detection by authorities.
Cryptocurrencies like Bitcoin and other digital assets are favored in dark web markets because of their decentralized nature. They operate on blockchain technology that, while transparent, can be used in ways that obscure the identities of participants. Many users employ additional privacy techniques, such as mixing services or privacy-focused cryptocurrencies, to enhance anonymity. This combination of features makes cryptocurrencies particularly suited for buyers and sellers who prioritize discretion and security.
The use of crypto in dark web markets underscores the ongoing tension between the need for anonymity in various transactions and the efforts of regulatory bodies to increase oversight and transparency. Despite increasing efforts to trace transactions, cryptocurrencies maintain a level of pseudonymity that continues to attract users seeking a discreet means of exchange. This dynamic contributes to the persistent reliance on cryptographic assets as the primary payment method in these clandestine marketplaces, reinforcing their role in facilitating anonymous commerce.
Bitcoin and Alternative Digital Currencies
Dark web markets have become notorious for facilitating illicit activities, with a significant portion of transactions relying on various forms of cryptocurrency. Cryptocurrencies like Bitcoin and alternative digital currencies are favored in these environments due to their pseudonymous nature, which provides a layer of anonymity for users engaging in illegal trades. These digital currencies enable a level of financial privacy that traditional banking methods cannot offer, making them attractive for transactions on the dark web market.
Bitcoin remains the dominant cryptocurrency used on dark web markets because of its wide acceptance, liquidity, and established infrastructure. However, the transparent nature of its blockchain, which records all transactions publicly, has led to the development of tools and techniques aimed at deanonymizing users. As a result, some vendors and buyers also explore alternative digital currencies that offer enhanced privacy features, such as Monero or Zcash, to better safeguard their identities.
Use of cryptocurrency in dark web markets generally involves a few key steps: converting fiat currency into digital assets, transferring these assets securely within the market, and finally cashing out via exchanges or other methods. This process often includes the use of anonymizing services, mixing, or tumbling techniques, designed to obscure transaction trails and protect users from detection.
Some factors influencing the choice of digital currency in these markets include transaction speed, security features, and the level of privacy offered. While Bitcoin’s liquidity remains a significant advantage, the increasing awareness and scrutiny by law enforcement have driven users towards more private and less traceable alternatives. As a result, emerging cryptocurrencies with stronger privacy protocols continue to gain popularity in dark web market transactions.
- Cryptocurrency provides a decentralized and pseudonymous method of payment, crucial for activities on dark web markets.
- Bitcoin is the most widely used due to its stability and acceptance, but privacy-focused coins are gaining traction.
- Enhanced privacy features in digital currencies are appealing for users seeking to avoid detection and traceability.
- Utilizing cryptographic mixing services improves transaction anonymity, complicating law enforcement efforts.
- Frequent shifts in cryptocurrency usage reflect ongoing adaptations to law enforcement actions and technological developments.
Crypto Transaction Patterns and Concealment Techniques
Dark web markets have become a notable avenue for the exchange of various goods and services, often utilizing cryptocurrencies as the primary medium of transaction. The inherent pseudonymous nature of cryptocurrencies, such as Bitcoin and Monero, makes them attractive for users seeking anonymity in illicit activities. These platforms facilitate transactions that bypass traditional financial institutions, enabling buyers and sellers to operate with a reduced risk of detection.
Cryptocurrency transaction patterns in dark web markets tend to exhibit specific behaviors aimed at maintaining privacy. Users often employ techniques such as coin mixing or tumbling services, which obscure the trail of funds by blending transactions from multiple sources. Additionally, many traders prefer using privacy-focused cryptocurrencies that provide enhanced anonymity features. These patterns and techniques complicate efforts to trace funds and identify participants involved in illicit transactions.
Concealment techniques are integral to the operation of dark web markets and their users’ trading strategies. Techniques such as transaction obfuscation, employing multiple wallets, and utilizing decentralized exchanges help evade blockchain analysis. Furthermore, some traders split large sums into smaller transactions, making it more difficult for investigators to piece together financial flows. These methods demonstrate a persistent effort to diminish the transparency of cryptocurrency transactions within these clandestine platforms.
Financial Flows and Wallet Clusters
The dark web market has become a prominent hub for illicit activities, largely due to the anonymity it provides to its users. Among the most critical components facilitating transactions on these platforms is the use of cryptocurrencies. Digital currencies such as Bitcoin are favored because they enable financial exchanges without revealing personal identities, making them ideal for the clandestine nature of dark web markets.
Cryptocurrency use in these markets often involves complex financial flows that are designed to obscure the origins and destinations of funds. Techniques such as mixing and tumbling services are frequently employed to break the trail of transactions, complicating efforts to trace illicit money flows. This sophisticated financial choreography enables vendors and buyers to operate with a higher degree of anonymity, challenging law enforcement agencies attempting to track illegal activities.
Analyzing wallet clusters—groups of cryptocurrency addresses that are likely controlled by the same entity—has become a vital method for understanding the financial landscape of dark web markets. By identifying associated wallet clusters, investigators can uncover patterns, identify key players, and map the flow of illicit funds across different platforms. This analytical approach provides critical insights into the operational structure of dark web markets and their ecosystem of transactions.
Overall, the integration of cryptocurrencies into the dark web market ecosystem has significantly facilitated illicit trade, allowing for discreet and efficient transactions. Continuous advancements in blockchain analysis tools are essential for tracking and disrupting these hidden financial networks, thereby aiding in efforts to combat illegal activities associated with dark web markets.
Operational Strategies of Dark Web Vendors
Operational strategies employed by vendors on the dark web market are complex and multifaceted, reflecting the need for anonymity, security, and efficiency in an inherently risky environment. These vendors develop innovative methods to conceal their identities and protect their transactions from law enforcement and malicious actors. Understanding these strategies offers insight into how illicit activities persist and evolve in the digital underground.
Dark web market vendors often utilize layered communication systems, such as encrypted messaging platforms and anonymous hosting services, to coordinate and conduct business securely. They regularly update their operational protocols to adapt to new security measures and law enforcement tactics. Marketplaces may also implement reputation systems and escrow services to build trust and ensure transaction integrity.
One example of a vendor operational strategy involves the use of decentralized networks, which distribute data across multiple nodes to mitigate the risk of detection. Additionally, vendors frequently employ fake identities and exploit anonymization tools like Tor to evade tracking. These tactics collectively create a resilient ecosystem for illegal trade, thriving despite increased scrutiny.
For those interested in exploring more about the dark web market, additional resources and marketplaces can be found through specialized directories and forums dedicated to dark web activities. Continuous adaptation and innovation are key to the sustainability of these vendors’ operations in a challenging environment.
Vendor Clusters and Multi-Market Presence
The dark web market operates as a complex and clandestine ecosystem where vendors employ various operational strategies to maintain their presence and maximize profitability. These strategies are often characterized by the formation of Vendor Clusters, which are groups of related sellers collaborating to strengthen their market influence and share resources. Such clusters facilitate the pooling of intelligence, security measures, and logistics, making it more challenging for law enforcement to dismantle individual operations. Additionally, vendors often develop Multi-Market Presence, allowing them to diversify across multiple dark web marketplaces simultaneously. This approach reduces dependency on a single platform, mitigates risks associated with market takedowns, and broadens their customer base. Operating within a dark web market demands agility, as vendors must adapt quickly to changing marketplace rules, security protocols, and competitive landscapes. The strategic combination of vendor clustering and multi-market engagement underscores the adaptive nature of dark web market operators, highlighting their focus on resilience, scalability, and risk management. These tactics enable vendors to sustain their illicit activities over time while evading law enforcement and market disruptions.

Supply Chain Management and Sourcing
The dark web market operates as a complex and often clandestine environment where vendors employ various operational strategies to ensure success and sustainability. Central to these strategies is the management of supply chains, which involves sourcing products from diverse and often anonymous suppliers to meet customer demands while maintaining confidentiality. Vendors on the dark web carefully select sources that provide quality products at competitive prices, often establishing multiple channels to diversify risk and avoid disruptions.
Effective supply chain management in the dark web market is crucial due to the inherent risks associated with illegal and semi-legal transactions. Vendors typically develop reliable networks that enable discreet procurement and delivery, often relying on encrypted communication and cryptocurrency payments to preserve anonymity. Sourcing methods may include leveraging insider contacts, exploiting cyber vulnerabilities, or purchasing from other vendors operating within the ecosystem. Ensuring a steady flow of inventory helps sustain customer trust and reduces the likelihood of operational interruptions.
Operational strategies also extend to logistical considerations, such as discreet packaging and using various shipping routes to evade detection by authorities. Vendors often implement rigorous inventory control and fraud prevention measures, including verification of supplier credibility and regular audits, to mitigate theft or counterfeit issues. Maintaining a resilient supply chain allows vendors on the dark web market to adapt quickly to changing law enforcement tactics and market fluctuations, ensuring continuous availability of products and services.
Furthermore, successful vendors understand the importance of building a reputation for reliability and discretion, which fosters customer loyalty and attracts new buyers. They may also employ strategic pricing, discounts, and responsive customer support to enhance their market standing. Overall, the interplay of operational strategies, meticulous supply chain management, and sourcing practices forms the backbone of an effective dark web market presence, enabling vendors to operate effectively within an unpredictable and often hostile environment.
Pricing, Listings, and Disguise Tactics
Operational strategies of dark web vendors are designed to ensure anonymity, security, and profitability within the clandestine marketplace. Vendors often employ a combination of technical and operational measures to protect their identities and evade law enforcement while maintaining a reliable supply chain for their illicit products or services. These strategies include sophisticated disguise tactics, secure communication methods, and dynamic pricing models to attract and retain customers.
Pricing strategies on the dark web market are typically influenced by supply and demand, as well as the perceived risk associated with different types of products. Vendors may adjust prices based on competition, the rarity of items, or the complexity of production and distribution. Some vendors employ a flexible pricing approach, offering discounts for bulk purchases or repeat customers, while others rely on premium pricing for high-demand or scarce items to maximize profits.
Listings on dark web platforms are carefully crafted to maximize visibility while minimizing vulnerabilities. Vendors often utilize coded descriptions, ambiguous language, or hidden keywords to evade automated detection systems. They frequently update their listings and create multiple profiles to prevent profile tracking, making it more difficult for law enforcement or rival vendors to establish patterns or connections.
Disguise tactics play a crucial role in maintaining vendor security. These include using anonymous communication channels, such as encrypted messaging services, and employing digital tools to conceal IP addresses. Vendors also adopt operational security practices like managing multiple pseudonymous identities, utilizing VPNs, and regularly changing their digital footprints to avoid detection. Such tactics are essential in sustaining a presence within the dark web market and conducting illicit transactions securely.
Use of Smaller Online Stores and Off-Markets
The dark web market operates through a complex network of vendors employing various operational strategies to maintain anonymity and evade law enforcement. One prevalent approach involves utilizing smaller online stores, which often serve as a means to reduce risk exposure and avoid detection. These smaller storefronts allow vendors to establish a more manageable presence, change locations rapidly, and limit the scale of transactions, thereby minimizing the impact of potential shutdowns.
Off-markets are another critical strategy used by dark web vendors. These off-market channels facilitate covert transactions outside the traditional marketplace platforms, offering an additional layer of security and anonymity. Vendors often communicate directly with buyers through encrypted messaging services or private channels, enabling discreet negotiations and transaction arrangements. This method also helps in avoiding market takedowns and provides more control over the sales process.
By leveraging smaller online stores and off-markets, vendors can operate more flexibly and adapt quickly to changing law enforcement tactics. These strategies support the continuous flow of illicit goods and services while complicating efforts to detect and dismantle these criminal networks. Understanding these operational tactics is key to comprehending the resilience and clandestine nature of the dark web market ecosystem.
Enforcement and Law Enforcement Challenges
Enforcement and law enforcement challenges play a crucial role in tackling criminal activities on the dark web, especially within dark web markets. These clandestine platforms facilitate illegal transactions involving drugs, weapons, stolen data, and other illicit goods, making them a significant concern for authorities worldwide. The anonymous nature of the dark web, combined with advanced encryption techniques and privacy-focused tools, complicates efforts to identify and apprehend perpetrators. As a result, law enforcement agencies must constantly adapt their strategies and leverage technological innovations to combat these illegal enterprises. Investigations often require international cooperation and specialized expertise, highlighting the complexity of shutting down dark web markets and bringing perpetrators to justice. For those interested in exploring more about these hidden networks, some dark web markets are accessible through secure and anonymous links, such as the dark web market(http://nexusafejew45osqaawl2xqjwmincsfvjwuwtm2fums2kjeon7tbmlid.onion). Staying informed and understanding these enforcement challenges are vital in the ongoing effort to disrupt illegal activities on the dark web.
Challenges in Monitoring and Interdicting Markets
Monitoring and interdicting illegal activities within dark web markets pose significant enforcement challenges for authorities worldwide. These clandestine platforms operate with a high degree of anonymity, making it difficult for law enforcement agencies to identify participants, trace transactions, or gather actionable intelligence. The use of advanced encryption techniques, anonymizing tools, and decentralized networks complicates efforts to infiltrate or shut down these markets effectively.
One of the primary challenges in law enforcement is the fluid nature of dark web markets. These platforms often have rapid turnover rates, frequently moving or disappearing when law enforcement cracks down on them. This constant shifting hampers long-term investigations and requires agencies to adapt quickly to new platforms and operational tactics. Additionally, dark web markets often employ sophisticated encryption and security measures, making surveillance and digital forensics more complex than traditional online investigations.
The illicit activities facilitated through these markets, such as drug trafficking, weapon sales, and stolen data exchanges, are often conducted in cryptocurrencies that provide a layer of pseudonymity. While this offers some degree of privacy, it also presents challenges for tracking financial transactions and identifying key players. Enforcement agencies continually develop targeted tools to trace cryptocurrency flows, but suspects frequently employ mixing services and other obfuscation methods to evade detection.
Moreover, international jurisdictional issues can hinder enforcement efforts. Dark web markets operate across borders, and coordinating efforts between different countries with varying legal frameworks and priorities adds complexity to interdiction strategies. The lack of a unified international legal approach can result in slower response times and inconsistent outcomes when attempting to disrupt these markets.
Despite these challenges, ongoing technological advancements and collaborative efforts among law enforcement agencies contribute to increasingly effective strategies for combating illicit dark web market activity. Continuous research, intelligence sharing, and the development of specialized tools are essential to stay ahead of the evolving tactics employed by those running these clandestine platforms.
Cryptocurrency Analytics for Tracking Illicit Activity
Enforcement efforts in combating illicit activities on the dark web market face significant challenges, especially when it comes to cryptocurrency analytics. These markets often utilize cryptocurrencies as a primary method of payment, enabling anonymity and making it difficult for law enforcement to track transactions. As a result, tracking the flow of funds and identifying malicious actors has become increasingly complex, requiring advanced analytical tools and strategies.
One of the key challenges in law enforcement is the pseudonymous nature of cryptocurrencies, which provides users with a certain level of privacy but does not guarantee complete anonymity. This makes it difficult to link transactions to real-world identities without sophisticated blockchain analysis. Additionally, dark web market participants often employ privacy-enhancing techniques, such as coin mixing or tumbling services, to obscure transaction trails further.
To address these challenges, specialized cryptocurrency analytics tools are employed to monitor blockchain activity and identify suspicious transactions. These tools utilize techniques like clustering, address attribution, and pattern recognition to trace illicit funds. However, despite technological advances, criminals continually adapt their methods to evade detection, leading to ongoing enforcement challenges.
Enforcement agencies face the following hurdles:
- Identifying the true origin and destination of transactions amid a complex web of addresses.
- Overcoming the use of privacy-enhancing tools designed to conceal transaction trails.
- Gathering sufficient evidence to prosecute offenders operating on the dark web market.
- International jurisdictional issues, as dark web markets often span multiple countries.
- Keeping pace with rapidly evolving blockchain technologies and methods of obfuscation.
Continued development of cryptocurrency analytics is vital to tackling illicit activity on the dark web market. By enhancing detection capabilities and fostering international cooperation, authorities can more effectively combat illegal operations. Nonetheless, the persistent challenges emphasize the need for a multi-faceted approach combining technological innovation, legal measures, and strategic enforcement to combat dark web activities effectively.
Case Studies of Fentanyl and Major Seizures
Enforcement agencies worldwide face numerous challenges when combatting illegal activities within dark web markets, particularly those involved in the trafficking of fentanyl and other illicit substances. These hidden online marketplaces operate anonymously, utilizing sophisticated encryption and cryptocurrency transactions that hinder traditional law enforcement efforts. Disrupting such operations requires a combination of cyber forensics, intelligence gathering, and international cooperation, which often faces legal and technical hurdles.
One of the significant challenges in tackling dark web markets is the difficulty in tracking the flow of illegal drugs like fentanyl from production to distribution. Fentanyl, a potent synthetic opioid, has become a primary concern due to its high potency and the associated risk of overdose crises. Major seizures of fentanyl and related substances have demonstrated the effectiveness of covert investigations, yet sellers continually adapt their methods to evade detection, such as by shifting servers, using more secure communication platforms, or employing smart contract techniques.
Case studies of major seizures highlight both the successes and ongoing difficulties faced by law enforcement. For example, authorities have successfully infiltrated dark web marketplaces, arrested vendors, and confiscated large quantities of fentanyl, significantly disrupting supply chains. These operations often involve international agencies coordinating to dismantle complex networks. Nonetheless, criminals frequently redeploy similar structures or migrate to newer, more resilient platforms, showcasing the persistent challenge in curbing illegal drug trade on the dark web.
Despite these efforts, enforcing laws in the context of dark web markets remains arduous due to jurisdictional issues, anonymity features, and the rapid evolution of technologies used by traffickers. Enhancing digital forensics capabilities, fostering global cooperation, and developing innovative legal frameworks are critical steps toward more effective enforcement. Continued vigilance and adaptive strategies are essential to counteract the complex and dynamic landscape of dark web marketplaces involved in fentanyl trafficking and major seizures.
Impact of Enforcement Actions on Market Behavior
Enforcement and law enforcement challenges play a significant role in regulating dark web markets, which are often associated with illegal activities such as drug trafficking, stolen data exchanges, and illicit weapon sales. These markets operate in concealed digital environments, making detection and intervention complex and resource-intensive for authorities. Law enforcement agencies face difficulties in tracking transactions, identifying vendors and buyers, and dismantling operational infrastructure without infringing on privacy rights or disrupting legitimate digital activities. Additionally, the constantly evolving nature of the dark web requires enforcement bodies to stay adaptable and innovative in their investigative techniques.
The impact of enforcement actions on market behavior within dark web environments is profound. When law enforcement targets specific markets or vendors, it often results in temporary shutdowns or shifts to new platforms, which can cause volatility and unpredictability in the marketplace. Vendors and users tend to adapt swiftly, often moving operations to more secure or obscure channels to evade detection. This enforcement pressure can discourage some participants from engaging in illegal transactions, but it can also drive others to adopt more sophisticated security measures, complicating future enforcement efforts. The persistent cat-and-mouse dynamic underscores the need for comprehensive strategies that combine technical, legal, and international cooperation to effectively curb illegal activities on the dark web.
- Enhanced investigative techniques are required to adapt to the clandestine nature of dark web markets.
- Cooperation across borders is essential for dismantling transnational illicit networks.
- The rise of encrypted communications and anonymization tools complicates enforcement efforts.
- Market responses to enforcement actions often involve increased security measures and privacy protections.
- Strategic enforcement must balance disrupting illegal activities with safeguarding legitimate online privacy rights.
Case Studies of Fentanyl Trade on the Dark Web
The dark web has become a notorious hub for illegal activities, including the trade of illicit substances like fentanyl. Case studies of fentanyl transactions on the dark web reveal extensive networks where vendors and buyers operate with a high degree of secrecy and sophistication. These markets often facilitate the distribution of dangerous drugs, contributing to ongoing public health crises worldwide. Understanding the patterns and methods used in these transactions is crucial for law enforcement agencies aiming to disrupt such operations and protect communities. For those interested in exploring the structure and operations of the dark web market, there are numerous platforms that serve as online marketplaces, making illegal drugs more accessible than ever before, despite ongoing efforts to shut them down. Some of these markets utilize advanced encryption and anonymity tools to evade detection, highlighting the importance of cybersecurity in combating the fentanyl trade on the dark web.
Identification of Fentanyl Listings and Disguises
The dark web market for illicit substances, particularly opioids like fentanyl, has become a significant concern for law enforcement agencies worldwide. Fentanyl, a potent synthetic opioid, is frequently traded on clandestine platforms where anonymity is maintained through encryption and hidden networks. These dark web marketplaces serve as hubs for vendors and buyers to conduct transactions with relative secrecy, often under the guise of other products or disguised listings to evade detection.
One of the key challenges in combating this illegal trade is the identification of fentanyl listings and the tactics used to disguise them. Sellers often use coded language, abbreviations, or ambiguous descriptions to conceal these items, making it difficult for automated systems to detect illicit content. They may also employ alternative packaging, false descriptions, or embed listings within seemingly legitimate categories to avoid suspicion. Monitoring these practices requires sophisticated analysis techniques to uncover patterns and decode hidden references.

Law enforcement agencies and cybersecurity experts utilize a variety of methods to track and identify fentanyl trade on the dark web market. These include analyzing transaction data, monitoring marketplace communications, and developing specialized algorithms that recognize common disguises and keywords associated with fentanyl and other controlled substances. By combining technical expertise with investigative strategies, authorities aim to dismantle these illegal networks and reduce the availability of fentanyl on these hidden platforms.
Understanding the methods of obfuscation and detection is essential for developing effective countermeasures. Continuous research and collaboration among international agencies are vital in staying ahead of traffickers who adapt their tactics quickly to avoid detection. Ultimately, addressing the fentanyl trade on the dark web market requires ongoing efforts to identify and disrupt these clandestine operations, safeguarding public health and safety.
Market Rules and Their Enforcement
The dark web has become a covert marketplace for the trade of illicit substances, with fentanyl being one of the most concerning drugs available in these underground markets. Fentanyl, a powerful synthetic opioid, is often sold in these environments due to the difficulty in conducting traditional law enforcement efforts and the anonymity that the dark web provides for both buyers and sellers. Case studies highlight how these markets operate, the challenges faced by authorities, and the importance of effective enforcement strategies.
One notable aspect of the fentanyl trade on the dark web is its organized structure, often resembling legitimate markets with defined rules and protocols to ensure trust and security among participants. Market rules can include mechanisms to manage disputes, verify vendor identities, and facilitate secure transactions, all intended to reduce risks for both sellers and buyers. However, despite these measures, the illicit nature of the sales makes enforcement complex and continuously evolving.
Law enforcement agencies have been actively working to dismantle these dark web markets through infiltration, surveillance, and cyber operations. Enforcement strategies often involve tracking cryptocurrency transactions, monitoring marketplace activities, and collaborating with international partners. These efforts have resulted in successful takedowns, arrests, and seizure of illicit drugs, but the resilient and decentralized nature of these markets means that new platforms frequently emerge to fill the void.
Public safety concerns are at the forefront due to fentanyl’s potency and the high risk of overdose associated with its use. Effective enforcement, combined with public awareness campaigns and treatment programs, is critical in addressing the broader issues related to the fentanyl trade on the dark web. Continuous adaptation of market rules and law enforcement tactics remains essential to combat this dangerous underground economy.
- The crawling pipeline consists of authenticating into DWMs and downloading key attributes for each active listing, as highlighted in Fig.
- Furthermore, DWMs have been targets of cybercriminal actors through use of distributed denial-of-service (DDoS) attacks and hacking attempts, while some DWMs also shut down due to administrators stealing funds from customers directly 53, 54.
- A selectable heart button is accessible in each vendor shop so that customers may “favorite” certain products.
- DWM listings on the contrary were much steadier in time and with little variation in the number of active listings throughout the first wave of the pandemic, while decreasing to a lower steady availability from the summer.
Vendor and Supplier Networks in Fentanyl Trade
The dark web marketplace has become a notorious hub for the trade of illicit substances, particularly fentanyl, which poses significant public health risks worldwide. Within this clandestine environment, vendor and supplier networks operate with a high degree of complexity, utilizing encrypted channels to facilitate the distribution of this potent synthetic opioid. These networks often consist of multiple tiers, including raw material suppliers, manufacturers, and distributors, all working covertly to evade law enforcement detection.
In the dark web market, fentanyl vendors typically maintain anonymous profiles and employ reputation systems to foster trust among buyers. They utilize sophisticated encryption methods and cryptocurrency transactions to safeguard their identities and financial flows. These vendors often source fentanyl from international suppliers, leveraging global networks that can rapidly adapt to crackdowns. The supply chains are highly fragmented, making it challenging for authorities to dismantle the entire operation effectively.
Supply networks on the dark web are characterized by their resilience and adaptability. They often shift marketplaces, change vendor identities, and employ new encryption tools to avoid surveillance. This dynamic environment complicates efforts to track and arrest key figures involved in the fentanyl trade. Law enforcement agencies continuously monitor these networks, but the decentralized nature of dark web markets means that depleting supply chains requires coordinated international efforts and advanced cyber investigative techniques.
The proliferation of fentanyl on the dark web underscores the importance of comprehensive strategies to combat illicit online markets. Education campaigns, technological advancements in digital forensics, and international cooperation are crucial in disrupting vendor and supplier networks. As the dark web market continues to evolve, so must the approaches employed by authorities to address the rising threat of fentanyl trafficking through these secretive digital channels.
Flow of Fentanyl-Related Cryptocurrency Payments
Dark web markets have long been channels for illicit transactions, notably involving dangerous substances such as fentanyl. Case studies of these markets reveal complex networks where illegal drugs are exchanged anonymously, often utilizing sophisticated methods to evade law enforcement detection. One prominent aspect of these operations is the prevalence of cryptocurrency payments, which facilitate the flow of funds across borders without physical transaction obstacles.
In many instances, fentanyl trade on the dark web relies heavily on cryptocurrency transactions, primarily involving cryptocurrencies like Bitcoin and Monero. The flow of fentanyl-related payments follows a layered approach, with initial purchases made through illicit market platforms, where buyers and sellers rely on encrypted communications and anonymized digital wallets. This process helps obscure the identities of the participants and complicates tracking efforts by authorities.
Crypto wallets are often used as intermediaries to transfer funds between parties, with transactions recorded on blockchain networks. Law enforcement agencies track these transactions by analyzing blockchain data, which can sometimes lead to the identification of key participants or the seizure of assets. However, traffickers frequently employ techniques such as mixing services or decentralized exchanges to further anonymize their financial flows, making investigations more challenging.
The case studies illustrate that the flow of fentanyl-related cryptocurrency payments is characterized by a high degree of complexity, involving multiple layers of transactions designed to evade detection. The use of dark web markets as intermediaries for purchasing fentanyl demonstrates the significant risks involved, both for users and for law enforcement efforts aimed at dismantling these illegal networks. Nonetheless, ongoing technological advancements and collaborative efforts continue to improve the ability to track and disrupt these illicit financial flows.
Detection and Investigation Techniques
Detection and investigation techniques play a crucial role in understanding and combating activities within the dark web market. These methods enable analysts and law enforcement agencies to uncover illicit operations, track transactions, and identify responsible parties. Effective investigation relies on a combination of technical skills, strategic planning, and advanced tools to navigate the complexities of hidden networks. By employing these techniques, investigators can gather vital intelligence to disrupt illegal trade and enhance cybersecurity measures. Gaining insight into these methods is essential for staying ahead of emerging threats and safeguarding digital ecosystems.
Blockchain Analytics and Wallet Tracking
Detecting and investigating illicit activities within the darknet market requires a combination of advanced techniques and specialized tools. Authorities and cybersecurity professionals employ a range of blockchain analytics, wallet tracking, and investigative methods to identify persons and entities involved in illegal transactions. These strategies are essential for disrupting illegal operations and ensuring law enforcement effectiveness in the digital space.
Blockchain analytics play a crucial role in tracing cryptocurrency transactions associated with dark web market activities. By analyzing transaction patterns, investigators can uncover links between wallets, identify clusters of related activities, and sometimes even pinpoint the real-world identities behind pseudonymous addresses. Techniques such as clustering algorithms and address tagging facilitate the visualization of transaction flows and the detection of suspicious activities.
Wallet tracking is another vital component of the investigative process. It involves monitoring specific addresses over time to observe transaction behaviors, incoming and outgoing funds, and interaction with exchanges or other service providers. Automation tools enable investigators to flag wallets that exhibit characteristics consistent with illicit use, such as frequent exchanges of large sums or connection to known blacklisted addresses.
Detection techniques are complemented by investigative methods that include undercover operations, analysis of marketplace listings, and analysis of forum communications. Combining these approaches allows investigators to build comprehensive case profiles and establish the legitimacy or criminal nature of participants in the dark web market. The goal is to identify key figures, seize assets, and ultimately dismantle criminal networks operating in online clandestine markets.
- Gather data through blockchain explorers and analytics platforms to identify transaction patterns.
- Use clustering techniques to group related addresses and reveal entire networks involved in illegal activities.
- Monitor wallet activity over time to detect suspicious or unusual behavior indicative of illicit operations.
- Cross-reference wallet data with exchange registration information to identify potential owners.
- Leverage human intelligence and undercover investigations to corroborate blockchain findings and gather contextual evidence.
Continuous advancements in detection and investigation techniques are vital to staying ahead of evolving dark web market strategies. Combining blockchain analytics, wallet tracking, and traditional investigative methods creates a robust framework for combating illegal online markets and safeguarding the digital ecosystem from criminal threats.
Linking Dark Web Vendors to On-Chain Activity
Detection and investigation techniques are essential for uncovering illicit activities within dark web markets, especially when attempting to link dark web vendors to on-chain activity. These methods involve a combination of technological tools, analytical strategies, and investigative skills designed to trace anonymous transactions back to individual actors. Understanding the connection between dark web vendors and blockchain activity is crucial for disrupting illegal trade and enforcing law enforcement efforts.
One primary technique involves blockchain analysis tools that scrutinize transaction patterns to identify suspicious activity. Analysts look for anomalies in transaction volume, timing, or transfer patterns that could indicate coordinated efforts with dark web vendors. By mapping transaction flows and identifying wallet clusters, investigators can establish links between on-chain activity and specific vendors operating within dark web marketplaces.
Another approach is the use of data mining and scrapping techniques on dark web forums and marketplaces to gather intelligence on vendor identities and their operational behaviors. Combining this with blockchain data can help corroborate whether certain vendor accounts correspond to particular blockchain wallets. This multi-layered analysis enhances the accuracy of identifying illicit actors involved in illegal trading activities.
Crucial to this process is the deployment of advanced geolocation and network analysis tools that can uncover the infrastructure supporting dark web marketplaces. These tools can detect the hosting services and exit nodes used to access dark web platforms, providing additional clues to associate vendors with on-chain transactions. Law enforcement agencies also leverage undercover operations and digital forensics to collect evidence that links marketplace activities to specific blockchain addresses.
In summary, linking dark web vendors to on-chain activity requires a multidisciplinary approach that combines blockchain analytics, cyber intelligence gathering, and technical surveillance. These detection and investigation techniques play a vital role in combatting the hidden networks of illegal trade and bringing offenders to justice within the complex environment of dark web markets.
Visualization Tools for Illicit Transaction Flows
Detecting and investigating illicit transaction flows within dark web markets require specialized techniques and advanced visualization tools to uncover hidden activities. These environments are intentionally designed to obscure the origin, destination, and nature of transactions, making traditional tracking methods inadequate. Therefore, investigators employ a combination of digital forensics, network analysis, and data analytics to identify suspicious patterns and link related activities.
One key technique involves analyzing transaction metadata and blockchain data where applicable. Although many transactions on dark web markets utilize cryptocurrencies, blockchain analysis tools can trace transaction flows, identify clusters of addresses, and reveal links between different actors. These methods assist investigators in mapping out the transaction networks and detecting anomalies such as large transfers or unusual activity patterns.
Visual analytics play an essential role in illuminating complex transaction relationships. Sophisticated visualization tools create graphical representations of transaction flows, allowing analysts to identify central nodes, hierarchies, and hidden links that might indicate money laundering, fraud, or other illicit activities. These visualizations help streamline the investigation process by turning raw data into comprehensible insights, facilitating the identification of key players within dark web transactions.
In addition to blockchain analysis and visualization, investigators often deploy machine learning algorithms to automate the detection of suspicious activities. These algorithms can classify and flag anomalous transaction patterns based on historical data, thereby enhancing the speed and accuracy of investigations. Combining these techniques with traditional investigative methods increases the likelihood of uncovering illicit transaction networks in dark web markets.
Overall, leveraging advanced detection and investigation techniques, complemented by powerful visualization tools, is crucial for addressing the challenges presented by illicit transaction flows within dark web markets. These approaches enable law enforcement and security professionals to pierce through the anonymity and complexity inherent in such environments and work towards dismantling criminal networks.
Identifying High-Risk Clusters and Traders
Detecting and investigating activities within dark web markets requires a combination of advanced techniques and strategic analysis. These markets often operate under a veil of anonymity, making it challenging to identify high-risk clusters and traders involved in illegal activities. Effective detection begins with monitoring digital footprints, transactions, and communication patterns characteristic of illicit marketplaces. Identifying high-risk actors involves scrutinizing their behaviors, trade volumes, and network connections, which may reveal clusters engaged in unlawful transactions. Thorough investigation techniques incorporate data analysis, behavioral profiling, and pattern recognition to uncover suspicious activities and pinpoint traders who pose significant risks to law enforcement efforts.
- Monitoring transaction patterns and looking for abnormal spikes in trading volume can help identify clusters involved in high-value or illegal trades.
- Analyzing communication channels and metadata may reveal connections between traders, facilitating the detection of coordinated activities.
- Employing machine learning and data mining techniques can assist in recognizing behavioral anomalies and establishing risk profiles for individual traders and clusters.
- Integrating open-source intelligence (OSINT) methods enables investigators to gather contextual information relevant to specific traders or groups.
- Utilizing network analysis tools to map relationships and interactions between entities offers insights into high-risk networks within dark web markets.
- Consistent pattern recognition and anomaly detection are essential for flagging suspicious activities that deviate from typical marketplace behaviors.
By deploying these detection and investigation techniques, authorities can better understand the structure and activity of dark web markets, enabling them to identify and disrupt high-risk clusters and traders involved in illicit transactions. Maintaining an ongoing monitoring process is crucial, as these markets are continually evolving to evade detection and enforcement efforts.
Countermeasures and Risk Mitigation
Countermeasures and risk mitigation are essential components in navigating the complex and often perilous landscape of the dark web market. With the increasing prevalence of illegal activities and cyber threats, understanding how to protect oneself and assets is paramount. Effective strategies involve identifying potential vulnerabilities, implementing security protocols, and maintaining vigilance against emerging risks. In the context of a dark web market, deploying these measures can help users avoid scams, data breaches, and legal pitfalls. For instance, utilizing secure communication channels and avoiding the exposure of personal information are key steps in risk reduction. Additionally, exploring trusted resources can provide valuable insights into best practices and safety measures when engaging with dark web platforms or marketplaces, such as dark web market. Implementing comprehensive countermeasures ensures a safer experience and minimizes potential damages from malicious activities.
Use of Custom Data and Alerts for Illicit Activity
Countermeasures and risk mitigation strategies are essential components in managing the security of dark web markets, especially given the prevalence of illicit activities online. Implementing robust procedures helps organizations identify suspicious behaviors early and reduces exposure to potential threats. A proactive approach includes deploying advanced monitoring tools, establishing clear protocols for incident response, and training personnel to recognize signs of unauthorized or malicious activities. These measures are vital in maintaining the integrity of digital platforms that handle sensitive or valuable data and ensuring compliance with legal standards.
Utilizing custom data and alert systems plays a crucial role in proactively addressing illicit activities within dark web markets. By integrating tailored algorithms and filters, organizations can monitor specific keywords, transaction patterns, and behavioral indicators linked to illegal operations. Automated alerts created from these criteria enable prompt action, such as suspending suspicious accounts or initiating investigations before significant damage occurs. This targeted monitoring approach enhances the ability to detect and respond to threats associated with dark web market transactions.
- Develop and implement custom data collection frameworks that gather relevant information from diverse sources, including dark web marketplaces, forums, and communication channels.
- Set up real-time alert systems configured to notify security teams about anomalous activities or suspicious transactions based on predefined risk indicators.
- Regularly update and refine the data parameters and alert criteria to adapt to evolving tactics used by malicious actors on dark web markets.
- Coordinate with law enforcement and cybersecurity agencies to share intelligence and improve the effectiveness of countermeasures.
- Conduct periodic reviews of monitoring and response strategies to ensure they address new threats and vulnerabilities effectively.
Combining these measures creates a comprehensive risk mitigation framework that enhances the ability to combat illicit activities associated with dark web markets. Continual improvement and vigilance are essential to staying ahead of cybercriminals engaged in potentially damaging operations.
Proactive Monitoring of Evolving Market Tactics
In the rapidly evolving landscape of underground digital marketplaces, particularly within the dark web market, organizations and cybersecurity professionals must prioritize robust countermeasures and risk mitigation strategies to safeguard their assets and reputation. These markets are often characterized by constantly shifting tactics, including the use of anonymization techniques, encrypted communications, and sophisticated hacking methods, which necessitate proactive and adaptive defensive measures.
Implementing comprehensive threat monitoring systems is essential to detect and respond to emerging threats promptly. This involves real-time analysis of dark web activity, tracking new marketplace listings, and assessing potential data leaks or breaches. By staying vigilant and continuously updating detection mechanisms, organizations can identify malicious activities before they escalate into significant incidents.
Another critical component is regular security assessments and vulnerability scans, which help identify weaknesses in existing infrastructure that could be exploited within the dark web market environment. When combined with employee training and awareness programs, these measures significantly reduce the risk of infiltration or data exfiltration.
Furthermore, establishing clear incident response protocols ensures swift action in the event of a threat detection. Collaborating with cybersecurity experts and law enforcement agencies can enhance the effectiveness of these efforts, especially when dealing with illegal activities often associated with dark web markets.
Overall, adopting a proactive stance by continuously monitoring evolving tactics, assessing risks, and deploying adaptive countermeasures is vital for organizations seeking resilience against threats emanating from dark web markets. This strategic approach helps mitigate potential damages and maintain operational integrity amid the unpredictable nature of these clandestine online forums.
Enhancing Disruption and Interdiction Strategies
Countermeasures and risk mitigation are essential components in the effort to combat illicit activities within the dark web market. These strategies are designed to disrupt illegal operations, deter criminal behavior, and protect legitimate users and organizations from potential harm. Enhancing these countermeasures involves a combination of technological, procedural, and collaborative approaches to stay ahead of evolving threats and maintain a secure environment.
To effectively address risks associated with dark web market activities, it is critical to implement comprehensive measures that target vulnerabilities and prevent malicious transactions. This includes deploying advanced monitoring tools that analyze patterns of illegal trade, and conducting regular security audits to identify potential exposure points. Collaboration between law enforcement agencies, cybersecurity firms, and financial institutions can also significantly improve interdiction efforts through shared intelligence and coordinated actions.
- Invest in sophisticated detection systems capable of identifying suspicious activities and transactions within the dark web.
- Develop robust protocols for responding to detected threats, including swift content takedowns and legal actions.
- Implement strong user authentication and encryption standards to safeguard data and prevent unauthorized access.
- Engage in intelligence-sharing networks to stay informed about emerging tactics used by cybercriminals operating in dark web markets.
- Promote international cooperation to facilitate cross-border investigations and enforcement actions against illegal activities.
Enhancing disruption and interdiction strategies involves continuously adapting to new methods employed by criminals. This may include deploying honeypots to gather intelligence on dark web market operators or disrupting payment channels used for illicit exchanges. It is also vital to educate stakeholders about potential risks and signs of illegal activity, encouraging proactive reporting and vigilance. By strengthening these areas, authorities and organizations can better mitigate risks and diminish the influence of malicious actors within the dark web market environment.
Collaborative Efforts Between Authorities and Analytics Firms
Countermeasures and risk mitigation are essential strategies in addressing the threats posed by dark web markets, which often facilitate illegal activities such as drug trafficking, counterfeit goods, and cybercrime. Effective response requires a coordinated effort between law enforcement agencies and analytics firms to identify, monitor, and dismantle these clandestine online platforms. Combining technological expertise with legal authority enhances the capacity to prevent illicit transactions and protect public safety.
Collaborative efforts between authorities and analytics firms involve several key measures to combat dark web activities:
- Intelligence Sharing: Establishing secure channels for exchanging information about emerging threats, suspicious activities, and known malicious actors helps to build a comprehensive understanding of dark web market operations.
- Data Analysis and Monitoring: Employing advanced analytics tools enables real-time tracking of transactions, user behavior, and marketplace trends, facilitating early detection of illegal activities.
- Cybersecurity Enhancements: Strengthening digital defenses to prevent infiltration and gather forensic evidence supports ongoing investigations and the disruption of illicit networks.
- Legal and Policy Frameworks: Developing clear regulations and collaborative protocols ensures that efforts to shut down dark web markets adhere to legal standards and respect privacy rights.
- Public Awareness and Education: Informing the public about the risks associated with dark web markets and encouraging reporting of suspicious activities can aid in reducing demand and disrupting supply chains.
Implementing these countermeasures, with active cooperation between authorities and analytics firms, significantly enhances the capacity to mitigate risks associated with dark web markets. Such joint efforts are vital for dismantling illegal networks, safeguarding community safety, and maintaining cyber hygiene in an increasingly digital world.