Darknet Market Listings Overview
The darknet has become a complex and often mysterious part of the internet, hosting various marketplaces where a wide range of goods and services are exchanged. A darknet market list provides valuable insights into these hidden platforms, helping users understand their structure, offerings, and the risks involved. These markets operate in anonymized environments, making them difficult to access yet crucial for many users seeking privacy and unregulated transactions. For those interested in exploring these networks, a comprehensive darknet market list can serve as a guide to navigate the often volatile landscape safely and effectively.
Popular Categories of Illicit Goods and Services
Darknet markets are online platforms operating on hidden networks, primarily the Tor or I2P networks, where users can buy and sell various goods and services anonymously. These markets maintain a marketplace-style structure, allowing vendors to list items and buyers to browse, evaluate, and complete transactions while preserving privacy. The darknet market list is constantly evolving as new platforms emerge and others shut down, reflecting the dynamic and often clandestine nature of these marketplaces.
Among the many offerings available on darknet market listings, some of the most common are illicit drugs, which are frequently the top category. These drug listings span a wide range of substances, from controlled pharmaceuticals to recreational substances, often sold at discounted prices. In addition to narcotics, darknet markets also feature counterfeit currencies, fake identification documents, stolen financial information, and hacking tools, making them a hub for cybercriminal activity.
Another prevalent category includes illegal services such as hacking, money laundering, and even hacking-for-hire services. These offer malicious software, exploit kits, and access to compromised accounts or networks. Furthermore, counterfeit goods like fake designer apparel, watches, and accessories are popular categories, appealing to consumers seeking luxury items at lower prices. The darknet market list also includes marketplaces for illicit firearms, stolen data, and adult content, illustrating the wide range of illegal activities facilitated through these platforms.
The dark web’s anonymous environment makes it attractive for both illicit vendors and consumers seeking to avoid traditional law enforcement oversight. However, it also poses significant risks, including scams, legal consequences, and exposure to dangerous content. Awareness of the common categories on the darknet market list can help users understand the scope and risks associated with these illegal online marketplaces.
Types of Illegal Products Sold
The darknet market list provides insight into the shadowy world of online marketplaces operating beyond the reach of conventional internet regulations. These markets are often accessed through specialized software that ensures anonymity and privacy for users and vendors alike. Understanding the landscape of these markets can shed light on the types of transactions that occur in this clandestine space and help inform efforts to monitor and combat illegal activities.
Darknet market listings typically feature a wide range of products, many of which are illegal according to international laws and regulations. These include controlled substances such as narcotics, synthetic drugs, and prescription medications, often sold without proper authorization. Additionally, illegal firearms and weaponry are frequently listed in these markets, presenting serious safety concerns. The sale of stolen data, credit card information, and hacking tools also forms a significant part of the illegal products available on darknet markets.
Besides tangible illegal goods, darknet market listings also include counterfeit products, such as fake passports, IDs, and branded merchandise. Cybercriminal tools, such as malware, ransomware, and hacking services, are commonly sold, enabling other illicit activities to flourish. Moreover, the sale of adult content, including illegal pornography and exploitation material, often appears in these listings, making them a focal point for law enforcement efforts.
The darknet market list highlights the complex and diverse nature of illegal merchandise traded in these secretive online communities. While many of these markets are shut down or temporarily unavailable, new ones constantly emerge to replace them, perpetuating a cycle of clandestine commerce. Recognizing the types of illegal products sold through these markets is essential for understanding their impact on society and for developing effective strategies to reduce their influence and protect public safety.
Emerging Trends in Market Listings
The darknet market list provides a comprehensive overview of the various anonymous online marketplaces that operate on the dark web, facilitating trade in a range of goods and services often outside legal boundaries. These markets are typically accessed through specialized web browsers that anonymize user activity and location, ensuring privacy for both vendors and buyers. As these markets evolve, staying informed about current listings is essential for understanding the scope and nature of activities taking place within the dark web ecosystem.
Recent trends in market listings reveal increased diversity in product categories, with some markets expanding beyond traditional offerings such as drugs and illicit substances to include counterfeit items, cyber services, and hacking tools. There is also a noticeable shift toward more sophisticated operations that prioritize security and user anonymity, often employing advanced encryption methods and multi-layered hosting strategies. These developments reflect the ongoing adaptation of darknet market vendors to law enforcement measures and the need for greater operational security.
Emerging trends in the darknet market list demonstrate a move towards decentralized and peer-to-peer models, reducing reliance on centralized marketplaces which are more vulnerable to shutdowns and investigations. Additionally, the integration of cryptocurrencies with enhanced privacy features, along with the use of decentralized payment platforms, is becoming increasingly common. Such innovations aim to improve transaction confidentiality and reduce the risk of traceability. Keeping track of these trends is vital for understanding the shifting landscape of darknet markets and their listings, which continue to adapt rapidly to new technological and security challenges.
Major Darknet Marketplaces
The darknet hosts a variety of marketplaces that facilitate the exchange of goods and services beyond the reach of conventional law enforcement. These marketplaces are often shrouded in anonymity and utilize encrypted communication to protect both buyers and sellers. A comprehensive darknet market list provides insight into some of the most prominent platforms operating within this clandestine network, each offering different products ranging from electronics to illicit items. Understanding these marketplaces is crucial for researchers, cybersecurity experts, and law enforcement agencies aiming to monitor and regulate online illegal activities. For instance, exploring a darknet market list can reveal the structure, challenges, and evolving nature of these online hubs.
Prominent Marketplaces and Their Features
Darknet marketplaces have become a significant aspect of online underground activity, providing platforms for the exchange of various goods and services beyond conventional regulations. These marketplaces operate on encrypted networks, enabling users to buy and sell anonymously. A darknet market list often includes a range of prominent platforms known for their stability, security features, and diverse offerings.
Among the major darknet marketplaces, some of the most well-known include names that have established a reputation for their resilience and user-friendly interfaces. These marketplaces typically feature multiple categories such as illicit drugs, digital products, counterfeit items, and hacking services. A darknet market list frequently highlights these marketplaces due to their influence and volume of transactions.
Prominent marketplaces often distinguish themselves through robust security protocols, escrow payment systems, and user verification processes designed to reduce fraud. Many of these platforms use multisignature escrow services to ensure both buyer and seller protections. Additionally, features like community feedback and review systems help maintain trust and transparency among users.
It’s important to note that while these marketplaces vary in size and scope, they share common features including anonymized communication channels, PGP encryption for messages, and decentralized hosting to prevent takedowns. These characteristics make them resilient in the face of law enforcement efforts. A darknet market list serves as a guide to those seeking information on the most active and reliable platforms in the underground economy.
Overall, understanding the features and reputation of major darknet marketplaces can be crucial for users involved in these networks, whether for research, security analysis, or awareness. Continuous updates to a darknet market list reflect the dynamic and ever-changing landscape of these underground platforms.
Market Takedowns and Disruptions
The darknet marketplace landscape has been continuously evolving, characterized by the rise and fall of various platforms that facilitate anonymous transactions often involving illicit goods and services. These marketplaces operate on hidden networks, primarily using the Tor browser, making them difficult to monitor and shut down. However, authorities worldwide have implemented numerous takedowns and disrupt operations to curb illegal activities associated with these sites. Understanding the current darknet market list is essential for recognizing the shifts within this clandestine economy and the efforts made to dismantle it.
Major darknet marketplaces such as those involved in drug trafficking, counterfeit documents, hacking tools, and other illegal commodities regularly attract law enforcement attention. These platforms often experience temporary closures, exit scams, or deliberate disruptions designed to protect users and vendors or to dismantle entire networks. Many of these operations are uncovered through international cooperation, advanced cybersecurity measures, and undercover investigations. The darknet market list, which catalogs these platforms, highlights the volatile nature of online illicit markets and the ongoing efforts to combat them.
Market takedowns and disruptions are a significant part of the fight against online illegal activities. Law enforcement agencies worldwide have succeeded in shutting down prominent marketplaces, seizing assets, and arresting key players. These actions disrupt the supply chains and deter new entrants, although new marketplaces often emerge in their stead. Despite these efforts, the clandestine nature of the darknet ensures that this market remains resilient. Monitoring the darknet market list helps authorities and researchers track trends, identify emerging threats, and develop new strategies to combat illegal online operations effectively.
New Marketplaces Launching Post-Disruption
The darknet marketplace landscape continues to evolve rapidly, especially following periods of disruption that have temporarily affected major platforms. In recent times, several new darknet marketplaces have emerged, aiming to fill the void left by those that shut down or experienced significant operational challenges. The darknet market list remains dynamic, reflecting shifts in vendor activity, security measures, and user preferences.
One notable trend is the rise of marketplaces that emphasize enhanced security and anonymity features, attracting both established vendors and new users. These platforms often incorporate innovative technologies to safeguard transactions and user identities, contributing to their quick growth on the darknet market list. Additionally, new marketplaces are often launched with targeted niches, which help them build a loyal user base in a competitive environment.
Despite the volatility, some longstanding marketplaces continue to adapt, integrating new features to maintain relevance and security. However, the consistent appearance of new entrants signifies a resilient demand and a persistent innovation drive within the darknet ecosystem. As such, users and vendors alike must stay informed about emerging platforms, security practices, and operational changes to navigate this complex environment effectively.
The ongoing development of darknet marketplaces underscores the importance of staying vigilant and updated, especially in a landscape that is continually shifting due to law enforcement efforts and technological advancements. The darknet market list serves as a valuable resource for understanding current trends, identifying reliable platforms, and assessing the risks associated with various marketplaces.
Pricing and Supply of Darknet Market Items
The pricing and supply of items available on darknet markets can vary widely depending on numerous factors, including the rarity of the product, demand, and the level of competition among vendors. Understanding these dynamics is essential for anyone interested in navigating the darknet market landscape. Market listings tend to fluctuate frequently, reflecting real-time supply and pricing trends. A comprehensive darknet market list provides valuable insights into the various platforms where these transactions occur, helping users identify reputable sources and compare offerings effectively. For instance, the availability of specific items on a market like darknet marketplace often influences their pricing and supply. Being aware of the current state of supply and costs across multiple markets enables more informed decision-making in this complex digital ecosystem.
Price Trends for Illegal Goods
The darknet market landscape is characterized by its unique pricing dynamics and fluctuating supply of illegal goods. These markets operate in a semi-anonymous environment, which influences how prices are set and how supply levels are maintained. Typically, prices for items such as drugs, counterfeit documents, and stolen data are determined by supply and demand within the market, often fluctuating based on law enforcement activity, market competition, and regional availability. A comprehensive darknet market list reveals a variety of platforms facilitating these transactions, highlighting the diverse range of products available and the differences in pricing strategies across markets.
Price trends for illegal goods on the darknet tend to change over time, impacted by various factors including law enforcement crackdowns, new supplier emergence, and shifts in consumer demand. During periods of increased law enforcement activity, prices often rise as supply decreases, making certain goods more expensive. Conversely, when new suppliers flood the market or restrictions loosen, prices may drop, making illegal items more accessible. The darknet market list showcases these trends, illustrating the fluid nature of the underground economy and how illicit goods are priced according to current supply conditions and market sentiment.
Supply levels of darknet market items are influenced by the ease of production, shipping methods, and the risk involved in trafficking illegal goods. As law enforcement steps up efforts, some suppliers may reduce activity or relocate, leading to temporary shortages and price hikes. Conversely, technology advancements and alternative distribution channels can enhance supply, stabilizing or lowering prices. Monitoring the darknet market list provides insights into these supply-side shifts, revealing which goods are in high demand and how their availability impacts overall pricing trends in this clandestine marketplace.
Supply Estimates and Market Size
The darknet market landscape is characterized by its unique pricing and supply dynamics, driven by the clandestine nature of its operations. Because transactions occur outside traditional financial systems, prices for illegal goods and services often fluctuate based on supply, demand, risk, and law enforcement activity. Understanding the supply estimates and market size provides valuable insight into the scale and impact of these hidden marketplaces.
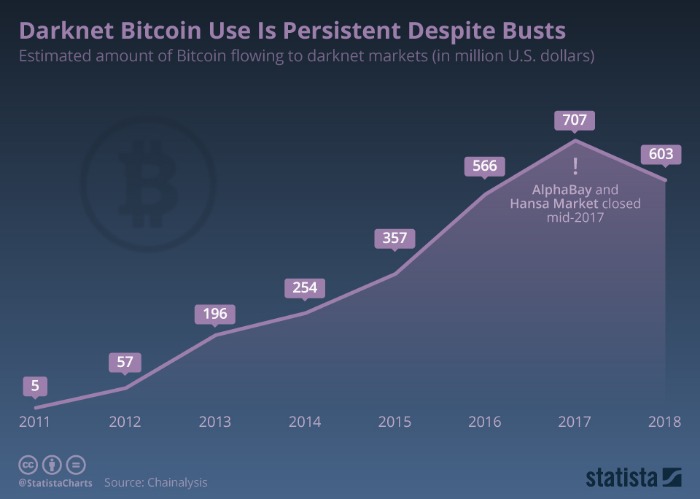
Estimating the supply of items on darknet markets involves analyzing transaction volumes, vendor activity, and product listings. While precise data is challenging to obtain due to the covert environment, experts generally agree that the supply of illicit goods such as drugs, counterfeit items, and stolen data remains substantial and consistently evolving. Fluctuations in supply are influenced by law enforcement crackdowns, vendor migration to new platforms, and technological adaptations like encrypted communications.
The market size for darknet market items is significant, with estimations suggesting billions of dollars worth of transactions annually. This encompasses a wide variety of product categories, with some markets specializing in specific niches like narcotics or illicit services. The darknet market list highlights the prominent platforms that facilitate these transactions, although the number of active markets and vendors can shift rapidly as platforms are seized or shut down.
When considering pricing on darknet markets, several factors come into play:
- Market demand for specific items influences prices, with high-demand products commanding higher premiums.
- The level of security and anonymity measures adopted by vendors can affect the pricing structure.
- Risk of law enforcement intervention often results in price inflation for high-risk items.
- The volume of supply and vendor competition can lead to price fluctuations, with some vendors offering discounts to attract buyers.
Overall, the darknet market list offers a snapshot of the current landscape, illustrating the ongoing proliferation of these markets despite increased efforts to combat illicit activities. The combination of supply estimates, market size, and pricing strategies underscores the persistent challenge of regulating and understanding this shadow economy.
Factors Influencing Price Fluctuations
The darknet market list provides a comprehensive overview of online platforms that facilitate the buying and selling of various illicit items. One of the key aspects influencing these marketplaces is the pricing and supply of items offered. The prices on darknet markets are often subject to significant fluctuations, driven by multiple factors that impact both supply and demand. Understanding these factors is essential for anyone navigating this shadow economy.
Supply levels on darknet markets are affected by the number of active vendors, the ease of sourcing products, legal risks, and the overall stability of the marketplace. When supply increases—such as more vendors entering the market or improved logistics—the prices for certain items tend to decrease due to heightened competition. Conversely, limited availability or disruptions in supply chains often lead to higher prices, especially for high-demand or scarce products.
Demand also plays a crucial role in pricing dynamics. Items with high demand, perhaps due to perceived quality or rarity, can command premium prices. Seasonal trends, law enforcement activities, and public awareness campaigns can influence demand, causing fluctuations in prices. Vendors adjust prices in real time to balance their profit margins with market conditions, which explains the often volatile pricing observed in the darknet market list.
Furthermore, external factors such as increased law enforcement crackdowns, technological changes, or shifts in legislation can impact both supply and demand. A surge in law enforcement activity, for example, might reduce the perceived safety of sourcing certain items, leading to decreased supply and increased prices. Conversely, the emergence of new platforms or technology can make sourcing easier, boosting supply and often reducing prices.
Overall, the pricing and supply of darknet market items are intertwined and influenced by a complex web of factors. This constant fluctuation underscores the importance for buyers and vendors to stay informed of the latest market trends, which are often reflected in the darknet market list. Monitoring these dynamics helps stakeholders better understand market behaviors and make more informed decisions.
Data and Payment Information on Dark Web Markets
Darknet markets have become prominent hubs for the exchange of illicit goods and services, often involving sensitive data and payment information. These marketplaces facilitate transactions that are typically hidden from mainstream financial institutions, making the security and anonymity of user information paramount. The darknet market list serves as a valuable resource for understanding the scope and scale of these underground economies. In particular, the handling of data and payment information on these platforms raises significant concerns regarding privacy, fraud, and law enforcement efforts. Exploring the darknet market list can provide insights into how various sites manage financial transactions and store sensitive user details, which are often targeted by cybercriminals seeking to exploit vulnerabilities. For example, some markets emphasize encrypted communication and secure payment options, while others may neglect proper data protection measures, making user information vulnerable to compromise. Thorough research into the darknet market list is essential for cybersecurity professionals, law enforcement, and investigators working to combat illegal activities in these shadowy environments.
Credit Card and “Fullz” Listings
Darknet markets serve as online platforms where illicit goods and services are traded, often operating under anonymity to evade law enforcement. A critical component of these markets involves the exchange of sensitive data, particularly payment information and personal identifiers. Among the most sought-after offerings are credit card details and “Fullz” listings, which contain comprehensive personal information used for identity theft and financial fraud. Such data is frequently sold or traded on darknet market lists, making these platforms hotspots for cybercriminal activity.
Credit card information available on darknet markets typically includes card numbers, expiration dates, and security codes, often obtained through data breaches or skimming attacks. The sale of this information enables criminals to commit unauthorized transactions or resell the data across different marketplaces. “Fullz” listings, on the other hand, consist of detailed personal data such as full names, Social Security numbers, addresses, dates of birth, and bank account details. This extensive information facilitates identity theft, account hacking, and other fraudulent activities, significantly increasing the potential damage for victims.
Darknet market list compilations frequently feature these data types alongside anonymized payment methods, such as cryptocurrencies, which provide a layer of security for transactions. The availability and variety of data on these lists underscore the persistent threat posed by cybercriminal networks that profit from stolen financial and personal information. Responsible security measures, including vigilant monitoring of financial statements and credit reports, are essential for individuals to protect themselves against the misuse of such data from the darknet marketplace ecosystem.
Average Prices and Variations by Country
Darknet markets are known for facilitating transactions involving stolen data and payment information, often operating outside the boundaries of legal and regulatory frameworks. These platforms typically exchange a variety of sensitive data, including credit card details, login credentials, and personal identification information, which are often sold to malicious actors. The darknet market list provides insight into the types of data in high demand and the prices associated with them, highlighting the illegal economy that thrives in these hidden marketplaces.
Prices for stolen data on darknet markets vary widely based on the type, quality, and the country of origin. For instance, credit card details from economically developed nations such as the United States or European countries tend to fetch higher prices, often ranging from $10 to $50 per card, especially if they offer substantial balances and rewards. Conversely, data from less affluent countries may be sold at lower prices. Personal data, such as full names, addresses, and social security numbers, can also be bought for varying amounts depending on the completeness and sensitivity of the information.
On the darknet market list, stolen payment information and personal data are traded in bulk, with certain markets offering specialized sections dedicated to specific types of data. The variations in prices by country reflect the demand and value placed on that data within cybercriminal communities. These illegal transactions underscore the importance for consumers and businesses to remain vigilant, implement robust cybersecurity measures, and monitor for potential data breaches that can be exploited on the dark web.
Payment Processor and Online Account Listings
Darknet markets are online platforms that facilitate the exchange of various goods and services, often operating outside the boundaries of legal regulations. A crucial aspect of these marketplaces involves the handling of data and payment information, which are typically secured through encrypted channels to maintain user anonymity and safety. When navigating a darknet market list, it is important to understand how payment processes are managed to prevent exposure of sensitive information and avoid legal risks.
Most darknet markets utilize specialized payment processors that support cryptocurrencies, primarily Bitcoin and other digital currencies, due to their pseudonymous nature. These processors enable users to transfer funds securely without revealing personal details, although some markets may implement additional security measures. Proper handling of payment information is essential to prevent scams, theft, and law enforcement detection. Market operators often implement escrow services and multi-signature transactions to protect buyers and sellers during exchanges.
Online account listings on darknet markets typically include details like user ratings, transaction history, and verified statuses. These listings help establish trust among users and streamline the buying and selling process. Since the platforms emphasize privacy, account information is generally limited to pseudonymous identifiers, with some markets offering options to enhance security, such as two-factor authentication. Awareness of these account features, along with the handling of data and payment information, is vital for anyone exploring a darknet market list for informational or research purposes.
Hacked Accounts Available for Sale
Hacked accounts for sale are a prominent and growing concern within the darknet marketplace ecosystem. These illicit transactions involve the trading of compromised credentials, often sourced from data breaches and cyberattacks. The darknet market list plays a significant role in facilitating the exchange of these stolen accounts, offering access to a range of services and illicit goods. Buyers and sellers operate anonymously, making it challenging for authorities to monitor or stop such activities. Exploring the darknet market list reveals the extent of the underground trade in hacking services and stolen digital assets, highlighting the ongoing cybersecurity risks faced by individuals and organizations alike.
Types of Hacked Online Accounts
Hacked accounts available for sale on darknet markets present a significant cybersecurity threat, impacting individuals and businesses alike. These illicit marketplaces facilitate the illegal exchange of compromised accounts, which can include a wide range of online services. Understanding the types of hacked accounts commonly traded on these platforms is essential for users to safeguard their digital assets effectively.
Darknet market lists often feature various categories of hacked online accounts, each serving different malicious purposes. The most frequently found types include:
- Email Accounts: These are often the most sought-after, as they can be used for phishing, spamming, or further hacking attempts.
- Social Media Accounts: Hacked profiles on platforms like Facebook, Instagram, or Twitter are sold for scams, propaganda, or impersonation.
- Financial Accounts: Bank accounts, PayPal, or cryptocurrency wallets are highly valuable on darknet markets, enabling direct financial theft.
- E-commerce Platform Accounts: Accounts on sites like Amazon or eBay can be exploited for fraud or identity theft.
- Gaming and Streaming Accounts: Hacked gaming profiles or streaming accounts provide access to in-game items, subscriptions, or insider information.
The darknet market list also highlights the proliferation of these compromised accounts, reflecting the scale of cybercriminal activity. The sale of hacked accounts is often accompanied by tools or services that facilitate the compromise or exploitation of other accounts, amplifying the risks. Users must remain vigilant and implement robust security measures to prevent falling prey to these illegal transactions. Regularly updating passwords, enabling two-factor authentication, and monitoring account activity are essential steps in defending against unauthorized access.
Understanding the landscape of hacked account sales helps in recognizing the importance of digital security and the ongoing threat posed by darknet marketplaces. Staying informed and cautious can significantly reduce the likelihood of personal or organizational compromise.
Financial and Cryptocurrency Accounts
The darknet market scene has become an increasingly prominent avenue for the sale of hacked accounts, including financial and cryptocurrency accounts. These markets operate in the shadowy corners of the internet, offering a wide range of illicit services and products, from stolen personal information to compromised account credentials. One of the main entries on the darknet market list involves the sale of hacked accounts that can be used for financial gain or fraud.
Hacked accounts available for sale typically include bank accounts, payment service accounts, and cryptocurrency wallets. Cybercriminals often acquire these through phishing, malware, or data breaches, then list them on darknet markets to reach potential buyers seeking easy access to financial resources. Cryptocurrency accounts, in particular, are highly sought after due to the pseudonymous nature of digital currencies, making them attractive for illicit transactions.
Darknet market list entries often feature detailed descriptions of the accounts, including credentials, associated personal information, and sometimes the extent of compromised access. The sale of these accounts poses significant risks to individuals and financial institutions alike, as stolen credentials can lead to identity theft, financial fraud, and money laundering operations.
Law enforcement agencies worldwide continually monitor and take action against darknet market activities, but these marketplaces persist due to their decentralized and encrypted setup. Awareness and security measures are essential to protect personal and financial data from being exploited and to prevent the secondary market for stolen accounts from growing further.
In summary, the darknet market list reveals a disturbing trend of compromised accounts being bought and sold for illicit purposes. Vigilance, strong cybersecurity practices, and timely reporting of suspicious activity are crucial in combating these underground transactions and safeguarding digital assets.
Social Media and Subscription Service Accounts
The darknet market list includes various platforms known for trading illicit goods and services, often operating beyond the reach of standard law enforcement. Among the most concerning offerings found on these markets are hacked accounts available for sale, which include social media profiles and subscription service accounts. These accounts are typically compromised through data breaches or phishing attacks, and their sale poses significant risks to individuals and organizations alike.
Hacked social media accounts listed on darknet markets can be exploited for a range of malicious activities, including spreading misinformation, phishing, or further cyberattacks. Similarly, subscription service accounts, such as streaming platforms or premium memberships, are sometimes sold to gain unauthorized access or resell services at a lower cost. This illicit trade not only compromises user privacy but also undermines the security of online platforms.
The darknet market list serves as a disturbing reminder of the underground economy where stolen data, including hacked accounts, are bought and sold. This ecosystem facilitates cybercriminal activities, promoting identity theft and financial fraud. Awareness of these markets is crucial for individuals and enterprises to implement robust security measures and monitor for signs of unauthorized access to their accounts.
Protecting personal and corporate accounts requires vigilant security practices, including strong, unique passwords and multi-factor authentication. Monitoring account activity regularly and being cautious of suspicious emails can also help prevent unauthorized access. Recognizing the prevalence of hacked accounts for sale on the darknet market list reinforces the importance of cybersecurity awareness and proactive defense strategies in the digital age.
Fake Documents and Identity-Related Data
Fake documents and identity-related data pose significant challenges in the digital landscape, especially within illicit online marketplaces. These counterfeit items are often used for fraudulent activities, making it difficult for authorities and consumers to verify authenticity. The darknet market list features numerous platforms where such illegal goods may be exchanged, emphasizing the importance of awareness and security measures. For those exploring this underground realm, understanding the scope of fake documents within the darknet market list is crucial for navigating these risky environments safely. One example of a marketplace involved in illicit trades is accessible through specialized links, providing insight into the scope of operations involved in counterfeit and illegal goods exchanges.
Scans and Digital Templates
The darknet market landscape includes a wide array of platforms that facilitate the exchange of various goods and services, often operating outside the boundaries of legal regulation. Among the key concerns associated with these markets are the use and proliferation of fake documents and identity-related data, which are frequently used to facilitate transactions and conceal real identities. These counterfeit documents can range from fake IDs and passports to falsified business credentials, making it difficult to verify the legitimacy of users and vendors operating within these environments.
Darknet markets often rely heavily on the exchange of scans and digital templates of fake documents, enabling individuals to acquire identity-related materials quickly and discreetly. These digital templates allow users to generate convincing counterfeit documents tailored to specific needs, which can be used for various illicit purposes such as fraud, identity theft, or bypassing security measures. The availability of high-quality scans and templates has significantly increased the sophistication of fake document offerings, complicating efforts to identify and prevent their misuse.
Within the darknet market list, some platforms may specialize or become known for the trade of fake documents and related data. Such markets typically feature listings that provide detailed images, templates, and instructions for creating counterfeit identification. This proliferation underscores the importance for authorities, organizations, and individuals to remain vigilant and implement robust verification procedures to counteract the threat posed by fake documents and malicious use of digital identity data.
Understanding the trends and common practices surrounding fake documents and identity-related data on darknet markets is crucial for developing effective strategies to combat illegal activities. Enhanced awareness and advanced detection techniques can help mitigate the risks associated with counterfeit documents and uphold the integrity of secure verification systems.
Physical Forged Documents
The darknet market list serves as a comprehensive guide to various online marketplaces operating within the hidden web environment. These markets often facilitate the exchange of goods and services that are typically illegal or restricted in many jurisdictions. One of the critical concerns associated with darknet markets is the proliferation of Fake Documents and Identity-Related Data, which are commonly used to impersonate individuals or bypass security measures. Additionally, these marketplaces are known to trade Physical Forged Documents, such as fake passports, driver’s licenses, and other official identification materials, enabling users to conceal their true identities and engage in illicit activities with reduced risk.
Fake Documents and Identity-Related Data pose significant threats to security and privacy, often being employed in fraudulent schemes, identity theft, and financial crimes. These forged identities can be crafted with high precision, making it challenging for authorities and verification systems to detect deception. Darknet market list entries often include vendors specializing in these products, highlighting the importance of vigilance and awareness in protecting personal and organizational data from such counterfeit materials.
The trade of Physical Forged Documents on these markets undermines governmental and institutional efforts to maintain secure identification processes. These documents are frequently used by individuals involved in illegal activities, such as human trafficking, illegal immigration, or financial scams. Therefore, monitoring and understanding the darknet market list can provide valuable insights into the scale and scope of these illicit operations, aiding law enforcement and cybersecurity agencies in their efforts to combat document fraud and safeguard public safety.
Impersonation and Fraud Use Cases
Darknet markets are online platforms that facilitate the exchange of goods and services, often operating outside the reach of legal authorities. Among the various concerns associated with these markets, the proliferation of fake documents and identity-related data, impersonation, and fraud poses significant risks to individuals, organizations, and governments. These illicit activities undermine trust and can lead to severe consequences for victims, including financial loss and identity theft.
Fake documents and identity-related data are frequently exchanged or sold on darknet market list platforms, enabling malicious actors to authenticate false identities or create convincing counterfeit credentials. Such fake documents can include fake passports, driver’s licenses, birth certificates, and other official papers, which are often used to facilitate criminal activities such as visa fraud, illegal immigration, or financial crimes. Impersonation is a common tactic where criminals use stolen or fabricated identities to access financial accounts, commit fraud, or carry out social engineering attacks.
Fraud use cases driven by these illicit activities are diverse. For instance, scammers may utilize stolen personal information to open accounts or conduct fraudulent transactions, resulting in financial loss for individuals and institutions alike. Darknet market list resources often highlight the availability of such stolen data, making it accessible to a broad range of users. These activities not only damage financial institutions but also compromise personal privacy and security, emphasizing the importance of stringent verification processes and cybersecurity measures.
Combating the misuse of fake documents and identity data requires a multi-layered approach, including advanced identity verification, anomaly detection, and ongoing monitoring of suspicious transactions. Awareness and diligence are essential for individuals and organizations to protect themselves from impersonation and fraud schemes originating from illicit activities on darknet markets. Continuous vigilance and best practices in digital security are key to reducing the impact of these malicious use cases in the evolving landscape of cyber threats.
Malware and Cyberattack Tools on Dark Web
Malware and cyberattack tools have become increasingly prevalent on the dark web, serving as the backbone for cybercriminal activities worldwide. These clandestine marketplaces facilitate the exchange of malicious software, hacking tools, and exploit kits, making it easier for malicious actors to perpetrate cyberattacks. A comprehensive darknet market list helps users navigate these illicit platforms and understand the scope of cyber threats. Among these markets, some are known for specialized services, while others offer a wide range of malicious products. For those seeking information on these hidden markets, the darknet market list provides valuable insights into their structure and offerings, including platforms like the one accessible via this darknet market list.
Malware Distribution Listings
The dark web has become a notorious hub for illicit activities, including the exchange and distribution of malware and cyberattack tools. Darknet markets serve as platforms where cybercriminals can browse, purchase, and sell a wide array of malicious software, ranging from ransomware and spyware to remote access Trojans (RATs) and botnets. These markets often feature detailed listings of malware, providing buyers with specifications, pricing, and user reviews, facilitating the rapid dissemination of cyberattack tools.
One significant aspect of the darknet market list is the proliferation of malware distribution listings, which are often categorized based on functionality or targeted platforms. Cybercriminals utilize these listings to acquire tailored malware that can infiltrate networks, exfiltrate sensitive data, or disrupt operations. The accessibility of such tools through darknet market lists highlights the growing sophistication of cyber threats and the ease with which malicious actors can arm themselves with potent cyberattack instruments.
Darknet markets also sometimes offer tutorials, support, and even compiled malware packages, making it easier for less experienced cybercriminals to carry out attacks. This ecosystem fosters a continuous cycle of innovation in malware techniques, often making detection and defense challenging for cybersecurity professionals. Monitoring ***darknet market list*** helps organizations and authorities understand emerging threats and prepare defensive strategies accordingly.
Overall, the presence of malware and cyberattack tools on darknet marketplaces exemplifies the significant threat landscape faced by individuals, organizations, and governments. Staying informed about the latest offerings within the ***darknet market list*** is critical for cybersecurity efforts aimed at identifying, preventing, and mitigating cyberattacks fueled by malicious software exchanges on the dark web.
Ransomware and System Hijacking
The dark web serves as a hidden marketplace where cybercriminals trade a variety of malicious tools and services, including malware, ransomware, and system hijacking kits. These illicit exchanges elevate the threat landscape for individuals and organizations alike, making it essential to understand the types of threats circulating within darknet markets. Notably, dark web markets often feature a comprehensive list of cyberattack tools that enable hackers to conduct unauthorized intrusions with increased efficiency and anonymity.
Among the most prevalent threats are malware and cyberattack tools, which are frequently exchanged on darknet market lists. Cybercriminals use these platforms to buy and sell malicious software designed for espionage, data theft, or system disruption. Ransomware, a particularly destructive form of malware that encrypts victims’ data and demands payment for retrieval, is a common offering on these markets. System hijacking tools are also available, allowing hackers to take control of devices or entire networks.
The dark web market listings often categorize these malicious tools to attract specific types of cybercriminals. For example, a darknet market list might include:
- Ransomware kits with customizable payloads
- Remote Access Trojans (RATs) for covert control of infected systems
- Phishing kits designed to steal login credentials at scale
- Exploit kits that identify vulnerabilities in software and networks
- Botnet subscriptions used to coordinate large-scale attacks
These offerings facilitate cyberattacks such as distributed denial-of-service (DDoS) attacks, data breaches, and system hijacking, highlighting the importance for cybersecurity professionals to be aware of the tools circulating in darknet market lists. By understanding the scope and nature of these illicit markets, organizations can better prepare defenses against evolving cyber threats tied to darknet activities.
Distributed Denial of Service (DDoS) Attacks
The darknet has become a hub for illicit activities, serving as a marketplace for various illegal goods and services. Among the most concerning aspects of this hidden ecosystem are the availability and sale of malware and cyberattack tools, which are frequently used to conduct malicious activities such as hacking, data theft, and disruption of services. Darknet market lists often feature vendors offering malware kits, exploit scripts, and other cyberattack utilities that can be easily acquired by cybercriminals. These tools can facilitate complex cyberattacks, including Distributed Denial of Service (DDoS) attacks, which overwhelm targeted servers or networks with excessive traffic, rendering them inaccessible. The proliferation of such tools on darknet markets poses significant security threats to organizations and individuals alike.
- Some of the biggest markets have disappeared within just a few weeks in the latter half of 2022.
- You can buy credit card numbers, all manner of drugs, guns, counterfeit money, stolen subscription credentials, hacked Netflix accounts and software that helps you break into other people’s computers.
- What’s known as the dark web exists within the deep web; it’s an area of the internet that is only accessible by users who have a Tor browser installed.
- While Telegram was once a safe haven for illicit activity, recent policy changes have forced many threat actors to reconsider their presence on the platform.
Darknet marketplaces known as darknet market lists serve as repositories for cybercriminals to trade malicious software and expertise. These platforms provide a range of cyberattack tools, from simple malicious code to sophisticated malware strains capable of bypassing security defenses. DDoS attacks, in particular, have become a favored method for extorting businesses or disrupting services, thanks to the ready availability of attack tools on these markets. Criminal operators can purchase or rent botnet networks, which are collections of compromised computers working together to flood a target with traffic. The widespread accessibility of such tools underscores the importance of robust cybersecurity measures and constant vigilance against evolving cyber threats.
Dark Web Marketplaces for Fake Currency and Vouchers
Dark web marketplaces for fake currency and vouchers have become a notorious part of the darknet ecosystem, providing illicit avenues for the purchase and sale of counterfeit financial instruments. These underground platforms cater to individuals seeking to acquire or distribute counterfeit money and compromised vouchers discreetly, often using encrypted communications to maintain anonymity. The darknet market list delineates various marketplaces where such transactions occur, highlighting the breadth and clandestine nature of these operations. Among these platforms, some have gained notoriety for specializing in fake currency and vouchers, making them key points of interest for law enforcement and cybersecurity experts. A *darknet market list* can help track these sites and understand their operational patterns, offering insight into how counterfeit financial goods are circulated in the shadow economy.

Availability of Counterfeit Money
Darknet marketplaces have gained notoriety as platforms where various illicit activities occur, including the trade of counterfeit currency and vouchers. These underground venues often operate in hidden networks, making it difficult for authorities to track and shut down illegal transactions. One of the prominent issues associated with darknet market lists is the availability of fake money, which includes counterfeit bills, digital currencies, and manipulated vouchers designed to deceive consumers or bypass financial controls.
These marketplaces frequently feature a wide range of counterfeit products, with fake currency being one of the most common. Criminal entities utilize sophisticated techniques to produce counterfeit bills or digital money that closely resemble legitimate transactions. The ease of access within darknet market lists has facilitated a thriving black market for such items, making it challenging for consumers and businesses to distinguish genuine currency from forged ones.
Moreover, the availability of counterfeit vouchers on darknet marketplaces further complicates the financial landscape. These vouchers may include gift cards, discount codes, or electronic credits that are illegally sold or hacked from legitimate sources. Buyers are often attracted by the low prices and anonymity these marketplaces offer, but they risk financial loss or legal repercussions when dealing with such counterfeit vouchers.
Overall, the presence of fake currency and vouchers within darknet market lists highlights a significant security concern for individuals and financial institutions alike. It underscores the importance of vigilance and employing robust verification processes to prevent the circulation of counterfeit money in both physical and digital forms. As these illicit markets continue to evolve, ongoing efforts by law enforcement and cybersecurity experts are essential to curb the illicit trade of counterfeit currency circulating on darknet platforms.

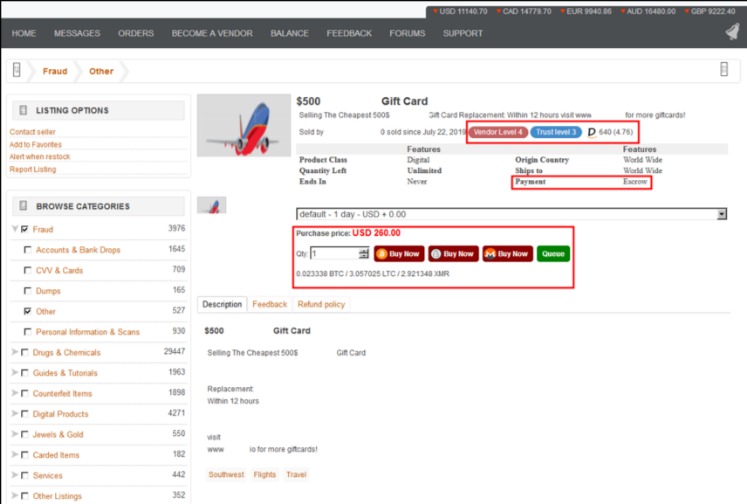
Offferings of Gift Cards and Vouchers
Darknet marketplaces have become notorious for their wide range of illicit activities, including the trade of fake currency and vouchers. These platforms often serve as underground hubs where counterfeit and unauthorized gift cards are bought and sold, posing significant risks to consumers and legitimate businesses alike. The darknet market list highlights these venues, offering a glimpse into the extent of illegal trading occurring beneath the surface of the internet.
Offering counterfeit gift cards and vouchers is a common criminal enterprise within these markets. Buyers seek out compromised or fake vouchers that can be used for online purchases, often at a fraction of their real value. Sellers on darknet marketplaces may provide a variety of fake currency options, including prepaid cards, digital credits, and discount vouchers, all designed to deceive unsuspecting users.
The darknet market list also features vendors dealing in stolen or fraudulent gift cards, aiming to exploit vulnerabilities in online systems. These illegal offerings facilitate money laundering, fraud, and theft, undermining trust in legitimate digital payment methods. Users should remain wary of such transactions, as they are often associated with scams, compromised personal data, and legal consequences.
Given the proliferation of these activities on darknet marketplaces, it is crucial for consumers to exercise caution and verify the authenticity of gift cards and vouchers before making any purchases. Law enforcement agencies continue to monitor and shutdown illegal marketplaces, but the persistent demand fuels a thriving underground industry that thrives on anonymity and secrecy.
In summary, the darknet market list underscores the ongoing issue of fake currency and voucher trafficking, emphasizing the importance of awareness and vigilance to avoid falling victim to these illegal operations.
Quality and Reliability of Fake Currency
Darknet marketplaces are often associated with illegal activities, including the trade of fake currency and vouchers. These markets serve as platforms where counterfeit financial instruments are bought and sold, posing significant risks to buyers and sellers alike. The quality and reliability of fake currency in these environments can vary widely, making it essential for participants to exercise caution. In darknet market lists, some marketplaces have established reputations for offering more trustworthy products, while others are known for frequent scams or low-quality fakes. Buyers should scrutinize reviews and feedback within these lists to gauge the authenticity and reliability of the offerings. Despite the proliferation of such markets, the legitimacy of the fake currency sold remains dubious, and law enforcement agencies continue to crack down on these clandestine exchanges. As a result, traders must understand that the risk of counterfeit bills being detected or rejected is high, and the quality of fake currency can influence the success of transactions. Overall, the darknet market list serves as a crucial resource for identifying the most active and reputed platforms, but users must remain vigilant about the inherent risks involved in purchasing fake currency and vouchers.
Darknet Market Listing of Fraudulent Services
Darknet markets are online platforms that facilitate the exchange of goods and services outside the reach of conventional law enforcement and regulatory authorities. Within these hidden networks, a variety of fraudulent services are often listed, posing significant risks to unsuspecting users. A comprehensive darknet market list provides insights into these illicit avenues, helping users understand the scope and nature of activities taking place behind the scenes. From counterfeit documents to hacking services, these marketplaces are notorious for hosting a wide array of illegal offerings. For those interested in exploring more about these hidden markets, a detailed darknet market list can serve as a valuable resource for research and awareness.
Account Hijacking and Identity Theft Services
Darknet markets have become notorious for hosting a variety of fraudulent services that pose significant risks to individuals and organizations alike. Among the most concerning offerings are services related to account hijacking and identity theft, which facilitate the unauthorized access and misuse of personal and financial information. These markets serve as platforms where cybercriminals can buy and sell illicit services, often operating under the guise of legitimate transactions but ultimately contributing to widespread digital fraud.
The darknet market list often features vendors providing account hijacking services, which involve gaining unauthorized access to email, banking, or social media accounts. These activities can lead to financial loss, reputational damage, and compromised personal information. Likewise, the list includes vendors offering identity theft services, enabling criminals to steal and utilize personal data for fraudulent activities such as applying for credit, conducting illegal transactions, or engaging in further cybercrimes.
Law enforcement agencies and cybersecurity firms continuously monitor the darknet market list to track these illicit services and dismantle networks involved in digital fraud. Awareness and vigilance are crucial for individuals and organizations to protect themselves from falling victim to such schemes. Employing strong, unique passwords, enabling multi-factor authentication, and monitoring financial statements are some measures that can reduce the risk of account hijacking and identity theft.
Overall, the darknet market list highlights the ongoing challenge of combating cybercrime related to fraudulent services. Staying informed about these threats and adopting proactive security practices can make a significant difference in safeguarding digital identities and financial assets from malicious actors operating within these clandestine marketplaces.
Subscription and Streaming Account Hacks
The darknet market list encompasses various platforms where illicit services and products are frequently traded, often operating beyond the reach of conventional law enforcement oversight. These markets are known to facilitate the sale of fraudulent services, such as hacking into streaming accounts, subscription fraud, and other cybercriminal activities. Cybercriminals utilize these marketplaces to offer and purchase compromised credentials, access to hacked accounts, and malicious hacking services.
Among the offerings commonly found on the darknet market list are services that enable users to hack streaming accounts, including popular platforms for entertainment and subscription-based services. These hacking services often promise to provide access to accounts that have been compromised, allowing buyers to enjoy premium content without paying. This practice not only violates the terms of service of legitimate providers but also contributes to revenue loss and security challenges for the affected companies.
Subscription fraud is another prevalent activity facilitated through these markets. Criminal actors purchase or sell stolen account credentials, allowing unauthorized access to various subscription services like music streaming, video platforms, or software licenses. Such activities undermine the security and business models of legitimate service providers, and often lead to financial losses and data breaches.
The darknet market list plays a significant role in the proliferation of these fraudulent activities, providing a centralized platform for traders and buyers to connect under the guise of anonymity. Law enforcement agencies continuously work to monitor and dismantle these illicit markets to combat cybercrime. Awareness of these dark web activities is essential for organizations and individuals to implement robust cybersecurity measures, safeguard personal information, and prevent falling victim to fraudulent services.
Methods Used to Circumvent Security Measures
Darknet markets serve as clandestine platforms where various illicit goods and services are bought and sold, often including fraudulent services that undermine security systems and facilitate criminal activity. The darknet market list frequently highlights these marketplaces, which are designed to operate in secrecy to evade law enforcement and regulatory authorities.
Many vendors offering fraudulent services utilize sophisticated methods to evade detection and circumvent security measures. These tactics include the use of encrypted communications, anonymizing tools, and fake identities to mask their operations. Such measures make it challenging for security systems and investigators to track transactions or identify perpetrators, thereby proliferating illegal activities.
One common method employed by these vendors is the use of encrypted messaging channels that prevent interception and analysis of communications. Additionally, they often utilize cryptocurrencies like Bitcoin to conduct transactions, which provide a higher degree of anonymity and make tracing more difficult. Some also employ fake documents or manipulated digital footprints to mislead investigators and security algorithms.
Other tactics include the frequent changing of digital addresses, the use of proxy servers, and the adoption of obfuscation techniques such as mixing services or coin tumbling, which further complicate efforts to trace the flow of illicit funds. These strategies help fraudulent service providers stay ahead of security measures that aim to detect and shut down illegal operations.
Despite these challenges, law enforcement agencies and cybersecurity firms continue to monitor the darknet market list and develop advanced detection tools. Understanding the methods used to circumvent security measures is crucial for improving cybersecurity defenses and dismantling illicit networks involved in the sale of fraudulent services. Awareness about these tactics is essential for maintaining the integrity of online security and protecting users from potential scams and criminal schemes.
Recent Additions and Novel Listings
Recent additions and novel listings in the darknet market sphere continue to shape the landscape of online clandestine trading. As new platforms emerge and established ones update their offerings, users gain access to an expanding array of products and services. The darknet market list features the latest market entries, reflecting dynamic shifts in availability and security protocols. Staying informed about these updates is crucial for those navigating this complex environment, ensuring they are aware of trusted sources and emerging threats. For a comprehensive overview, explore the latest darknet market list and discover what’s new in this evolving digital underground.
New Categories of Illicit Data and Goods
The landscape of the darknet market continues to evolve rapidly, with recent additions and novel listings shaping the dynamic environment. These markets often introduce new categories of illicit data and goods, reflecting shifting trends and demands within the underground economy. Staying informed about these developments is essential for understanding the current state of the darknet market list and its ongoing transformations. Recent additions include a surge in markets offering specialized products and services that were previously less accessible, highlighting the adaptability of vendors and consumers alike.
New categories of illicit data and goods frequently appear, ranging from sophisticated cyber tools and stolen personal information to illegal pharmaceuticals and counterfeit documents. These categories cater to a broad spectrum of illicit activities and often emerge in response to law enforcement efforts or technological advancements. The emergence of such novel listings underscores the need for continuous monitoring and analysis of the darknet market list to identify evolving threats and trends.
For researchers, law enforcement, and cybersecurity professionals, understanding these recent trends is crucial for developing effective strategies to combat illegal activities. The darknet market list serves as a vital resource, revealing how illicit marketplaces adapt and expand their offerings, introducing new categories of illicit data and goods to meet unmet demands. Vigilant tracking of these developments helps mitigate risks and supports efforts to disrupt illegal enterprises operating within the hidden parts of the internet.
Emergence of New Market Products
The landscape of darknet markets is continuously evolving, with recent additions and novel listings significantly shaping the digital underground economy. Emerging darknet markets introduce innovative features and expanded product categories, catering to a diverse range of user interests and needs. These new platforms often offer enhanced security measures, better anonymity protocols, and more user-friendly interfaces to attract a broader user base. The darknet market list is frequently updated to include these fresh entrants, providing an essential resource for users seeking reliable and up-to-date marketplaces.
The emergence of new market products on darknet platforms reflects broader trends in digital commerce and illicit trade. From pharmaceuticals and digital goods to rare collectibles and niche services, the variety of offerings continues to diversify. These new market products often exploit gaps in regulatory oversight and leverage technological advances to maintain operational security. The darknet market list helps users identify trustworthy marketplaces that feature these novel products, ensuring access to the latest offerings while minimizing risks.
As the darknet ecosystem expands, the introduction of innovative darknet markets and unique product listings underscores the importance of vigilance and continuous information updating. Staying informed about recent additions and new market products allows users and law enforcement agencies alike to monitor trends, identify potential threats, and adapt strategies accordingly. Overall, the darknet market list remains a vital tool in understanding the shifting dynamics of clandestine online trade.
Case Examples of Recently Detected Listings
The landscape of darknet markets is continuously evolving, with new platforms and listings emerging regularly. Recent additions and novel listings reflect the dynamic nature of this clandestine marketplace, often driven by demand for specific products and innovative operational strategies. Monitoring these changes is crucial for understanding trends, assessing risks, and maintaining awareness of key players within the darknet ecosystem.
Case examples of recently detected listings showcase the rapid development of darknet market list offerings. For instance, some newly launched platforms have introduced specialized categories that focus on emerging commodities, such as cryptocurrencies or encrypted communication services. These developments highlight the adaptability of darknet markets to shifting user preferences and regulatory pressures. Additionally, several markets have expanded their inventory by adding unique vendors who offer limited-edition or high-security products, demonstrating the diversification of supply within the darknet.
The darknet market list is a valuable index for researchers and security professionals seeking to monitor the latest activity in these underground networks. Newly detected listings often indicate attempts by vendors to evade law enforcement or to serve niche communities neglected by larger, more established markets. By staying informed about recent additions, stakeholders can better understand the operational strategies and evolving product portfolio of these markets, which often include items ranging from illicit substances to counterfeit documents.