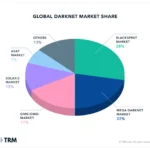
Understanding Darknet Sites
Understanding dark web sites involves exploring hidden digital spaces that operate outside the surface web’s traditional boundaries. These sites, often accessed through special software, provide anonymity for both users and operators, making them a unique environment within the larger internet ecosystem. While some dark web sites serve legitimate purposes such as privacy protection and confidential communication, others are associated with illegal activities. Gaining insight into these sites is essential for cybersecurity efforts, law enforcement, and users interested in online privacy. For example, some well-known darknet sites host forums and marketplaces that can be accessed through specialized browsers, offering both risks and opportunities for those who navigate them.
Definition and Characteristics of Darknet Sites
Darknet sites are specialized online platforms that operate within the deep web, accessible only through specific software or configurations that ensure anonymity and privacy. These sites are often associated with private forums, marketplaces, and communication channels that are not indexed by standard search engines, making them less accessible to the general public. Understanding the characteristics of darknet sites is essential for comprehending their role in online privacy and security.
Darknet sites are distinguished by several key features:
- Anonymity and Privacy: They prioritize user anonymity by utilizing encryption techniques and specialized browsers, such as Tor, which mask IP addresses and other identifying information.
- Restricted Accessibility: Access to darknet sites requires specific software or configurations, often involving virtual private networks (VPNs) and the Tor network, making them inaccessible through regular web browsers.
- Non-Indexing by Search Engines: These sites are not indexed by conventional search engines, which enhances their privacy but also makes discovery more challenging.
- Content Variety: Darknet sites host a wide array of content, including forums, marketplaces, encrypted messaging services, and hacking communities, some of which are involved in illicit activities.
- Security and Confidentiality: Elements such as end-to-end encryption and anonymized communication channels are core to maintaining the confidentiality of users and their activities.
Overall, darknet sites serve as a hub for both legitimate activities related to privacy advocacy and more controversial or illegal operations. Their distinctive features underline the importance of understanding the risks and benefits associated with these hidden parts of the internet landscape.
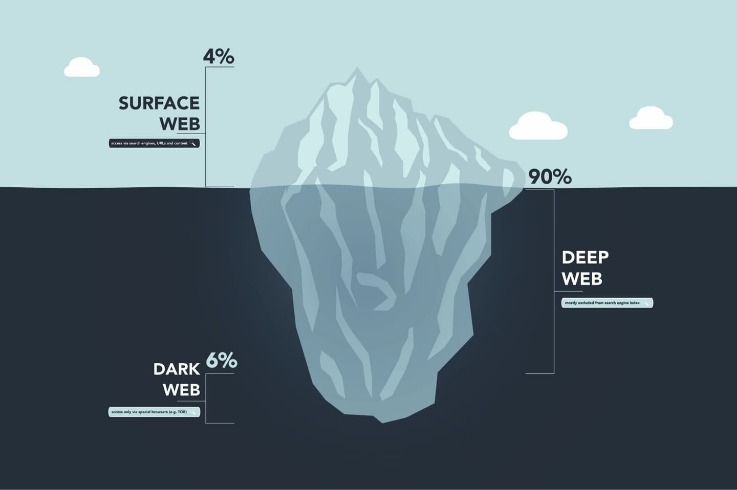
Differences Between Darknet, Deep Web, and Surface Web
The darknet refers to a hidden part of the internet that is not accessible through standard web browsers or search engines. These sites are intentionally concealed and require special software, configurations, or authorization to access, often used for anonymous communication and the exchange of information. Understanding the distinction between the darknet, the deep web, and the surface web is essential for grasping how the internet is structured.
The surface web is the portion of the internet that is publicly accessible and easily indexed by search engines like Google. It includes websites, news portals, social media, and online shopping platforms that can be accessed by anyone with an internet connection. In contrast, the deep web encompasses all online content that is not indexed by search engines, such as private databases, academic resources, banking portals, and password-protected sites. The deep web is significantly larger than the surface web and contains legitimate, non-malicious content that is not meant to be publicly accessible.
On the other hand, the darknet is a subset of the deep web that requires specific tools, such as the Tor browser, for access. It is often associated with anonymous communication and is used both for privacy-focused activities and, unfortunately, for illicit purposes. Darknet sites are intentionally hidden, making them difficult to find unless one knows the exact address or uses specialized search tools. The existence of darknet sites highlights the importance of understanding online privacy, security risks, and the ethical considerations surrounding anonymous networks.
Accessing Darknet Sites
The darknet represents a hidden part of the internet that requires specific tools and knowledge to access. It is often associated with anonymous communication and the sharing of sensitive information. Accessing darknet sites involves using specialized software, such as Tor, which enables users to browse these sites while maintaining privacy and anonymity. Although it offers opportunities for privacy protection, navigating the darknet also involves risks, as some sites may host illegal activities or malicious content. For those interested in exploring this hidden web, there are numerous darknet sites that provide various services and resources. One such site offers secure access to various resources and can serve as a gateway for newcomers to understand the structure and purpose of these hidden networks. Remember, responsible and informed usage is essential when entering these unindexed parts of the internet.
Tools Required for Access (e.g., TOR Browser, VPNs)
Accessing darknet sites requires specialized tools and precautions to ensure safety and privacy. These hidden networks often host content not accessible through regular web browsers, emphasizing the importance of secure methods to navigate them effectively. Understanding the tools necessary is essential for anyone interested in exploring this part of the internet responsibly.
The primary tool used to access darknet sites is the TOR Browser. This browser allows users to connect to the internet anonymously by routing their traffic through a series of encrypted relays. This process masks the user’s location and identity, enabling access to darknet sites that typically operate on the Tor network. Installing and properly configuring the TOR Browser is a critical step for anyone venturing into this domain, providing a layer of privacy and security.
Additionally, virtual private networks (VPNs) are often employed alongside the TOR Browser for enhanced protection. VPNs encrypt internet traffic between the user and the VPN server, adding an extra layer of anonymity. When used together, VPNs and TOR can significantly reduce the risk of tracing activities back to the user, though it is crucial to select reputable VPN providers that do not retain logs.
It’s important to exercise caution when accessing darknet sites, as they are often associated with illegal activities and malicious content. Utilizing the right tools like the TOR Browser and VPNs, combined with good cybersecurity practices, can help mitigate potential risks. Always ensure that your systems are updated, avoid downloading suspicious files, and do not disclose personal information while exploring these hidden parts of the internet.
How Darknet Sites are Hosted and Located
Darknet sites are part of the deep web that is not indexed by traditional search engines and often require specialized tools to access. These sites are typically associated with anonymous activities and are hosted in a way that preserves user privacy and security. Understanding how darknet sites are hosted and located can help shed light on their unique nature and the challenges involved in monitoring or accessing them.

Unlike regular websites that are hosted on publicly accessible servers with easily traceable IP addresses, darknet sites utilize a combination of technologies designed to obscure their location and ownership. These sites often operate on overlay networks such as the Tor network, which encrypts user traffic and routes it through multiple relays worldwide to anonymize both users and hosting servers. This setup makes it difficult for anyone to determine the physical location of the servers hosting these sites.
Darknet sites are generally hosted on servers that are configured to accept traffic only through anonymity-preserving networks. These servers may be operated by individuals, organizations, or communities committed to maintaining their privacy and security. Some hosts intentionally distribute their content across multiple nodes to prevent shutdowns or takedowns. Additionally, the infrastructure involves the use of encrypted communication protocols and decentralized hosting methods, further complicating efforts to track or locate the hosting origins.
The underlying hosting mechanisms often involve specialized software that allows sites to be accessible exclusively through secure, anonymized networks. This approach not only protects the identity of the host but also enhances the privacy of visitors. Despite these measures, law enforcement agencies and cybersecurity professionals employ various techniques to investigate and monitor darknet activity, though the layered anonymity often remains a significant obstacle.
Special Domain Extensions (e.g., .onion)
Accessing darknet sites involves navigating a hidden portion of the internet that is not indexed by traditional search engines and requires special tools and protocols. These sites often utilize unique domain extensions, such as .onion, which are part of the Tor network designed to preserve user anonymity and security. To access these sites safely, users typically need to use specialized software like the Tor Browser, which allows them to connect to the network securely and access onion domains that are inaccessible through standard web browsers.
The .onion domain extension is central to the operation of darknet sites, providing a persistent, encrypted address that maintains user privacy. These domains are generated through a specific process that ensures they are difficult to track or monitor, making them popular for sensitive activities. However, navigating the darknet requires caution, as it can host both legitimate services and illicit content. Ensuring proper security measures and understanding the legal implications are essential for anyone attempting to access these sites.
While the allure of darknet sites includes privacy and anonymity, it is important to recognize their complex nature and potential risks. Users should stay informed about safe browsing practices and the laws applicable in their jurisdictions to avoid unintended legal issues. Accessing darknet sites and their .onion counterparts offers a glimpse into a hidden part of the internet, but responsible usage is key to maintaining security and legality.
Types of Content on Darknet Sites

Darknet sites host a diverse range of content, serving various needs and interests within the hidden parts of the internet. These sites often feature different types of content, from illicit marketplaces and forums to private blogs and information repositories. Understanding the types of content found on darknet sites can help users navigate this obscure digital landscape more safely and effectively. Some darknet sites are dedicated to providing access to anonymous communication platforms, while others serve as hubs for exchanging specialized information or trading goods outside the reach of conventional oversight. For more insights into accessing and exploring darknet content, you can visit darknet portals such as this darknet site. Knowledge of the different categories of darknet sites can aid users in identifying legitimate resources and understanding the scope of content available within these hidden networks.
Legitimate Uses for Privacy and Free Expression

Darknet sites are a distinct segment of the internet that operate on overlay networks, often accessed through special software such as Tor or I2P. These sites host various types of content, some of which are illicit, while others serve legitimate purposes related to privacy, security, and free expression. Understanding the different types of content found on darknet sites helps in recognizing their role in supporting privacy rights and freedom of speech in a digital age.
On darknet sites, you may encounter a varied array of content, which can be broadly categorized into the following types:
- Encrypted Communications and Forums – These platforms provide secure channels for individuals to exchange information anonymously, often used by journalists, activists, and whistleblowers to share sensitive data without risking their identity.
- Private Marketplaces – While some marketplaces facilitate illegal activities, others focus on the trading of legal goods such as digital currencies, rare collectibles, or privacy-focused services.
- Educational and Research Content – Researchers and cybersecurity experts sometimes utilize darknet sites to study cyber threats, host educational material, or develop tools aimed at enhancing digital privacy.
- Public and Personal Blogs – Individuals use darknet sites to publish opinions, personal stories, or advocacy content in a way that shields their identity, promoting free expression especially under oppressive regimes.
- Whistleblowing Platforms – Secure and anonymous platforms on darknet sites enable whistleblowers to reveal corruption, abuses, or misconduct without fear of retaliation.
Although the content on darknet sites includes some illegal material, these platforms also serve crucial legitimate functions. They provide a safe space for privacy, protect free speech, and support sensitive communications in regions with restrictive censorship. Recognizing the diverse types of content on darknet sites highlights their importance as tools for privacy and expression, emphasizing the need to balance security concerns with the fundamental rights to privacy and free speech in the digital realm.
Illegal Activities (e.g., Drug Markets, Data Theft)
Darknet sites host a wide variety of content that often remains hidden from the mainstream internet due to their anonymous nature. These sites serve as platforms for both legitimate and illicit activities, attracting users seeking privacy and anonymity. One significant aspect of darknet sites is the variety of content types available, many of which are associated with illegal operations. Understanding the range of content found on these platforms is crucial for recognizing the scope and risks involved.
Among the most concerning are illegal activities that frequently take place on darknet sites, including but not limited to the operation of illegal drug markets and data theft schemes. These activities exploit the darknet’s anonymity features to facilitate trade and transactions that would otherwise be detected and prosecuted on the open web.
Illegal activities on darknet sites often revolve around the following types of content:
- Drug Markets: These sites function as underground marketplaces where various controlled substances are sold illegally. Buyers and sellers communicate through encrypted channels, and transactions are often completed using cryptocurrencies to avoid detection.
- Data Theft and Black Markets: Forums and marketplaces dedicated to the sale of stolen data, including credit card information, personal identities, and login credentials. These platforms enable hackers and cybercriminals to exchange and purchase sensitive information with relative anonymity.
- Counterfeit Documents and Goods: Darknet sites often facilitate the sale of forged documents such as passports, driver’s licenses, and other identification tools, as well as counterfeit luxury goods.
- Malware and Exploit Kits: Distributors of malicious software and hacking tools engage on darknet sites to offer malware, ransomware, or exploit kits to cybercriminals seeking to compromise systems or conduct attacks.
- Illegal Services: These include hacking services, money laundering, assassin services, and other illicit offerings that cater to criminal needs beyond physical goods.
It is important to acknowledge that while darknet sites provide a space for illegal activities, they also host content related to privacy advocacy, journalistic work, and activism. However, law enforcement agencies continue to monitor and take action against the illegal content often found on these platforms, aiming to curb the proliferation of criminal activities and protect individuals and organizations from harm.
Financial Transactions and Cryptocurrencies
Darknet sites are known for hosting a variety of content that often operates outside the boundaries of conventional legality and regulation. These sites serve as platforms for different types of content, ranging from forums and marketplaces to information sharing and illicit activities. The nature of the content found on darknet sites makes them unique environments that require careful navigation and understanding.
One prominent aspect of darknet sites involves the exchange of financial transactions, often utilizing cryptocurrencies such as Bitcoin and Monero. These digital currencies provide a level of anonymity and privacy that traditional financial systems cannot offer, making them ideal for transactions on the dark web. Cryptocurrency-enabled transactions are a cornerstone of darknet marketplaces, allowing users to buy and sell illicit goods and services securely and discreetly.
Cryptocurrencies have revolutionized financial transactions within these environments, enabling rapid and borderless payments that are difficult to trace. This has facilitated a wide range of activities, including the sale of drugs, counterfeit documents, stolen data, and other illegal commodities. Darknet sites leverage blockchain technology to enhance security and maintain user anonymity, attracting both buyers and sellers seeking discreet exchanges.
Overall, the types of content on darknet sites are diverse and often illicit in nature, with financial transactions predominantly driven by cryptocurrencies. Understanding these dynamics is essential for grasping the critical role that digital currencies and secure online platforms play within this clandestine digital realm. The continual evolution of these sites underscores the importance of cybersecurity measures and legal frameworks to combat illegal activities while respecting privacy rights.
Security and Privacy on Darknet Sites
Darknet sites operate within a hidden segment of the internet, offering a platform for anonymous communication and transactions. Security and privacy are fundamental concerns for users engaging with these sites, as their activities often involve sensitive or illicit content. Protecting user identities and maintaining confidentiality are essential to prevent surveillance, hacking, and potential legal repercussions. Various tools and techniques, such as encryption and anonymity networks, are used to safeguard interactions on darknet sites. However, despite these measures, vulnerabilities still exist, making it crucial for users to stay informed about best practices for maintaining security and privacy in this digital environment. For enhanced privacy features, some users turn to specialized darknet directories and marketplaces that prioritize secure transactions.
Encryption Protocols and Anonymity Measures
Darknet sites operate within a hidden segment of the internet that prioritizes user privacy and secure communications. Ensuring security and privacy on these sites involves a combination of advanced encryption protocols and anonymity measures designed to protect both users and operators from surveillance and malicious attacks. These measures are crucial in maintaining the integrity and confidentiality of activities conducted within this discreet online environment.
Encryption protocols are fundamental to securing data exchanged on darknet sites. These protocols encrypt information transmitted between users and servers, making it virtually impossible for unauthorized parties to decipher sensitive data. Commonly utilized encryption methods include Transport Layer Security (TLS) and end-to-end encryption, which safeguard communications against eavesdropping and tampering. Employing robust encryption ensures that even if data interception occurs, the content remains protected and unreadable.
In addition to encryption, anonymity measures play a vital role in preserving privacy on darknet sites. Technologies such as the Tor network are extensively used to conceal users’ IP addresses and browsing activities. Tor achieves this through a network of relays that reroute internet traffic, making tracing attempts significantly more difficult. Users often leverage tools like virtual private networks (VPNs) and compartmentalized browsing practices to further enhance their anonymity. These measures collectively foster a secure environment where users can operate without fear of identification or surveillance.
Darknet sites implement these security practices not only to protect user privacy but also to defend against cyber threats and law enforcement actions. While these security solutions are vital, they also require diligent management to prevent abuse and ensure safe usage. By continuously updating encryption protocols and anonymity measures, darknet sites aim to uphold a secure and private space for their users.
Best Practices to Protect Personal Information
Operating on darknet sites involves inherent privacy and security risks due to the anonymous nature of these platforms. To safeguard personal information, users must adopt rigorous security measures that help protect their identity and data from potential threats or malicious actors. Understanding the best practices for security and privacy is essential for anyone venturing into or interacting with darknet sites.
Using strong, unique passwords for accounts related to darknet activities is fundamental. Employing password managers can facilitate the creation and storage of complex passwords. Additionally, enabling two-factor authentication wherever possible adds an extra layer of security. It is crucial to avoid sharing identifiable information such as real names, addresses, or phone numbers to minimize the risk of exposure.
Utilizing encryption tools and secure communication channels can greatly enhance privacy. Virtual Private Networks (VPNs) can mask IP addresses and encrypt internet traffic, making it more difficult for third parties to track online activity. However, selecting reputable VPN providers that do not keep logs is important to ensure your anonymity is maintained.
Practicing safe browsing habits includes regularly updating software and security patches, avoiding the download of untrusted files, and being cautious with links and attachments. When accessing darknet sites, it is advisable to use specialized browsers or configurations designed for anonymity, as well as to disable scripts or plugins that could reveal identifying information.
Finally, understanding the importance of operational security (OPSEC) and maintaining compartmentalization between different online identities can prevent full exposure of personal details. By following these best practices, users of darknet sites can significantly reduce the risks to their privacy and personal information while navigating these elusive online spaces.
Risks of Malware, Surveillance, and Data Leaks
Darknet sites operate within a hidden layer of the internet that prioritizes anonymity and privacy. While this environment offers certain protections for users seeking to evade censorship or maintain confidentiality, it also presents significant security and privacy vulnerabilities. Engaging with these sites exposes users to a range of risks, including malware infiltration, government surveillance, and data leaks that can compromise personal safety and anonymity.
One of the primary concerns when accessing darknet sites is the threat of malware. These sites are often targeted by malicious actors who exploit vulnerabilities to distribute harmful software. Malware can lead to unauthorized access to user devices, theft of sensitive information, or even remote control of systems. Users may unknowingly download malicious files or fall victim to scams designed to steal their cryptocurrencies or personal data.
Surveillance is another critical issue associated with darknet site activity. Despite the veil of anonymity, authorities and cybercriminal groups conduct monitoring efforts to track illegal activities and identify individuals. Techniques such as traffic analysis and network analysis can sometimes uncover patterns that lead to de-anonymization, putting users at risk of legal actions or targeted attacks. Therefore, maintaining privacy while navigating these sites requires robust security measures and awareness of potential monitoring efforts.
Data leaks also pose a significant threat on darknet sites. Despite intentions to remain anonymous, users can inadvertently reveal identifying information through insecure practices or compromised sites. Such leaks can result from poorly secured databases, phishing attempts, or accidental disclosure. Once personal details are exposed, individuals may face harassment, legal consequences, or financial loss.
- Use strong, unique passwords and enable two-factor authentication to enhance account security.
- Employ reliable VPN services and use Tor browser to access darknet sites securely and anonymously.
- Be cautious when downloading files or clicking on links to avoid malware infections.
- Regularly update software and security tools to protect against emerging threats.
- Educate yourself about common scams and tactics used by cybercriminals to avoid falling victim.
- Maintain minimal sharing of personal information and be vigilant about privacy settings.
Law Enforcement and Darknet Sites
The dark net has become a complex and often misunderstood part of the internet, where illegal activities and illicit marketplaces frequently operate beyond the reach of conventional law enforcement. Darknet sites serve as hidden platforms for various transactions, some of which raise serious legal and ethical concerns. Law enforcement agencies worldwide continue to monitor and investigate these sites to combat criminal activities, including drug trafficking, arms sales, and cybercrime. Understanding the structure and risks associated with darknet sites is crucial for cybersecurity professionals and the general public alike, as these hidden networks pose unique challenges to maintaining online security and safety. For more information on accessing secure darknet marketplaces, you can visit specialized resources such as this darknet site.
Methods Used to Monitor and Investigate
Darknet sites are hidden parts of the internet that are intentionally concealed and require specific software or configurations to access. These sites are often associated with illicit activities, making them a significant focus for law enforcement agencies. Monitoring and investigating activities on darknet sites pose unique challenges due to their encrypted and anonymous nature. Enforcement bodies employ a combination of technological tools, legal strategies, and international cooperation to combat criminal operations hidden within these clandestine networks.
Law enforcement uses specialized software and techniques to track digital footprints, analyze darknet traffic, and identify individuals or groups engaging in illegal activities. Techniques such as network infiltration, digital forensics, and malware analysis help investigators trace transactions and communications while maintaining operational security. Additionally, they often collaborate with cybersecurity experts to develop tools that can de-anonymize users or uncover hidden servers hosting unlawful content.
Investigating darknet sites also involves extensive use of open-source intelligence (OSINT) and undercover operations. This includes monitoring marketplace listings, forum discussions, and transaction patterns. Law enforcement agencies may also deploy sting operations or undercover agents to gather evidence, disrupt illicit networks, and apprehend suspects. International cooperation among agencies enhances the ability to track cybercriminals who frequently operate across borders, leveraging the decentralized nature of the darknet.
Overall, the surveillance of darknet sites requires a multidisciplinary approach that combines advanced technology, legal authority, and global partnerships. Continued development in cybersecurity techniques is essential to keeping pace with evolving methods used by criminals to evade detection and to ensure that law enforcement can effectively investigate and dismantle illegal activities on the darknet.
Notable Darknet Busts and Operations
Darknet sites are part of an encrypted online network that allows users to communicate and share information anonymously. These sites often operate beyond the reach of traditional law enforcement agencies, making them a focal point for illegal activities such as drug trafficking, weapons sales, illegal pornography, and cybercrimes. Despite the anonymity provided by the darknet, law enforcement agencies worldwide have developed sophisticated techniques to monitor, investigate, and dismantle illegal operations within this hidden digital realm.
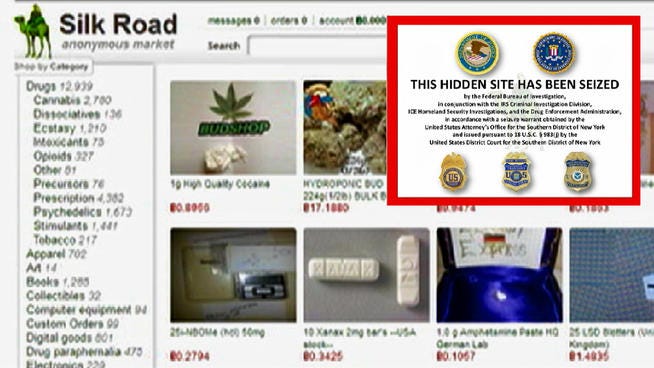
Law enforcement agencies have conducted numerous notable busts and operations targeting illegal activities on darknet sites. These operations often involve undercover investigations, cyber surveillance, and advanced digital forensics to track and identify operators of illicit marketplaces. For instance, coordinated efforts have led to the takedown of large-scale darknet drug marketplaces, resulting in arrests and the seizure of millions of dollars in illegal assets. Such operations demonstrate the persistent commitment of authorities to combat illegal activities facilitated through anonymous online platforms.
One of the most significant law enforcement efforts includes the dismantling of prominent darknet marketplaces known for illicit trade. These operations typically begin with cyber intelligence gathering, followed by infiltration into the marketplace networks, and culminate in coordinated raids and arrests. The success of these efforts underscores the importance of technological expertise and international cooperation in addressing criminal behavior on darknet sites. Continued vigilance and adaptive strategies are crucial as criminals continually evolve their methods to evade detection.
Despite the challenges posed by darknet sites, law enforcement remains committed to maintaining digital safety and combatting criminal activity in cyberspace. By leveraging advanced digital tools and fostering international collaboration, authorities aim to reduce the prevalence of illegal activities on these hidden networks, ultimately making the online environment safer for everyone.
Legal Challenges in Regulating Darknet Activities
Darknet sites operate on anonymity networks that enable users to access hidden parts of the internet, often for purposes ranging from privacy advocacy to illicit activities. The secretive nature of these sites presents significant challenges for law enforcement agencies seeking to regulate and combat illegal behaviors conducted within these spaces.
One of the primary legal challenges in regulating darknet sites is the difficulty in identifying and locating individuals involved in unlawful activities. The use of encryption and anonymizing tools such as Tor hampers efforts to trace criminal transactions and communications. Consequently, authorities face hurdles in collecting concrete evidence and building cases against offenders.
Legal frameworks often struggle to keep pace with the rapidly evolving technology used by darknet sites. Existing laws may not explicitly cover the nuances of activities conducted in anonymous networks, creating gaps that can be exploited by criminals. This situation necessitates continual updates to legislation and the development of specialized investigative techniques.
International cooperation also plays a crucial role since darknet activities frequently span multiple jurisdictions. Coordinated efforts between law enforcement agencies across countries are essential to dismantle illegal operations hosted on darknet sites effectively. However, varying legal standards and priorities can complicate such collaborations.
Ultimately, regulating darknet sites involves balancing the enforcement of laws with respect for privacy rights and digital freedoms. As technology advances, legal challenges will persist, demanding innovative solutions and robust legal frameworks to address criminal activity while upholding civil liberties.
Legal and Ethical Considerations
Engaging with darknet sites raises numerous legal and ethical considerations that individuals must carefully evaluate. While these hidden corners of the internet can offer privacy and anonymity, they also pose significant risks related to unlawful activities and ethical boundaries. It is crucial to understand the legal frameworks governing access and use of darknet sites to avoid inadvertent involvement in criminal behavior. Additionally, ethical concerns surrounding privacy rights, data security, and the potential for supporting illicit markets must be taken into account. Navigating these issues responsibly ensures that users remain within the bounds of the law and uphold moral standards when exploring the depths of the darknet, such as darknet sites that host sensitive or controversial content. Familiarity with these considerations helps foster a safer, more conscientious approach to online exploration and digital security.
Legality of Accessing Darknet Sites
Accessing darknet sites raises important legal and ethical considerations that users should carefully evaluate. The dark web hosts a variety of content and services, some of which operate within the boundaries of the law, while others engage in illegal activities. It is crucial to understand the legal implications of entering these environments to avoid potential criminal charges or other legal consequences. Laws regarding access to darknet sites vary by jurisdiction, with some countries explicitly prohibiting the use of anonymizing networks or penalizing activities such as illicit drug sales, hacking, or distribution of illegal content. Ethical considerations also come into play, as engaging with or supporting illegal operations on these sites can contribute to harmful activities and undermine societal norms of legality and morality. Users should always ensure they are complying with local laws and refrain from participating in any illegal transactions or activities. Being aware of the risks and maintaining ethical standards is fundamental when exploring the darknet, as it can pose significant legal and moral challenges that require responsible behavior and informed decision-making.
Privacy Rights Versus Criminal Activities
Darknet sites operate within a complex landscape of legal and ethical considerations that significantly impact users and operators alike. These hidden online spaces often facilitate a range of activities, some of which are lawful, while others are illegal and pose serious concerns for society. Navigating this environment requires a clear understanding of privacy rights and the potential for criminal misuse. While many individuals use darknet sites to preserve anonymity and protect their privacy, these same features can enable illicit activities such as drug trafficking, arms distribution, and cybercrime.
One of the primary challenges associated with darknet sites is balancing the right to privacy with the need to prevent criminal activities. Privacy rights are fundamental, allowing individuals to communicate securely and maintain confidentiality, especially in oppressive regimes or sensitive situations. However, this same privacy can shield criminal actors from law enforcement efforts, making it difficult to combat illegal behaviors effectively. Law enforcement agencies often face ethical dilemmas when attempting to investigate crimes on darknet sites, as intrusive measures may infringe upon privacy rights and civil liberties.
Legal frameworks surrounding darknet activities vary by jurisdiction, but generally, engaging in or facilitating illegal activities on these sites constitutes criminal behavior. Authorities worldwide are continually developing strategies to detect and dismantle illegal operations while striving to respect legal boundaries and privacy rights. Ethical considerations also extend to the impact on victims of illegal activities, as enforcement agencies aim to suppress harmful practices without unjustly infringing on the rights of innocent users.
In conclusion, the existence of darknet sites highlights a tension between protecting individual privacy and preventing criminal conduct. Ethical and legal standards must evolve to address these challenges, ensuring that measures taken are proportional, respect human rights, and effectively combat illegal activities without overreach. Navigating this delicate balance remains a vital aspect of law enforcement and societal responsibility in the digital age.
Responsibility and Risks for Users
Engaging with darknet sites involves significant legal and ethical considerations, along with understanding the responsibilities and risks associated with their use. Due to the anonymous nature of these sites, users may encounter scenarios where their actions could lead to legal complications or ethical dilemmas. It is crucial to be aware of the laws governing internet use within your jurisdiction, as accessing certain content or services on darknet platforms may be illegal and subject to prosecution. Ethical considerations also come into play when contemplating the impact of activities conducted on darknet sites, including respecting privacy boundaries and refraining from participating in illicit transactions.
Users of darknet sites carry various responsibilities to ensure they do not inadvertently support illegal activities or cause harm. These responsibilities include being cautious about the type of information shared, avoiding engagement in criminal enterprises, and maintaining ethical standards in online conduct. Navigating the risks involved requires vigilance against potential security threats such as scams, malware, and identity theft, which are prevalent on these platforms. There is also a risk of exposure to disturbing content or unlawful markets, which can have serious legal ramifications and personal consequences if uncovered.
- Understanding and complying with local laws related to internet usage and digital activities.
- Avoiding participation in illegal transactions or forums that facilitate criminal activities.
- Practicing good cybersecurity hygiene to protect personal data and digital identities.
- Being aware of the ethical implications of accessing or sharing sensitive or illicit content.
- Recognizing the potential for encountering scams, malware, or malicious actors and taking appropriate precautions.
- Considering the broader impact of one’s actions, including supporting the safety and integrity of online environments.
In summary, navigating darknet sites requires a responsible approach that respects legal boundaries and ethical standards. Users must be aware of the risks involved and take steps to safeguard themselves while avoiding actions that could lead to legal trouble or cause harm to others. Staying informed and cautious is essential when exploring these hidden corners of the internet to ensure a safe and lawful experience.
Emerging Trends and Future of Darknet Sites
- In addition to the critically important efforts of the German Federal Criminal Police, significant assistance was provided by the Justice Department’s Office of International Affairs and the U.S.
- In doing so, Pavlov is alleged to have facilitated Hydra’s activities and allowed Hydra to reap commissions worth millions of dollars generated from the illicit sales conducted through the site.
- However, individuals do not have to use the dark web to purchase cryptocurrencies.
- Parsarad was also indicted by a federal grand jury in the Northern District of Ohio on drug trafficking charges related to the illegal business he ran on the dark web.
The landscape of darknet sites is constantly evolving, reflecting broader trends in technology, security, and user behavior. As privacy concerns grow and cybercriminal activities become more sophisticated, new patterns are emerging that indicate the future trajectory of these hidden online communities. Innovations such as enhanced anonymity measures and decentralized networks are shaping how darknet sites operate and interact. One example of such development is the increasing use of specialized gateways and encrypted communication channels that bolster user safety. As the darknet continues to adapt, understanding these emerging trends is crucial for both security professionals and users interested in the implications of this shadowy digital realm. Exploring a variety of darknet sites, such as this platform, reveals the diversity and technological advancements within this clandestine ecosystem.
Impact of New Technologies (e.g., Enhanced Encryption)
Darknet sites have long been associated with clandestine activities, but recent technological advancements are shaping their evolving landscape. As the digital realm continues to innovate, darknet platforms are adapting to new security measures and user needs, signaling significant shifts in their future development. Emerging trends indicate a move towards more sophisticated methods of anonymity and privacy preservation, making these sites more resilient against surveillance and takedown efforts.
One of the most influential factors impacting darknet sites is the rise of enhanced encryption technologies. Advanced encryption algorithms and protocols now provide users with increased protection, making it more difficult for law enforcement and third parties to monitor activities. This heightened security fosters greater anonymity, encouraging more users to engage with darknet content confidently, while simultaneously complicating efforts to regulate or shut down illicit operations.
Additionally, innovations such as decentralized hosting, blockchain integration, and privacy-focused network architectures are emerging as pivotal in shaping the future of darknet sites. These technologies aim to distribute data across multiple nodes, reducing vulnerability points and enhancing resistance to censorship. As a result, darknet platforms are expected to become more resilient, persistent, and harder to track, potentially evolving into more secure and autonomous ecosystems.
Furthermore, the incorporation of new technologies is likely to influence the types of activities conducted on darknet sites. Enhanced privacy features could facilitate not only illicit transactions but also protect activists, journalists, and whistleblowers sharing sensitive information under oppressive regimes. This duality highlights the complex impact of technological innovations, balancing the need for security with the potential for misuse.
Looking ahead, the future of darknet sites will undoubtedly be shaped by ongoing technological progress and the choices made by both cybersecurity defenders and malicious actors. As encryption and privacy-preserving technologies become more sophisticated, these sites will continue to evolve, posing ongoing challenges and opportunities for law enforcement, policymakers, and the global community focused on internet security and freedom.
Potential for Law Enforcement Collaboration
The landscape of darknet sites is continuously evolving, driven by technological advancements, shifting user behaviors, and emerging security concerns. As these sites become increasingly sophisticated, their role in illicit activities but also in safeguarding privacy and free expression continues to attract attention from both law enforcement agencies and cybersecurity experts. Understanding the emerging trends and the potential for future developments is crucial for developing effective strategies to address the challenges associated with the dark web.
One significant trend is the rise of more decentralized and anonymized platforms that aim to enhance user privacy while reducing the risks of detection. These sites often leverage advanced encryption techniques and innovative routing methods to obscure user identities and locations. The development of more resilient and resilient networks suggests that darknet sites will become harder to infiltrate, posing new challenges for law enforcement efforts.
Additionally, there is an increasing convergence of blockchain technology with darknet activities, which introduces new avenues for illicit transactions and data exchange. Cryptocurrencies remain a primary means of transaction on these sites, and their integration with more complex smart contract systems could facilitate more covert and automated operations. This convergence raises questions about future detection methodologies and the need for more sophisticated investigative tools.
In terms of law enforcement collaboration, there is growing recognition of the importance of interdisciplinary approaches that combine cyber intelligence, technological expertise, and international cooperation. Collaborative efforts around emerging trends in darknet sites include sharing intelligence, improving tracing techniques, and developing proactive measures to disrupt illegal activities without infringing on privacy rights. Such partnerships are key to addressing the transnational nature of darknet operations.
Looking ahead, future developments in darknet sites may involve the integration of artificial intelligence to enhance security and automate various functions, making these sites more resilient. Conversely, advancements in detection algorithms and law enforcement tools are also expected to improve, enabling more effective monitoring and intervention. As this dynamic environment continues to evolve, ongoing innovation and cooperation will be vital in balancing privacy rights with security concerns.
Ongoing Challenges in Combating Illicit Activities
The future of darknet sites is poised to undergo significant transformations driven by technological advancements and evolving security measures. These hidden online spaces continue to serve as platforms for both legitimate privacy needs and illicit activities, presenting ongoing challenges for law enforcement agencies worldwide. As encryption technologies become more sophisticated, maintaining anonymity on the darknet becomes increasingly feasible for users, complicating efforts to track and dismantle illegal operations.
Emerging trends indicate a shift towards more decentralized and resilient darknet networks, which use blockchain and peer-to-peer technologies to enhance security and reduce reliance on centralized servers. This makes shutting down or monitoring such sites more complex. Additionally, the adoption of artificial intelligence and machine learning tools by both cybercriminals and security agencies is transforming how activities are detected and prevented, creating a digital arms race.
Despite advancements, combating illicit activities on darknet sites remains a formidable challenge. The anonymous nature of these platforms allows for a range of illegal dealings, including drug trafficking, weapons sales, and fraudulent schemes. Efforts to monitor illicit activities often face obstacles due to the use of encrypted communications and anonymization techniques like Tor, which hinder traditional investigative methods.
Looking ahead, the dark web is likely to evolve with new privacy-preserving technologies that further complicate law enforcement efforts. Finding a balance between protecting user privacy and addressing criminal activities continues to be a critical issue. Strategies combining technological innovation, international cooperation, and legal frameworks are essential to address the complexities of maintaining security while respecting privacy rights.
Overall, as darknet sites adapt to changing digital landscapes, ongoing vigilance and innovative approaches will be necessary to effectively combat illicit activities and ensure safer online environments for all users.