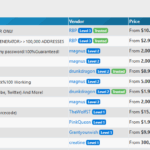
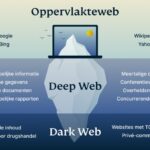
Darknet Market Links and Their Role in Cybercrime Ecosystem
Darknet market links play a central role in the underground cybercrime ecosystem, providing a gateway for illicit goods and services to circulate anonymously. These hidden online marketplaces facilitate transactions involving illegal products such as drugs, weapons, counterfeit documents, and hacked data. By utilizing specialized network addresses, often in the form of onion links, these markets maintain a high level of privacy and security for their users. For example, accessing numerous darknet markets can be achieved through links like darknet marketplace. These platforms not only enable illegal trade but also contribute to a broader cybercrime ecosystem that challenges law enforcement and cybersecurity experts worldwide.
Definition and Significance of Darknet Market Links
Darknet market links serve as essential gateways to hidden online marketplaces that operate on the dark web, a concealed part of the internet not indexed by traditional search engines. These links facilitate access to clandestine platforms where illegal goods and services are exchanged anonymously, making them a core component of the cybercrime ecosystem. The significance of darknet market links lies in their ability to connect users with illicit vendors offering everything from drugs and counterfeit documents to stolen data and hacking tools.
Within the realm of cybercriminal activity, darknet market links act as the digital entry points that enable transactions beyond the reach of law enforcement scrutiny. Their role extends to fostering a thriving black market economy, where anonymity and untraceability are prioritized. As a result, these links are highly sought after and frequently circulated among cybercriminals, terrorists, and other malicious actors. The structured nature of these links allows for the seamless operation of illegal marketplaces, reinforcing their importance in maintaining the cybercrime ecosystem. Understanding the function and significance of darknet market links is crucial for cybersecurity efforts aimed at disrupting illegal activities online.
Types of Darknet Market Links and Access Methods
Darknet market links are web addresses that provide access to illicit marketplaces operating on the dark web, a portion of the internet not indexed by traditional search engines and accessed through specialized anonymity-preserving tools. These links serve as entry points for users seeking to purchase illegal goods and services, ranging from counterfeit documents to illicit substances, playing a central role in the cybercrime ecosystem. By maintaining these links, vendors and operators facilitate anonymous transactions and hide their physical locations from law enforcement agencies.
There are various types of darknet market links, each designed to serve specific purposes within the illicit marketplace. The most common are direct onion links, which connect users to the primary marketplace page through encrypted onion routing circuits. These links are often dynamically changed or rotated regularly to avoid detection and shutdown efforts. Additionally, some markets utilize secondary links for user registration or specific product categories, helping to compartmentalize operations and improve security.
Access methods to these dark web marketplaces typically involve the use of anonymous browsers like Tor or I2P, which enable users to navigate the network securely and privately. These browsers mask IP addresses and encrypt traffic, making it difficult for authorities or third parties to trace activities back to individuals. Users generally need to acquire verified dark web addresses or links through underground forums, encrypted messaging platforms, or peer-to-peer dissemination, ensuring that only trusted or authorized individuals can reach these marketplaces. Protecting the integrity and confidentiality of darknet market links is crucial for both vendors and buyers engaged in illegal activities, as exposure can lead to law enforcement takedowns and disruptions in the cybercrime infrastructure.
Common Platforms Hosting Darknet Market Links
Darknet market links serve as gateways to hidden online marketplaces where illegal goods and services are exchanged anonymously. These links are essential for accessing platforms that operate outside the reach of traditional internet regulations, often facilitating activities such as drug trafficking, weapons sales, counterfeit documents, and hacking services. The anonymity provided by darknet market links makes them a crucial component of the cybercrime ecosystem, enabling criminals to coordinate and conduct transactions while evading law enforcement detection.
Several common platforms are known for hosting darknet market links, often through specialized software or encrypted networks. These platforms operate on the dark web, a segment of the internet not indexed by conventional search engines and accessible only via specific tools like Tor. The marketplace environment is dynamic, with sites frequently changing domains or switching hosts to avoid takedown efforts. Despite these challenges, understanding the role of darknet market links is vital for cybersecurity and law enforcement efforts to combat illegal activities online.
- Tor-based marketplaces: Many darknet markets are hosted on the Tor network, with their links providing access through the Tor browser. These platforms often function with escrow services to ensure secure transactions between buyers and sellers.
- I2P and other networks: Some marketplaces operate on alternative privacy-focused networks such as I2P, which also host marketplace links that facilitate anonymous trade.
Darknet market links are a critical component of the cybercriminal infrastructure, enabling illicit trade under the guise of anonymity. By understanding their role and the platforms that host them, authorities and cybersecurity professionals can better strategize efforts to monitor and dismantle illegal markets operating in the shadows of the internet.
Distribution and Sharing of Darknet Market Links
Sharing and distributing darknet market links is a common practice within certain online communities seeking access to specific marketplaces. These links serve as gateways to hidden online markets that operate outside traditional web access, often requiring specialized software and anonymity measures. The dissemination of such links, like darknet market links, allows users to connect with vendors and explore various illicit services and products securely. However, the distribution process is fraught with risks, including exposure to malicious actors and legal consequences, making the sharing of these links a delicate and often secretive activity.
Use of Telegram Channels for Sharing Market Links
Distribution and sharing of darknet market links are complex activities that often operate within hidden networks to maintain anonymity and security. These links serve as gateways for users seeking access to various services and products available on the dark web. Due to the sensitive nature of these markets, obtaining and disseminating links require careful measures to avoid detection and legal repercussions.
One common method of sharing darknet market links is through encrypted messaging platforms, particularly Telegram channels. These channels enable users to circulate links swiftly and discreetly to a targeted audience. Telegram’s privacy features, such as end-to-end encryption and secret chats, make it an attractive option for sharing darknet market links securely. Channels dedicated to this purpose often have large follower bases, allowing rapid dissemination of updated or new links.
Ensuring the confidentiality of any shared darknet market links, such as darknetmarketlink123, is crucial to prevent unintended exposure or interception by authorities. As these links can change frequently, users rely on trusted channels and communities to keep abreast of the latest addresses. Sharing links via Telegram channels is also facilitated by the use of coded language or indirect references to bypass automated detection systems and censorship efforts.
In summary, the distribution and sharing of darknet market links, particularly through Telegram channels, play a vital role in the ecosystem of the dark web. This method allows for quick, secure, and discreet access, although it also involves significant risks for all parties involved. Users must exercise caution and prioritize safety when engaging in such activities to protect their identity and avoid legal issues.
Dark Web Forums and Marketplace Listings
Distribution and sharing of darknet market links, forums, and marketplace listings are activities that often occur within clandestine online environments. These links serve as gateways to hidden marketplaces and obscure communities where transactions and discussions about illicit goods frequently take place. Sharing such links can contribute to the rapid spread of illegal content and activities across the dark web.
When involved in the dissemination of darknet market links, it is crucial to understand the potential risks and legal implications. Accessing or distributing these links may lead to criminal investigations or cyber security threats. Due to these reasons, many users exercise caution and limit sharing to trusted circles or encrypted channels.
The following are key considerations regarding the distribution of darknet market links and related content:
- Security and Anonymity: Sharing links should prioritize maintaining user anonymity and avoiding detection by law enforcement or malicious actors.
- Legality and Ethics: Distributing links associated with illegal activities can have serious legal consequences and ethical implications.
- Controlled Sharing: When sharing darknet market links, it is often done in private forums or encrypted communication channels to reduce exposure.
- Risks of Exposure: Public sharing of marketplace listings or links increases the risk of exposure to scammers, hackers, or law enforcement agencies.
In conclusion, the distribution and sharing of darknet market links require careful consideration of security, legality, and ethical issues. Responsible handling of these links is vital to prevent unintended consequences and to uphold principles of secure and lawful online activity.
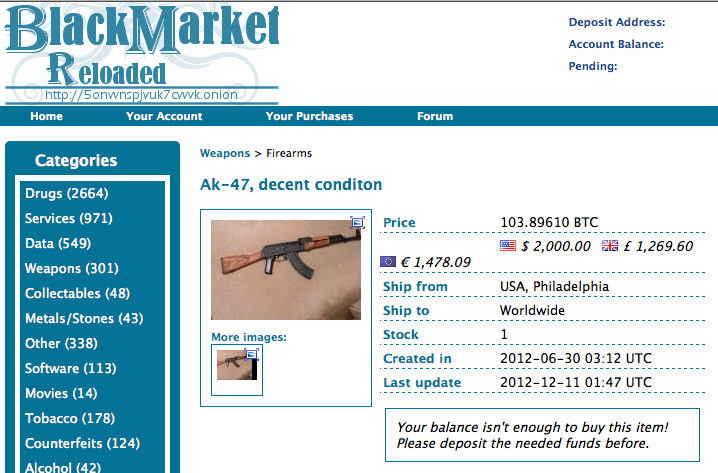
Encrypted Messaging Apps and Private Groups
Distribution and sharing of darknet market links, encrypted messaging apps, and private groups pose significant challenges for online safety and security. These elements are often used to facilitate illicit activities, making their dissemination a concern for law enforcement and cybersecurity professionals alike. Understanding how these links and communication channels are shared helps in developing effective strategies to monitor and mitigate illegal content exposure.
Darknet market links are primarily distributed through various clandestine means, including encrypted messaging platforms, private forums, and social media channels. These links are often shared within trusted networks to prevent detection and infiltration by authorities or unwanted parties. Such sharing typically occurs in closed groups or private messages, where access is restricted to verified members, ensuring a level of anonymity and security.
Encrypted messaging applications play a crucial role in the distribution of darknet links. Users utilize these apps to communicate securely, sharing links to markets, vendors, and related services discreetly. Private groups within these apps serve as hubs for exchanging sensitive information and ensuring that only trusted members have access to the shared content. The encrypted nature of these apps complicates efforts to track and regulate the spread of illegal links.
Efforts to curb the distribution of darknet market links often include monitoring public and certain private communications, although the encrypted nature of messaging apps presents a significant obstacle. Law enforcement agencies may collaborate with cybersecurity experts to identify patterns and vulnerabilities, but the private nature of these groups makes comprehensive oversight difficult.
In conclusion, the sharing of darknet market links within encrypted messaging apps and private groups represents a complex challenge that requires a nuanced approach. Improved detection techniques, user awareness, and cooperation among online platforms and authorities are essential in limiting the proliferation of illicit links and ensuring cybersecurity and legal compliance.
Techniques for Accessing Darknet Market Links
Accessing darknet market links requires specialized techniques to ensure safety and privacy. Due to the illicit nature of these markets, users must employ methods that minimize exposure to risks such as tracking and surveillance. Utilizing Tor browsers and secure connection practices is essential for navigating darknet sites securely. Techniques like using VPNs alongside Tor can add an extra layer of anonymity, helping users access darknet market links more safely. For example, visiting markets through dedicated links such as this onion address allows users to explore offerings while maintaining operational security. Understanding and applying these techniques is crucial for anyone seeking access to darknet market links in a secure and responsible manner.
Utilizing Tor Browser and Anonymizing Tools
Accessing darknet market links requires careful consideration of privacy, security, and anonymity. Users often turn to specialized tools such as the Tor browser to browse hidden websites securely. The Tor network encrypts communication and routes it through multiple volunteer-operated servers, making it difficult to trace online activities back to the user. This ensures that browsing darknet markets remains private and protected from potential surveillance.
Utilizing Tor alone may not be sufficient for maintaining complete anonymity. It is recommended to enhance privacy by employing additional anonymizing tools such as VPNs, which mask your IP address before connecting to the Tor network. Combining these tools creates multiple layers of protection, reducing the chances of de-anonymization when accessing darknet market links.
When accessing darknet market links, it is essential to adhere to safety protocols, including avoiding the use of personal information and securing your device against malware. Using privacy-centric browsers, disabling scripts, and employing security-focused operating systems can also mitigate potential risks. Remember that navigating darknet markets involves inherent security challenges, so always stay informed about best practices for safe browsing in this environment.
Employing VPNs and Proxy Services
Accessing darknet market links requires careful consideration of privacy and security measures to protect your identity and online activities. The darknet is a part of the internet that is not indexed by standard search engines and often hosts anonymous marketplaces for various goods and services. To navigate these sites safely, users typically employ specialized tools such as VPNs and proxy services that help conceal their IP addresses and browsing activities. These techniques are essential for maintaining anonymity when exploring dark web marketplaces. Ensuring your connection is secure reduces the risk of tracking or surveillance, which is critical for anyone engaging with darknet markets like those that offer diverse products or services.
- As cybercriminals continue to exploit dark web markets, Telegram channels, and underground forums, organizations must take a proactive approach to identifying potential risks.
- These coordinated actions targeted darknet vendors, buyers, and administrators, directly undermining the infrastructure of notorious markets such as Nemesis, Tor2Door, Bohemia, and Kingdom Markets.
- The presence of such a channel highlights how stolen financial data circulates within dark web markets, making Telegram an essential tool for cybercriminal activities.
- Such large-scale exposure of compromised identity data highlights the increasing risks organizations face regarding account takeovers and unauthorized access attempts.
- The group also facilitates connections between buyers and sellers, with some members offering daily-updated data sources and private datasets for a fee.
When attempting to access darknet market links, following systematic steps can enhance privacy and safety:
- Use a reputable VPN to encrypt your internet traffic and mask your IP address, making it difficult for third parties to trace your activity.
- Employ proxy services that act as intermediaries, routing your connection through servers in different locations to further obfuscate your identity.
- Always update your security software and use Tor Browser—an essential tool for accessing darknet links securely and anonymously.
- Avoid revealing personal information or engaging in activities that could compromise your anonymity while browsing darknet markets.
- Navigate to known and trusted darknet marketplaces, often found through secure channels like community forums or classified directories, to access the links you require.
By combining VPNs and proxy services effectively, users can enhance their privacy when connecting to darknet market links. This layered approach helps mitigate risks associated with monitoring and cyber threats, ensuring a safer browsing experience. Remember, maintaining strict operational security and staying informed about the latest privacy tools are crucial when exploring sensitive online environments like the darknet. Proper implementation of these techniques allows users to access darknet markets while safeguarding their identity and digital footprint.
Searching for Hidden Market Links via Cybercriminal Networks
Accessing darknet market links requires specialized techniques due to the anonymous and encrypted nature of the dark web. Cybercriminal networks often employ sophisticated methods to hide their marketplace URLs, making traditional searches ineffective. To uncover these hidden market links, individuals typically utilize a combination of anonymizing tools, advanced search strategies, and network analysis. These approaches are crucial for researchers, cybersecurity professionals, or law enforcement agencies aiming to monitor or investigate illegal activities online.
One common technique involves the use of Tor (The Onion Router), which provides a layered encryption system to mask user identities and website locations. By configuring secure and private settings on the Tor browser, users can access concealed marketplaces while maintaining anonymity. Often, these market links are shared through encrypted forums or messaging channels, making direct discovery challenging. Researchers may analyze traffic patterns and network nodes to identify potential market sites or use intelligence gathering to track the dissemination of links within cybercriminal communities.
Another strategy involves leveraging specialized search engines designed for dark web content. These search engines index hidden sites, helping users locate market links that are otherwise difficult to find through standard search methods. Additionally, monitoring social media, underground forums, and encrypted messaging platforms can yield clues regarding the current addresses of darknet markets. Cybercriminals frequently update their links to evade detection, so continuous monitoring and quick adaptation are necessary. Effective techniques for accessing these darknet market links are vital for staying informed of emerging threats and understanding the landscape of illegal online trade.
Risks and Legal Implications of Darknet Market Links
Engaging with darknet market links involves significant risks and potential legal consequences. Accessing or attempting to purchase goods through platforms like http://nexusafejew45osqaawl2xqjwmincsfvjwuwtm2fums2kjeon7tbmlid.onion can expose individuals to criminal charges, as many transactions involve illegal products or activities. Law enforcement agencies actively monitor such sites to curb illegal operations, making it important for users to understand the legal implications of their online activities. The dangers also extend to cybersecurity threats, including scams, malware, and the possibility of personal data theft. Being aware of these risks helps in making informed decisions about interactions with darknet market links and emphasizes the importance of adhering to legal boundaries and online safety practices.
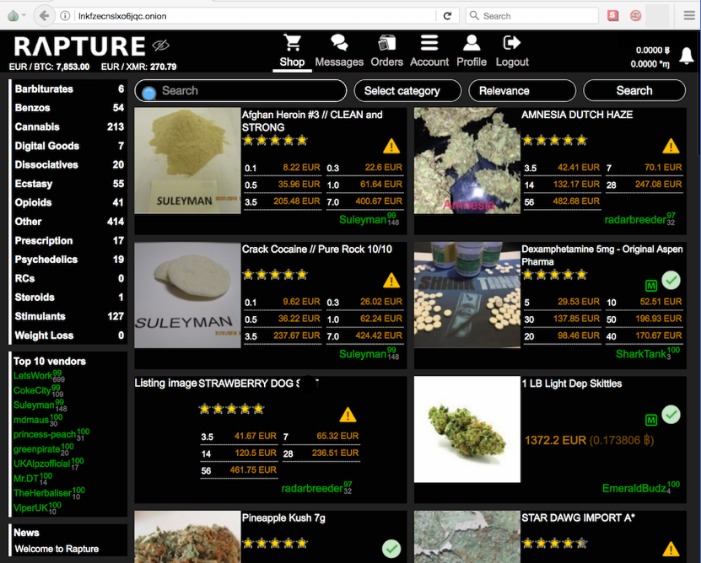
Exposure to Malicious Content and Scams
Engaging with darknet market links involves significant risks and potential legal repercussions. These platforms often operate outside the bounds of law, hosting a wide array of illicit activities that can result in serious legal consequences for users. Browsing or attempting to access darknet market links places individuals at risk of violating laws related to drug trafficking, illegal goods, or cybercrime, which can lead to fines, prosecution, or imprisonment. Moreover, these sites frequently contain malicious content designed to compromise user security.
One major concern associated with darknet markets is exposure to scams and fraudulent schemes. Users may encounter fake marketplaces or malicious actors posing as legitimate vendors, leading to financial losses or identity theft. The anonymity features of the darknet make it easier for scammers to exploit unsuspecting individuals, making it crucial to exercise extreme caution when encountering even a darknet market link. In addition, the interconnected nature of these sites often facilitates the distribution of malware and other malicious software, which can infect computers or steal sensitive personal data.
Beyond the immediate risk of scam or malware, accessing darknet market links may also draw the attention of law enforcement agencies. Authorities around the world monitor illegal activities on these sites and have implemented various measures to shut down illicit operations. If detected, users risk legal action regardless of whether they made purchases or simply visited these sites. Overall, the potential legal, financial, and cybersecurity threats associated with darknet market links underscore the importance of avoiding such sites and maintaining cyber safety practices.
Legal Consequences of Accessing and Using Dark Web Links
Accessing darknet market links can pose significant legal risks and potential consequences. These underground platforms often facilitate illegal activities, including the sale of illicit substances, stolen data, and counterfeit goods. Engaging with or even merely visiting darknet market links may inadvertently expose individuals to legal scrutiny, as authorities actively monitor and investigate these networks to combat illegal trade.
Legal implications of utilizing darknet market links vary by jurisdiction but generally include charges related to conspiracy, possession, or distribution of illegal items. Law enforcement agencies may track users through digital footprints, IP addresses, and transaction records to establish illicit activity. Consequently, accessing these links can lead to criminal investigations, fines, or imprisonment, especially if it involves purchasing or facilitating illegal transactions.
Furthermore, the risks extend beyond legal penalties. Darknet markets are often repositories for scams, malware, and other cybersecurity threats that can compromise personal data or financial information. Users who visit or use darknet market links also face potential exposure to fraudulent schemes or compromised systems, which can result in substantial financial loss and identity theft.
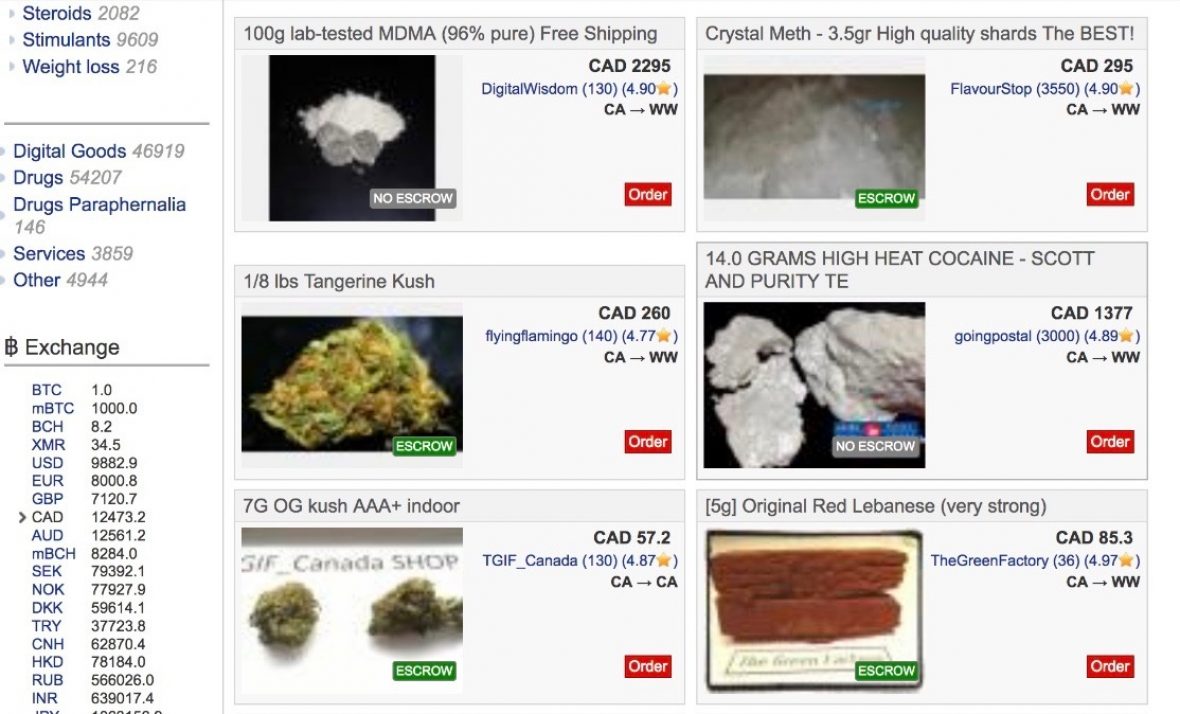
It is essential for individuals to recognize the dangers associated with darknet market links and to understand that involvement can have serious legal and personal repercussions. Vigilance and legal awareness are critical to avoid unintended engagement with illegal activities and to safeguard oneself from potential legal actions and cybersecurity threats.
Ensuring Safe Navigation and Avoiding Traps
Darknet market links are often associated with illegal activities and pose significant risks to users who may unknowingly encounter scams, malware, or law enforcement investigations. Navigating the darknet requires caution, as many sites are designed to deceive or trap unwary visitors. It is essential to understand the potential legal implications and take steps to ensure safe browsing when exploring these markets. Engaging with darknet market links without proper precautions can result in severe consequences, including criminal charges, financial loss, or exposure to harmful content.
One of the primary risks associated with darknet market links is encountering fraudulent schemes that aim to steal personal information or funds. Cybercriminals frequently create malicious sites that mimic legitimate marketplaces, luring users into revealing sensitive data or making payments for non-existent goods. Additionally, some sites may contain malware or viruses that can compromise devices, leading to data breaches or system damage. To avoid these traps, users should verify the authenticity of links, avoid clicking on suspicious advertisements, and use security tools such as VPNs and up-to-date antivirus software.
Legal implications are a significant concern when dealing with darknet market links. Many of these platforms facilitate illegal transactions involving drugs, weapons, or stolen data. Accessing or participating in such markets can inadvertently implicate individuals in criminal activities, even if they do not directly engage in wrongdoing. Law enforcement agencies actively monitor darknet sites and links, so being connected to illicit markets can lead to investigation and prosecution. To stay safe, users should abstain from visiting sites like darknet market links that are known for illegal content and ensure they adhere to the laws of their jurisdiction.

In conclusion, exploring darknet market links carries inherent dangers and legal risks. To navigate safely, users should educate themselves about common scams, employ robust cybersecurity practices, and avoid engaging with or accessing illegal content. Staying informed and cautious helps in protecting both personal safety and legal standing while browsing the darknet environment.
Monitoring and Detecting Darknet Market Links
Monitoring and detecting darknet market links is a critical component of cybersecurity and law enforcement efforts to curb illegal activities online. These links often serve as gateways to hidden marketplaces where illicit goods and services are traded anonymously. By implementing advanced tracking techniques and analyzing network traffic patterns, it’s possible to identify and monitor these covert links effectively. For instance, one such suspicious enlace can be found at a darknet market link, which exemplifies the importance of vigilant scanning and detection. Staying ahead of malicious actors requires continuous innovation in detection methods to ensure these hidden marketplaces are identified promptly and thoroughly. Recognizing and understanding these links enable authorities to take appropriate action to disrupt illegal operations and safeguard online communities.
Use of Dark Web Monitoring Tools and Services
Monitoring and detecting darknet market links is a critical component of cybersecurity and law enforcement efforts aimed at combating illegal activities on the dark web. These markets often facilitate the sale of illicit goods and services, making their identification vital for maintaining online safety and legal compliance. Implementing effective detection strategies involves leveraging specialized tools and services designed to scan and analyze dark web environments for suspicious links and activities.

Dark web monitoring tools and services are essential in this process, providing the ability to track and analyze dark web sites, forums, and markets continuously. These tools often utilize web crawling, pattern recognition, and data analysis techniques to identify new or modified links associated with darknet markets. By continuously monitoring these sources, organizations can quickly discover new illegal market entries or illicit trading activities related to darknet market links.
Many dark web monitoring solutions also incorporate threat intelligence feeds that provide real-time updates on emerging threats. This helps in early detection of darknet market links involved in activities such as drug trafficking, illegal arms sales, or counterfeit currency distribution. Advanced services may employ machine learning algorithms to evaluate the risk level of detected links, helping organizations prioritize their response efforts.
Detecting and understanding darknet market links is vital because cybercriminals frequently change their site addresses to evade detection, making continual monitoring a necessity. By integrating these monitoring tools into a comprehensive security strategy, organizations can better protect their networks, assist law enforcement initiatives, and reduce the risk of falling victim to darknet-related criminal activities.
Strategies for Identifying Market Link Shareings in Public Channels
Monitoring and detecting darknet market links is a crucial component of cybersecurity and law enforcement efforts aimed at disrupting illegal online activities. As these markets often operate covertly, identifying their presence and understanding how they share links in public channels can be challenging but essential for effective intervention. Employing strategic methods to monitor these clandestine networks helps uncover patterns and prevent criminal activities associated with illicit goods and services.
One of the primary strategies involves analyzing public communication platforms such as social media, forums, and messaging services where market links are often shared. These channels serve as initial points for link dissemination, making them valuable sources for monitoring efforts. Automated tools and algorithms can be employed to scan content for certain keywords, patterns, or suspicious URLs indicative of darknet market links. This helps in proactively identifying ongoing promotions or link sharing activities related to clandestine markets.
Effective detection also requires the use of advanced data analysis techniques, such as machine learning models trained to recognize common features of darknet market links. These features may include specific domain patterns, slang, or coded language used to mask the true nature of the links. Combining these techniques with manual review ensures a comprehensive understanding of the sharing activities and helps distinguish legitimate communications from malicious or deceptive postings.
Organizations can also use honeypot.Tiktok, Twitter, and Telegram channels to observe how market links are shared in real-time. Setting up monitored accounts or bot-driven alerts enables faster detection of new links as they appear. Tracking shifts in how and where these links are posted provides insight into the operational tactics of darknet vendors and helps anticipate future link sharing patterns.
- Regular Surveillance: Continuously monitor social media, forums, and encrypted messaging apps for new postings containing darknet market links.
- Keyword and Pattern Recognition: Deploy automated systems programmed to detect coded language, URLs, or symbols associated with darknet markets.
- Behavioral Analysis: Study user engagement and posting behaviors that correlate with link sharing activities.
- Network Analysis: Map out the relationships and interactions among users sharing these links to uncover broader networks and influence patterns.
- Collaboration with Cybersecurity Partners: Work closely with law enforcement and cybersecurity organizations for intelligence sharing and joint investigations.
In conclusion, effectively monitoring and detecting darknet market links involves a multifaceted approach combining technology, behavioral analysis, and collaborative efforts. By staying vigilant in analyzing public channels and applying advanced detection techniques, authorities and security professionals can better identify and disrupt illegal online markets, including those sharing links to darknet markets. Continuous adaptation of these strategies is vital to stay ahead of evolving tactics used by cybercriminals.
Role of Cyber Threat Intelligence in Tracking Links
Monitoring and detecting darknet market links plays a crucial role in maintaining cybersecurity and law enforcement efforts. Darknet markets are often used for illegal activities, including drug trafficking, illicit trading, and more, making it essential to identify and track associated links effectively. Cyber threat intelligence (CTI) provides valuable insights into these hidden networks by systematically gathering, analyzing, and interpreting data related to malicious activities and underground marketplaces.
One of the primary roles of cyber threat intelligence is to identify patterns and indicators that suggest the presence of darknet market links. This involves monitoring various online sources such as forums, marketplaces, and underground communities where these links are frequently shared or discussed. By leveraging advanced analytics, threat researchers can detect emerging links and predict their potential impact, allowing authorities or organizations to act swiftly.
Furthermore, cybersecurity teams utilize threat intelligence to track the lifecycle of darknet market links, understanding their dissemination, changes, and eventual takedown. Through comprehensive monitoring, it becomes possible to uncover not only direct links but also related infrastructure that supports these illicit marketplaces. This proactive approach helps in disrupting illegal activities before they escalate.
Effective detection also relies on the integration of automated tools and threat intelligence feeds that continuously scan for new or altered darknet market links. These tools can recognize suspicious keywords, anomalous hosting patterns, and related metadata, enhancing the speed and accuracy of detection efforts. Overall, the role of cyber threat intelligence in tracking darknet market links is vital in safeguarding digital spaces and enforcing legal compliance.
Impact of Policy Changes on Darknet Market Links
The landscape of darknet markets is highly influenced by recent policy changes and increased regulatory scrutiny. These shifts often lead to adjustments in how darknet market links are shared and accessed, impacting both vendors and users. As authorities crack down on illicit activities, some market operators relocate or modify their online addresses to avoid detection. For example, users seeking alternative access points may visit secure marketplaces such as this darknet marketplace to continue their activities. Understanding the evolving policies helps in recognizing how these changes influence the accessibility and security of darknet links, shaping the broader ecosystem of anonymous online commerce.
Telegram and Platform Policy Enforcement
Recent policy changes across digital platforms and enforcement measures have significantly impacted the visibility and accessibility of darknet market links. These changes aim to curb illegal activities but often lead to unforeseen consequences for users seeking access to these markets. As authorities strengthen their efforts, the structure and availability of darknet market links are evolving, prompting both challenges and adaptations within the ecosystem.
One major effect of new policies is the increased difficulty in locating operational darknet markets. Platform bans and tighter enforcement efforts on communication channels like Telegram have resulted in the rapid removal of links and related content. Consequently, users must navigate more complex and less predictable environments to find these markets, often relying on non-traditional methods or community-driven directories.
Policy enforcement also influences the behavior of marketplace operators, who may now employ more advanced security measures or shift to less detectable platforms. This adaptive behavior can include frequent updates to market links or migration to less visible networks, which complicates efforts to monitor or shut down illegal activities. Furthermore, stricter policies often lead to a decline in the trustworthiness of available links, as more appear compromised or fraudulent.
- Enhanced platform restrictions result in fewer accessible darknet market links, impacting users’ ability to find reputable sources.
- Increased surveillance and policy enforcement on communication channels force operators to innovate, making links more transient and harder to track.
- Policy shifts lead to a rise in misleading or malicious links, raising security concerns for users attempting to access darknet markets.
Overall, while policy changes and enforcement actions aim to increase security and reduce illegal activity, they also generate a dynamic environment where darknet market links constantly adapt. This ongoing imbalance underscores the importance of understanding the evolving landscape and the impact of regulatory measures on online illicit marketplaces.
Shift to Alternative Platforms for Market Link Sharing
Policy changes and increased enforcement efforts have significantly impacted the landscape of darknet market links, prompting vendors and users to adapt to new challenges. As governments and law enforcement agencies intensify their crackdown on illegal online activities, many traditional darknet markets face closures and closures or increased operational risks. This has led to a decline in the availability of market links in the original platforms, making it harder for users to access the products and services they seek.
In response to such restrictions, there has been a notable shift toward alternative platforms designed to evade detection and maintain user anonymity. These new venues often employ advanced security measures, utilize decentralized structures, or operate on different protocols to facilitate access to market links. Vendors frequently move their operations to these emerging channels to sustain their businesses and retain customer bases, ensuring that darknet market links remain accessible despite tightening policies.
This evolving environment underscores the importance for users and vendors to stay informed about the latest developments in darknet markets and to understand the risks associated with navigating these clandestine spaces. Continued policy changes are likely to drive further innovation and adaptation within the ecosystem, fostering a persistent demand for alternative platforms for market link sharing. Ultimately, this ongoing dynamic shapes the future of darknet markets and the ways in which market links are distributed and accessed within the digital underground.
Emergence of Decentralized and Encrypted Platforms
The evolving landscape of darknet markets has been significantly influenced by recent policy changes and technological advancements, leading to a complex environment for users and operators alike. As authorities intensify efforts to shut down illicit online platforms, many marketplaces have either shut down or migrated to more resilient structures, affecting the accessibility and stability of darknet market links. These policy shifts often result in a reduced number of accessible links, but they also prompt innovators to develop more sophisticated methods of maintaining anonymity and security for users.
One notable impact of policy changes is the increased adoption of decentralized and encrypted platforms. These platforms operate without a central authority, making them more resistant to shutdowns and legal interventions. By employing advanced encryption technologies and peer-to-peer networks, they ensure continuous operation even when individual nodes or services face crackdown. This decentralization enhances user privacy and makes it more challenging for law enforcement to track and shut down interconnected darknet market links.
The emergence of such platforms has also led to a proliferation of covert and encrypted links, which are often more difficult to identify and monitor. As traditional marketplaces face increased scrutiny, users may turn to these more secure environments, further complicating efforts to regulate and control illegal activities online. The resilience of decentralized platforms underscores the importance of adapting investigative techniques and applying innovative cybersecurity measures to maintain effective oversight of darknet markets and their links.
In summary, policy changes have prompted a shift towards more resilient and encrypted platforms, making darknet market links harder to shut down and monitor. This evolution highlights the ongoing battle between regulatory efforts and technological innovation within the dark web ecosystem, emphasizing the need for adaptive strategies to address these emerging challenges and preserve online safety and security.
Preventive Measures for Organizations
Preventive measures are crucial for organizations to safeguard their digital assets and maintain operational integrity in today’s increasingly interconnected world. As cyber threats evolve, especially within dark web environments, organizations must implement proactive strategies to identify and mitigate potential risks. Darknet market links, often associated with illicit activities, can pose significant security and legal challenges if accessed or exploited improperly. Understanding how to defend against fraudulent links and malicious actors on the darknet is essential for maintaining a secure organizational infrastructure. For example, monitoring and controlling access to known darknet markets such as darknet market links can help prevent data breaches and unauthorized transactions. Employing comprehensive cybersecurity measures, including threat intelligence and employee training, can further reduce vulnerability to darknet-related threats. Ultimately, a proactive stance allows organizations to anticipate potential dangers and respond effectively, ensuring ongoing safety and compliance in a complex digital landscape.
Dark Web and Darknet Link Exposure Detection
Preventive measures are essential for organizations aiming to safeguard their digital assets from exposure on the dark web and darknet markets. These clandestine platforms often host compromised data, including confidential company information and sensitive customer details, which can be exploited for criminal activities or reputational harm. Implementing proactive strategies helps organizations detect and mitigate potential threats early, reducing the risk of data breaches and unauthorized disclosures.
One of the primary steps is to conduct continuous monitoring of the dark web for any mentions of the organization’s name, proprietary information, or employee credentials. Specialized tools can automate searches and alert security teams if suspicious links or data leaks are detected on darknet market sites or other illicit forums. Regular audits of internal systems, including monitoring past data breaches, can also prevent sensitive information from being unknowingly exposed online.
Organizations should establish robust data handling and security policies, including encryption, access controls, and employee training to prevent accidental leaks. Additionally, maintaining an active incident response plan ensures swift action in case of exposure, helping to contain potential damage. Encrypting sensitive communications and regularly updating security software further reduce vulnerabilities that could be exploited on dark web platforms.
Awareness of darknet market links and other illicit platforms is vital. By understanding which markets or forums are used for selling stolen data or illicit goods, organizations can better target their monitoring efforts and respond promptly to emerging threats. Formal partnerships with cybersecurity firms specializing in dark web intelligence can enhance detection capabilities, providing insights into particular darknet market links that may pose a risk to the organization.
Overall, a layered approach combining technological tools, policy enforcement, and staff awareness is key to preventing exposure and safeguarding organizational information from the dangers posed by the dark web and darknet market links. Continuous vigilance and proactive measures can significantly diminish the likelihood of falling victim to criminal activities associated with these clandestine online marketplaces.
Integration of Threat Intelligence Modules
Preventive measures are essential for organizations aiming to safeguard their digital infrastructure against threats originating from darknet markets. These markets often serve as hubs for illicit activities, including the sale of stolen data, illegal goods, and malicious tools, which can directly impact organizational security. Implementing a comprehensive security strategy involves integrating threat intelligence modules that enhance an organization’s ability to detect and respond to suspicious activities linked to these markets.
One effective preventive measure is the deployment of real-time threat intelligence modules that continuously monitor various sources for emerging threats. These modules can identify and flag links or references to darknet market sites that may indicate ongoing or planned malicious activities. By analyzing patterns and indicators associated with darknet market links such as VPN footprints or suspicious transactions, organizations can proactively assess vulnerabilities and take appropriate actions to mitigate risks.
Furthermore, organizations should establish protocols for regular updates and collaboration with external threat intelligence providers. Sharing information about darknet market activities helps in maintaining an up-to-date understanding of evolving tactics used by cybercriminals. Training staff to recognize links to darknet markets and understanding the potential indicators of compromise are also vital components of a preventive strategy.
Integrating these threat intelligence modules with existing security infrastructure enables seamless detection and response to threats potentially linked to darknet markets. This proactive approach not only mitigates the chances of data breaches and fraud but also enhances overall cybersecurity resilience by maintaining awareness of the various channels where malicious actors operate. Vigilance and continuous adaptation to new threats remain fundamental in protecting organizational assets from the evolving landscape of darknet market activities.
Employee and User Education on Dark Web Threats
Darknet market links pose significant security challenges to organizations, employees, and users, as these platforms often facilitate illegal activities, including the sale of stolen data, illicit goods, and cybercriminal services. To combat these threats effectively, organizations must implement robust preventive measures and prioritize comprehensive education initiatives to equip their teams with the knowledge needed to recognize and avoid potential pitfalls associated with the dark web.
One of the primary preventive strategies involves deploying advanced cybersecurity tools such as threat detection systems, firewalls, and intrusion prevention systems that can identify signs of dark web activities and block malicious traffic before it reaches internal networks. Regular vulnerability assessments and security audits help uncover weaknesses that malicious actors might exploit, particularly in relation to accessing darknet market links that may host or distribute stolen credentials and data.
Employee and user education is equally vital in mitigating dark web threats. Organizations should conduct ongoing training sessions that highlight the dangers of clicking on suspicious links, especially those related to darknet markets, which are often referenced in phishing or scam campaigns. Emphasizing the importance of strong, unique passwords and encouraging the use of multi-factor authentication can also reduce the risk of unauthorized access to sensitive information stolen from these marketplaces.
Additionally, promoting awareness about the nature of darknet market links and how cybercriminals leverage them to distribute malware or sell compromised data can empower users to be vigilant. Organizations should remind staff not to visit unknown sites or click on suspicious links that could serve as entry points for cybercriminal activities originating from the dark web.
By integrating technological safeguards with targeted education on darknet market links, organizations can build a resilient security posture that minimizes risks and enhances their ability to detect and respond to dark web threats effectively. Maintaining an informed and cautious workforce, coupled with proactive security measures, is essential in safeguarding organizational and personal data from ongoing dark web risks.