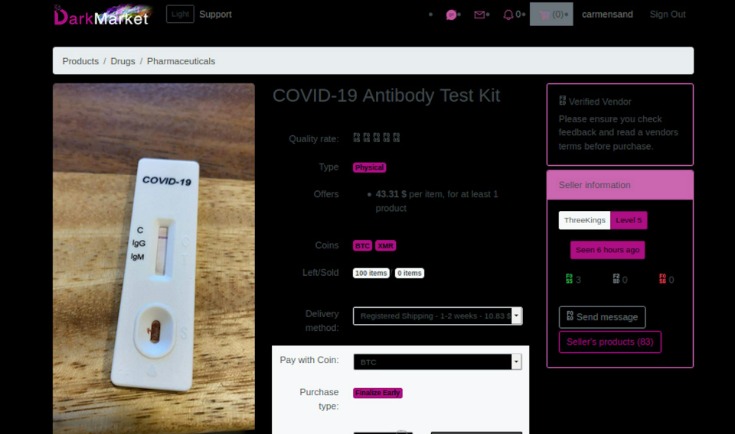
Understanding Darknet Websites
The darknet consists of a segment of the internet that is not indexed by traditional search engines and requires specific tools to access. Darknet websites are often associated with anonymous browsing and encrypted communications, enabling users to operate with increased privacy. These sites serve various purposes, from legitimate privacy-focused activities to illicit endeavors. Understanding how darknet websites work and their role within the broader internet landscape is essential for recognizing both their benefits and risks. For those interested in exploring this hidden part of the internet, there are numerous resources and directories that can provide access and guidance.
Definition and Characteristics of Darknet Websites
Darknet websites are a part of the hidden segment of the internet that is not accessible through standard search engines or ordinary browsing methods. They operate on overlay networks, often using specialized software to ensure anonymity and privacy for both hosts and visitors. These websites are designed to be difficult to locate and monitor, making them suitable for various activities that require secrecy.
Understanding the characteristics of darknet websites is essential to grasp their role in the broader internet ecosystem. These sites typically use encryption and routing techniques, such as those provided by the Tor network, to conceal the identities of users and operators. Unlike conventional websites that are indexed by search engines, darknet websites are deliberately hidden and do not appear in public search results.
Some key features of darknet websites include their use of anonymizing technologies, high levels of security measures, and their tendency to host content that might be illegal or sensitive in nature. These websites may serve as platforms for privacy-focused communication, but they have also gained notoriety for facilitating illegal trade and other illicit activities. Their unique setup ensures that monitoring and regulation are challenging, making them a complex aspect of internet security and law enforcement efforts.
Comparison Between Darknet, Deep Web, and Surface Web
The internet is a vast and complex space that extends beyond the surface web accessible through common search engines. Among its many layers, the darknet represents a hidden part of the internet that is often associated with anonymous activities and illegal operations. Understanding what darknet websites are and how they differ from other parts of the web is essential for comprehending the broader digital landscape.
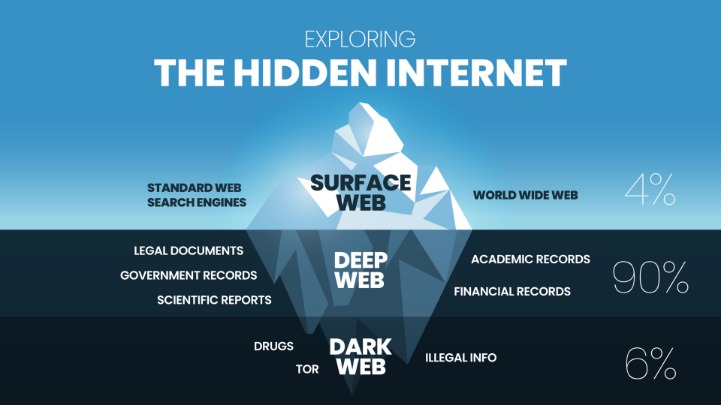
The darknet is a subset of the deep web, which includes all web pages not indexed by standard search engines. Unlike the surface web, which is easily accessible and indexed, the deep web contains private databases, administrative pages, and other content meant to remain hidden from public view. The darknet, on the other hand, is intentionally hidden and requires specific software and configurations for access, often emphasizing anonymity and privacy.
Darknet websites are typically accessed through specialized networks like Tor or I2P, which mask user identities and website origins. These sites often use encrypted and concealed communication channels to maintain privacy and anonymity, making them a haven for both privacy-conscious users and malicious actors. While some darknet websites serve legitimate purposes such as protecting dissidents or journalists in oppressive regimes, many are associated with illegal activities including black markets, illicit exchanges, and hacker forums.
In contrast, the surface web consists of websites that are publicly available and easily accessible through standard browsers and search engines. These sites are indexed and linked, making them readily discoverable by anyone with internet access. The deep web includes confidential or private data that is not intended for public viewing but is not necessarily illicit, such as academic databases, personal email accounts, or banking information.
Understanding the distinctions between these layers of the internet helps clarify the role each plays in digital security and privacy. While the surface web offers transparency and accessibility, the deep web and darknet prioritize privacy and control over distribution. Recognizing darknet websites as a separate and often clandestine sphere underscores the importance of cybersecurity awareness for users navigating online space securely and responsibly.
Access Methods and Tools for Darknet Websites
The darknet comprises a part of the internet that is not indexed by traditional search engines and requires specific tools and access methods to explore. It is often associated with anonymous communication and privacy-focused activities, making it a unique segment of the online world.Darknet websites are hosted on overlay networks that utilize encryption and anonymity layers to conceal user and server identities. These websites are accessible only through specialized software and configurations, which differentiate them from conventional websites.
Accessing dark web content typically involves using tools such as the Tor browser, which allows users to navigate through a series of relays to obfuscate their location and identity. Other tools include I2P (Invisible Internet Project) and Freenet, each offering distinct ways to connect securely and anonymously. These platforms enable users to reach darknet websites and participate in private communications or transactions without revealing personal information or exposing their digital footprints.
Darknet websites often employ particular technologies and protocols to enhance their security and anonymity. This includes using hidden services that operate within the Tor network or other similar overlays. Access methods require understanding how these tools operate and establishing secure connections through configuration settings tailored to preserve privacy and avoid tracking. Employing these tools and understanding their functionalities are essential for safely navigating the darknet and accessing its websites.
Types and Purposes of Darknet Sites
The darknet consists of a collection of networks that operate on overlay protocols, providing anonymous communication channels beyond the reach of traditional internet surveillance. These sites serve various purposes, ranging from safeguarding privacy to facilitating illicit activities. Darknet websites are often designed to protect user identities and enable secure transactions, making them appealing for both legitimate use and nefarious intent. Some sites are dedicated to activism and free expression, while others focus on black market trading or illegal content exchange. For more insights into the diverse functions of darknet sites, explore this darknet platform.
Legitimate Uses: Privacy, Censorship Circumvention, and Whistleblowing
Darknet sites are specialized websites operating on overlay networks that require specific software, configurations, or authorization to access. These sites are often associated with clandestine activities but also serve legitimate purposes in various contexts. Understanding the different types and purposes of darknet sites is essential to appreciate their roles in the digital landscape.
One primary type of darknet site is those used for privacy-focused communication and research. These sites enable users to maintain anonymity and safeguard their identities, which is crucial for journalists, activists, and individuals living under oppressive regimes. By providing secure channels for exchange, darknet websites facilitate free expression without fear of censorship or retaliation.
Another significant purpose of darknet sites is censorship circumvention. In regions where government authorities heavily control the flow of information, accessing information through darknet platforms allows users to bypass restrictive barriers. This enables important news and independent voices to reach audiences despite governmental suppression.
Darknet sites also serve as platforms for whistleblowing, offering a safe environment for individuals to leak sensitive information without revealing their identities. Whistleblowers can share evidence of corruption, human rights violations, or other misconduct, empowering transparency and accountability. These sites help protect sources who might otherwise face repercussions.
While some darknet sites are linked to illegal activities, many serve as vital tools for protecting privacy, promoting freedom of speech, and supporting transparency. Their existence underscores the balance between open access to information and the need for security and anonymity in the digital age.
Illicit Activities: Markets, Illegal Content, and Cybercrime Forums
Darknet sites are specialized online platforms that operate on overlay networks, such as the Tor or I2P networks, providing users with increased privacy and anonymity. These sites serve a variety of functions, each catering to different needs and communities. Understanding the types and purposes of these sites is essential to grasp the complex landscape of the darknet.
One primary category of darknet sites includes marketplaces that facilitate the buying and selling of illegal goods and services. These markets often specialize in the distribution of drugs, weapons, counterfeit currency, and stolen data. Such marketplaces operate under strict secrecy, using cryptocurrencies for transactions to maintain anonymity. They play a significant role in the facilitation of cybercrime and illegal trade on the darknet.
Another common type consists of sites hosting illegal content, such as pirated media, child exploitation material, and other restricted or prohibited materials. Accessing and distributing such content is a criminal offense in many jurisdictions, and these darknet sites enable users to share and obtain illicit content covertly. This environment makes it difficult for authorities to track and shut down these operations.
Cybercrime forums are also prevalent on darknet websites and serve as hubs for hackers, scammers, and cybercriminals. These forums facilitate discussions on hacking techniques, malware development, and exploit selling. They provide a platform for collaboration, resource sharing, and the exchange of stolen information, thus fueling a broader ecosystem of cybercriminal activities.
Overall, darknet sites serve multiple purposes, from providing anonymity to facilitate illegal activities to serving as community spaces for cybercriminals. While some utilize these platforms for privacy concerns and activism, their association with illicit activities remains a significant concern for law enforcement and cybersecurity professionals.
Platforms for Secure Communication and Hidden Services
The darknet is a segment of the internet that is not indexed by standard search engines and requires specialized software to access. It hosts a variety of sites that serve different purposes, often emphasizing privacy and anonymity. These sites can be classified into several types based on their functions and intended users. Understanding the different categories and the platforms used for secure communication is essential for grasping the complex nature of darknet sites.
One primary type of darknet site is the marketplace, where vendors sell a range of products, including both legal and illegal goods. These platforms typically operate anonymously, using encryption to protect the identities of both buyers and sellers. Another category includes forums and communities where individuals discuss sensitive topics, share information, or collaborate in secure environments. These platforms facilitate anonymous discussions on topics such as activism, privacy rights, or illicit activities.
Hidden services on the darknet also include hosting platforms for various services that require high levels of security and anonymity. These services can range from private messaging systems to file sharing platforms, designed to protect users from surveillance and censorship. Such sites often utilize onion routing technology, providing a layered encryption system that helps obscure user identities and locations.
Platforms for secure communication are vital in the darknet ecosystem. They include encrypted messaging services and anonymous email providers, which enable users to communicate without revealing their identities. These platforms use sophisticated encryption protocols to ensure that messages and other exchanges remain private and resistant to interception or tracking. Such platforms are essential for activists, journalists, and others who need to maintain confidentiality in hostile environments.
In summary, darknet sites serve diverse purposes, from facilitating anonymous commerce and communication to hosting sensitive discussions. The underlying platforms for these hidden services prioritize security, privacy, and anonymity, enabling users to operate discreetly in a complex digital landscape. Understanding these types and platforms provides insight into the structure and purpose of darknet websites and the vital role they play in safeguarding privacy in the digital age.
Common Features of Darknet Websites
Darknet websites are known for their unique features that set them apart from traditional internet sites. These platforms often prioritize anonymity and privacy, utilizing specialized networks and encryption to protect user identities. Many darknet websites are accessible exclusively through Tor or other anonymizing networks, making them difficult to locate and monitor. Common characteristics include the use of hidden services with encrypted domains and the lack of identifiable registration information. Some darknet websites also employ varied security measures to prevent unauthorized access or infiltration. For those interested in exploring the hidden parts of the web, a reputable darknet marketplace or resource is available for secure browsing. An example of such a platform can be found here. Understanding these features is essential for anyone seeking insights into how darknet websites operate and the precautions needed to navigate them safely.
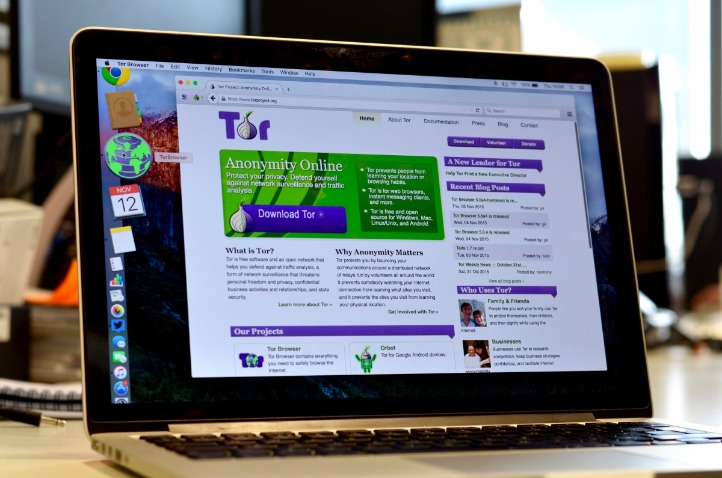
Encrypted Communications and Anonymity Technologies
Darknet websites are specialized online platforms that operate within the hidden parts of the internet, often hidden from standard search engines and requiring specific configurations to access. These sites are characterized by their commitment to privacy and security, making them popular among users seeking anonymity for various reasons. A common feature of darknet websites is their reliance on encrypted communications and robust anonymity technologies to protect both operators and visitors from identification and surveillance.
One of the key features of darknet websites is the use of encrypted protocols that safeguard data exchange from interception or tampering. Encryption ensures that any information transmitted between users and the website remains confidential, providing a secure environment in which sensitive activities can occur. This layer of security is essential for maintaining privacy in environments where anonymity is paramount.
To maintain user anonymity, darknet websites often employ advanced anonymity technologies such as the Tor network or I2P. These technologies route internet traffic through multiple relays and encrypt data at each stage, making it extremely difficult to trace user activities back to their origin. This multi-layered approach helps prevent both tracking and censorship, creating a shielded browsing experience for users seeking discretion.
Additionally, encrypted communication tools are commonly integrated into darknet websites, including encrypted chat, messaging, and data-sharing capabilities. These tools further enhance operational security by ensuring that even if data is intercepted, it remains unreadable without the proper decryption keys. As a result, darknet websites foster an environment where privacy is prioritized above all else.
Overall, the combination of encrypted communications and sophisticated anonymity technologies makes darknet websites distinct in their operational features. These elements not only secure user interactions but also sustain the secretive nature of these sites, supporting activities that rely heavily on privacy and confidentiality. The secure and anonymous environment established by these common features is what defines the core functionality of darknet websites.
Decentralized Hosting and Hidden Services
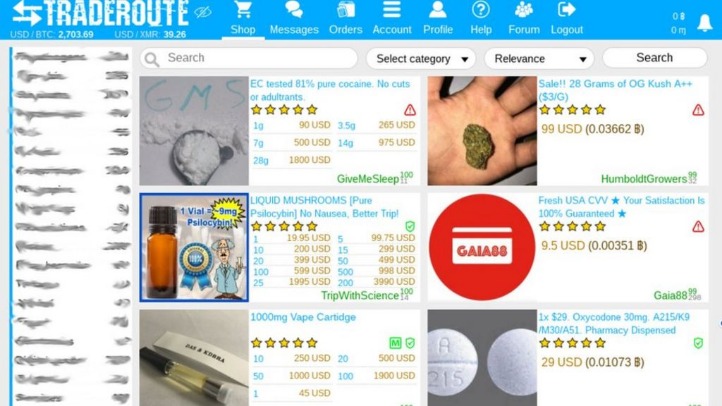
Darknet websites are specialized online platforms that operate within the hidden parts of the internet, often accessed through anonymizing networks. These websites are characterized by several common features that distinguish them from traditional websites, primarily centered around privacy, security, and anonymity. A key feature of darknet websites is their use of technologies designed to mask both the hosting infrastructure and user identities, making surveillance and tracking challenging.
One prominent feature of darknet websites is their reliance on decentralized hosting. Unlike conventional websites that are hosted on centralized servers, many dark web sites employ decentralized systems that distribute data across multiple nodes or servers. This decentralization enhances resilience against takedown efforts and censorship, ensuring the accessibility and persistence of these sites despite attempts to shut them down.
Another important characteristic is the use of hidden services. These are special types of websites that are intentionally concealed through encryption and routing techniques, often accessible only via specific software such as Tor. Hidden services provide strong anonymity for both operators and visitors, allowing activities to remain private and reducing the risk of infiltration or surveillance.
Darknet websites typically feature minimalistic design, primarily focusing on security protocols rather than aesthetics. They often employ encrypted communication channels and pseudonymous identities to protect user privacy. The combination of decentralized hosting and hidden services contributes significantly to the resilience and anonymity of these platforms, making them suitable for a range of activities that require discretion.
Overall, the common features of darknet websites—decentralized hosting, hidden services, and enhanced privacy measures—underscore their role in facilitating anonymous communication and maintaining operational resilience in the face of external pressures. These attributes are central to understanding how the dark web functions as a separate and often secretive layer of the internet.
Addressing and Navigation on the Darknet
Darknet websites are specialized online platforms that operate on hidden parts of the internet, often requiring specific knowledge and tools to access. These sites are distinct from traditional websites due to their unique features related to privacy, anonymity, and security. Understanding the common features of darknet websites is essential for recognizing how they function and how users navigate within these covert realms.
One of the primary characteristics of darknet websites is their use of encryption and anonymity networks such as Tor or I2P. These networks route user traffic through multiple servers, making it difficult to trace the origin or destination of the connection. This layer of protection allows darknet sites to maintain a high level of confidentiality for both operators and visitors.
Darknet websites often employ specific address formats that differ from standard URLs. Typically, these addresses are random strings of characters ending with specialized domain extensions such as .onion or .i2p. These addresses are not indexed by traditional search engines, requiring users to know or obtain the exact URL through trusted sources or directories.
Navigating on darknet websites usually involves careful use of search tools or directories dedicated to the hidden internet. Users often rely on community forums, word of mouth, or specialized search engines designed for the darknet. It is important to recognize that these sites may have a cluttered or intentionally obscure layout, emphasizing security and anonymity over user experience.
Common features of darknet websites include encrypted communication channels, minimalistic design focused on security, and often, a need for authentication mechanisms such as login credentials or captcha verification to access specific content. The content hosted on darknet sites can range from forums and marketplaces to more illicit activities, making them a complex aspect of the broader internet landscape.
Overall, darknet websites are characterized by their emphasis on privacy and security, along with their unique addressing and navigation methods. These features collectively support the purpose of maintaining anonymity and protecting the identities of both operators and visitors within the hidden internet ecosystem.
Security Concerns and Risks Associated with Darknet Websites
Darknet websites operate within a hidden segment of the internet, often associated with illicit activities and anonymous communication. While they provide privacy and protect user identity, they also pose significant security concerns and risks for users and stakeholders alike. These sites can be vulnerable to cyberattacks, hacking, and data breaches, which can lead to the theft of sensitive information. Additionally, the anonymous nature of darknet websites makes them attractive platforms for illegal transactions, fraud, and other malicious activities that undermine online security and trust.
One of the major risks associated with darknet websites is exposure to malicious software and scams that can compromise personal data and financial resources. Users often navigate these sites unaware of potential threats, increasing their susceptibility to malware, phishing attacks, and scams. For instance, accessing important services or marketplaces on darknet sites like Darknet marketplaces can expose users to these hazards, emphasizing the importance of cautious browsing and security measures. Overall, while darknet websites can serve legitimate privacy needs, the inherent security risks highlight the necessity of awareness, robust security protocols, and cautious engagement for anyone involved in this hidden part of the internet.
Legal and Ethical Risks of Access and Usage
Darknet websites are hidden parts of the internet accessible only through specialized software and networks, often associated with anonymous activities. While they can serve legitimate purposes such as protecting privacy and enabling free speech in oppressive regimes, they also pose significant security concerns and risks. Users who explore these sites may unintentionally expose themselves to malware, hacking attempts, or surveillance by malicious actors. The anonymity features of darknet websites can facilitate illegal activities, including drug trafficking, arms sales, and illicit data exchange, increasing the risk of involvement in criminal enterprises. These sites can also be targeted by law enforcement agencies aiming to combat criminal networks, making access potentially perilous for individuals involved.
In addition to security threats, there are substantial legal and ethical risks associated with accessing and using darknet websites. Engaging with content that includes illegal goods or services can lead to criminal charges, even if unintended or for research purposes. Many jurisdictions have strict laws against participating in or facilitating illegal transactions on such sites. Ethically, the use of darknet websites raises concerns about supporting illegal activities and compromising personal integrity. Law enforcement continually monitors darknet activities to identify and dismantle unlawful operations, highlighting the importance of understanding the serious legal consequences and moral implications involved. Navigating this hidden part of the internet requires caution, awareness of associated risks, and adherence to legal standards to prevent inadvertent misconduct.”
Exposure to Malware, Scams, and Surveillance
- All information should be free; knowledge belongs to the world yadda yadda.
- It brings to mind stories of scams, stolen identities, and dumps of hacked data.
- By having a dark web version of the site, Facebook gives its users other ways to access the social network, no matter their country.
- Hydra also featured numerous vendors selling false identification documents.
Darknet websites operate within a hidden layer of the internet, often used for a variety of purposes ranging from privacy protection to illicit activities. However, navigating these sites comes with significant security concerns and risks that users must be aware of. The anonymity provided by darknet websites can attract malicious actors who exploit vulnerabilities to distribute malware, carry out scams, or conduct illegal transactions.
One of the primary dangers associated with darknet websites is exposure to malware. Cybercriminals frequently use these platforms to spread malicious software, including viruses, ransomware, and spyware, often through seemingly legitimate downloads or links. Once malware infects a device, it can lead to data theft, financial loss, or further security breaches. The clandestine nature of darknet sites makes it difficult to identify and eliminate these threats quickly.
Scams are also prevalent on darknet websites, taking diverse forms such as fake marketplaces, phishing schemes, and fraudulent transactions. Unsuspecting users may fall victim to these schemes, losing money or sensitive information. The lack of regulation and oversight on these sites complicates efforts to combat scams and protect users, making vigilance essential when engaging in any activity on the darknet.
Surveillance issues add another layer of risk, as law enforcement agencies and malicious actors alike monitor certain activities on darknet websites. Users engaging in illegal transactions risk exposure through advanced tracking methods, which can lead to criminal investigations or personal data leaks. Even those seeking privacy may inadvertently attract unwanted attention if their activities are inconsistent or suspicious.
In summary, while darknet websites offer privacy and anonymity, they are fraught with security concerns, including exposure to malware, scams, and surveillance. Users should exercise extreme caution, employ robust cybersecurity practices, and be aware of the inherent risks associated with these hidden parts of the internet.
Risks of Encountering Illegal Content and Activities
Darknet websites are often associated with a range of security concerns and risks due to their anonymous and unregulated nature. Users navigating these sites may be exposed to various threats such as hacking attempts, malware, and scams that can compromise personal information and digital assets. Since these websites operate outside traditional oversight, malicious actors frequently exploit this environment to conduct illegal activities, increasing the likelihood of encountering illicit content. Engaging with darknet websites also carries the risk of inadvertently supporting criminal enterprises, which can have legal and ethical implications. It is essential for users to understand these risks and exercise caution to protect their privacy and safety when exploring or interacting within these hidden parts of the internet.
Darknet Marketplaces and Illegal Goods
Darknet marketplaces are hidden online platforms that facilitate the anonymous exchange of various goods and services, often existing outside the bounds of legal regulations. These websites operate on encrypted networks, making them difficult to trace and access, and are frequently associated with the trade of illegal items such as drugs, stolen data, counterfeit documents, and other illicit products. While some darknet sites provide a space for legitimate discussions and privacy-focused activities, many are exploited for illegal transactions. Exploring these websites reveals a complex ecosystem where privacy and anonymity are prioritized, but it also underscores the risks involved in accessing and engaging with illicit content. For example, darknet websites like this site offer gateways into these shadowy online worlds.
Drug and Weapon Markets
Darknet websites are hidden parts of the internet that operate outside the reach of traditional search engines and accessibility. These sites are often accessed through specialized browsers designed for anonymity, such as the Tor network. While the darknet serves legitimate purposes like protecting privacy and facilitating free expression, it is also frequently associated with illegal activities.
Among the various illicit activities conducted on darknet websites, marketplaces dealing with illegal goods are particularly notorious. These platforms often facilitate the sale and distribution of drugs, weapons, stolen data, and other prohibited items. The anonymous nature of these websites makes it challenging for law enforcement agencies to detect and dismantle such operations effectively.
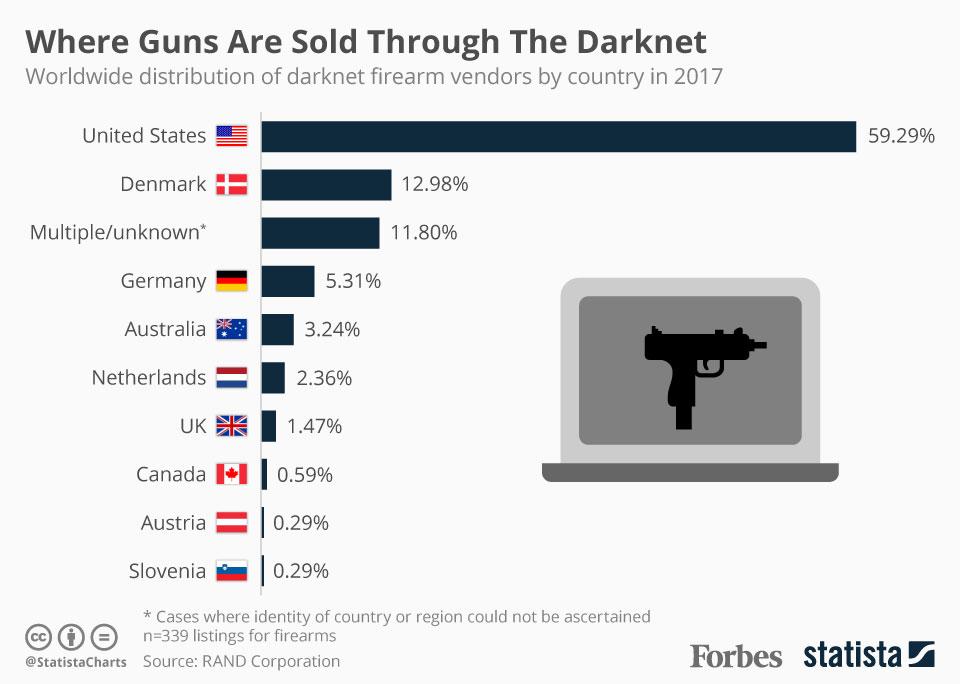
Drug markets on darknet websites have grown significantly over the years, providing a wide range of substances that can be shipped discreetly to buyers worldwide. Similarly, weapon markets, although less prevalent, pose serious security threats by enabling illegal arms trade. These markets operate largely in anonymity, with transactions often facilitated through cryptocurrencies to evade financial tracking.
Efforts to combat illegal activities on darknet websites include international cooperation among law enforcement agencies, advancements in digital tracking technologies, and increased awareness about the risks associated with engaging in these markets. Despite these measures, the clandestine nature of darknet websites allows illegal markets to persist, transforming them into complex challenges for regulatory authorities.
Stolen Data and Cybercrime Services
Darknet websites are hidden parts of the internet that require specialized software to access, such as Tor or I2P. These sites are often associated with illegal activities due to their anonymous nature, making them a hub for the exchange of illicit goods and services. Many users visit these dark web platforms to buy or sell illegal items while attempting to evade law enforcement detection.
One of the most concerning aspects of darknet marketplaces is their proliferation of illegal goods. These platforms facilitate the sale of weapons, drugs, counterfeit identification documents, and other unlawful products. The anonymity provided by darknet websites enables vendors and buyers to operate with minimal risk of being caught, leading to a flourishing black market.
Stolen data is another major commodity exchanged on darknet marketplaces. Cybercriminals often leverage these platforms to trade sensitive information such as credit card details, personal identification records, and login credentials. This stolen data is used for identity theft, fraud, and financial crimes, causing significant harm to individuals and organizations.
In addition, darknet websites serve as a marketplace for cybercrime services. Hackers and malicious actors offer hacking tools, malware, phishing kits, and even hiring cybercriminals to carry out targeted attacks. These services heighten the threat landscape, enabling even less experienced criminals to partake in cyberattacks that can lead to large-scale data breaches and financial losses.
Law enforcement agencies around the world continuously monitor and take action against illegal activities on darknet websites. However, the hidden and decentralized nature of these platforms makes policing efforts challenging. Awareness and cybersecurity measures are crucial for individuals and organizations to protect themselves from the risks associated with darknet marketplaces and the illegal goods and services they facilitate.
Fake Documents and Identity Theft Services
Darknet marketplaces are hidden online platforms that operate on encrypted networks, often accessed through specialized browsers. These sites facilitate a range of illegal activities, including the sale of prohibited goods and services. Users can navigate these sites anonymously, which attracts individuals seeking to buy or sell items outside the reach of law enforcement. The clandestine nature of darknet websites makes them a hotbed for illegal transactions and illicit commerce.
One of the most concerning aspects of darknet marketplaces is their involvement in trading illegal goods and services. These can include narcotics, firearms, stolen data, and counterfeit products. Among these illicit services, the sale of fake documents and identity theft services is particularly prevalent. Criminal actors offer forged passports, driver’s licenses, and other official documentation, enabling fraud and illegal entry into various domains. These fake documents are often used to deceive authorities, commit financial fraud, or facilitate illegal migration.
Darknet websites also serve as platforms for identity theft services, which provide stolen personal information, credit card details, and hacking tools. This information can be used to commit fraud, unauthorized purchases, or other cybercrimes. The anonymous environment of these sites complicates efforts to track down and shut down such operations, allowing them to flourish despite ongoing law enforcement efforts.
- Illegal Goods:
- Narcotics, firearms, and stolen data
- Counterfeit products and pirated media
- Other prohibited items facilitated by darknet marketplaces
- Fake Documents and Identity Theft Services:
- Forgery of passports, driver’s licenses, and other official documentation
- Offering stolen personal information and hacking tools
- Services that enable individuals to commit fraud and financial crimes
Combating these illegal activities requires continuous monitoring and cooperation among law enforcement agencies worldwide. Awareness and cautious online behavior are essential for individuals to avoid falling victim to scams or inadvertently supporting illegal operations associated with darknet websites.
Tools and Technologies for Navigating the Darknet
Exploring the dark net requires specialized tools and technologies that provide anonymity, security, and access to hidden networks. These tools help users navigate complex and often unindexed parts of the internet, where privacy is paramount. Darknet websites operate within this clandestine environment, offering a range of services and information not readily accessible through conventional browsers. To safely explore these sites, individuals often rely on technologies such as Tor, VPNs, and encryption protocols. For example, using the Tor Browser allows users to anonymously access dark net directories and marketplaces. Additionally, some enthusiasts utilize specific software designed for secure communications and data protection. For those interested in exploring darknet sites, there are resources and repositories that list active and reputable addresses, providing safer entry points into this hidden digital world. One of the notable darknet sites can be accessed through this link to get started securely.
The Tor Browser and Onion Routing
Exploring the darknet requires specialized tools and technologies designed to ensure privacy and anonymity. These tools enable users to access hidden websites and communicate securely, protecting them from surveillance and censorship.
One of the most widely used tools for navigating the darknet is the Tor Browser. Built on the principles of onion routing, Tor encrypts internet traffic and routes it through a series of volunteer-operated servers called nodes. This process obscures the origin and destination of the user’s data, providing a high level of anonymity. The Tor Browser is specifically designed to access websites hosted on the darknet, often identified by the “.onion” top-level domain, which are not accessible via conventional browsers.
Onion routing is a technique that enhances user privacy by wrapping data in multiple layers of encryption. As data passes through successive nodes, each node decrypts a layer, revealing only the location of the next node. This method prevents any single point from knowing both the origin and final destination of the data, significantly increasing security and anonymity.
In addition to the Tor Browser, various other tools assist in darknet navigation and security:
- VPN Services: Used alongside the Tor Browser to mask IP addresses further and add an extra layer of encryption.
- Secure Operating Systems: Such as Tails or Whonix, which are designed for privacy-focused activities and can run the Tor Browser securely.
- Encryption Tools: Including PGP for encrypting communications and files, ensuring data remains confidential even if intercepted.
- Search Engines and Directories: Specially curated for darknet websites, helping users find relevant hidden services safely.
While accessing darknet websites offers opportunities for privacy and free expression, it also requires awareness of potential risks and the importance of employing robust security tools. The combination of the Tor Browser, onion routing, and supplementary privacy tools creates a more secure environment for those seeking to explore these hidden parts of the internet safely.
VPNs and Additional Anonymity Layers
The darknet is a hidden part of the internet that requires specific tools and technologies to access and navigate securely. To explore darknet websites safely, users often rely on a combination of privacy-focused tools and layered security measures. These technologies are essential for protecting user identity and maintaining anonymity while browsing these sometimes sensitive and secretive sites.
One of the primary tools used for accessing the darknet is the Tor network, which routes user traffic through multiple relays to mask their location and identity. The Tor Browser is specially designed to connect to this network and browse hidden sites, often referred to as darknet websites. Its built-in privacy protections help prevent tracking and surveillance, making it a vital tool for those seeking anonymity.
In addition to Tor, Virtual Private Networks (VPNs) are frequently employed to add an extra layer of security. A VPN encrypts internet traffic and reroutes it through a server located in a different area, obscuring the user’s original IP address even further. When used together with Tor, VPNs can help mitigate some vulnerabilities and enhance privacy, although careful selection of reputable providers is crucial since some VPNs could potentially log user activity.
Beyond VPNs and Tor, users can implement additional layers of anonymity such as the use of secure operating systems like Tails, which are designed to run from a live USB and leave no traces on the host machine. Employing such systems reduces the risk of leaving digital footprints when exploring the dark web. Other security practices include disabling scripts, avoiding personal information disclosure, and handling cryptocurrency transactions with caution to prevent traceability.
Understanding and utilizing these tools and technologies is fundamental for anyone interested in exploring darknet websites responsibly and securely. While these measures significantly enhance anonymity, it’s important to stay informed about emerging threats and best practices to ensure safe navigation within this concealed part of the internet.
Encryption Protocols for Secure Transactions
Navigating the dark web requires specialized tools and technologies designed to ensure privacy, anonymity, and security. Darknet websites operate in a concealed part of the internet, often accessed through secure and encrypted channels to protect users from surveillance and tracking. Understanding the tools and protocols involved is essential for anyone interested in exploring this hidden domain safely.
One of the fundamental tools used for browsing darknet websites is the Tor Browser. It facilitates access to the dark web by routing internet traffic through a worldwide volunteer network, encrypting the data multiple times to obscure the user’s location and browsing activity. This layered encryption provides a high degree of anonymity, making it difficult for third parties to trace online actions.
In addition to browser tools, encryption protocols are vital for securing transactions and communications over the dark web. Protocols such as SSL/TLS are commonly employed to encrypt data exchanged between users and darknet sites, safeguarding sensitive information from interception. These encryption standards create a secure channel, ensuring that transactional data remains confidential even in potentially hostile environments.
- Secure Messaging Tools: Encrypted messaging applications like Signal or ProtonMail are often utilized for confidential communication, ensuring privacy beyond browsing.
- VPN Services: Virtual Private Networks add an extra layer of security by masking IP addresses and encrypting all internet traffic outside of the Tor network.
- Cryptocurrency Wallets: For financial transactions, secure wallets that employ strong cryptographic standards are essential, enabling anonymous and tamper-proof payments.
- Encryption Protocols: Protocols such as PGP (Pretty Good Privacy) are employed to encrypt emails and digital signatures, maintaining privacy and integrity.
Overall, the combination of specialized tools and robust encryption protocols is essential for safely exploring the darknet. These technologies not only facilitate access but also help ensure that privacy and security are maintained throughout digital interactions on the dark web.
Legal and Ethical Considerations in Darknet Usage
Engaging with darknet websites involves navigating a complex landscape where legal and ethical considerations are paramount. The anonymity offered by these sites provides a platform for a variety of activities, some of which may violate laws or ethical standards. Understanding the boundaries and responsibilities associated with darknet usage is crucial for users to avoid unintended legal consequences and to ensure that their actions adhere to moral principles. For instance, accessing certain darknet sites without proper precautions can inadvertently lead to involvement in illegal transactions or access to harmful content. It is essential for users to be aware of the risks and to operate within the limits of their local laws and ethical guidelines. Resources such as darknet safety guides can provide valuable insights on how to responsibly explore these hidden parts of the internet while maintaining legal and ethical integrity.
Legal Boundaries and International Regulations
Darknet websites operate within a complex landscape of legal and ethical considerations that users must navigate carefully. While the anonymity offered by the darknet provides privacy and freedom of expression, it also raises significant questions about legality and morality. Accessing or hosting certain types of content on these sites can have severe legal repercussions, depending on the jurisdiction in which an individual resides. Therefore, understanding the boundaries set by law is essential to avoid unintentional violations and potential penalties.
Legal boundaries and international regulations concerning darknet websites vary significantly across different countries. Some nations implement strict laws against the hosting, distribution, or access to illegal content on these platforms, including illicit drug markets, weapons trading, or child exploitation material. Other countries may have more permissive approaches but still enforce regulations against illegal activities conducted through darknet sites. It is crucial for users to be aware of local laws and international agreements that govern online conduct, as law enforcement agencies increasingly collaborate across borders to combat international crime networks operating via darknet platforms.
- Jurisdictional Differences: Laws regarding darknet activities differ widely among countries, with some explicitly banning access or certain types of content, while others lack specific legislation but enforce general criminal laws.
- International Cooperation: Multinational agencies work together to track illegal operations, making it risky to assume that activities on darknet sites are entirely untraceable.
- Legal Risks: Engaging in illegal activities, such as trading prohibited substances or distributing illicit materials, can lead to criminal charges, fines, or imprisonment.
- Ethical Implications: Even if a certain activity is not explicitly illegal in one jurisdiction, it may still be ethically questionable, especially when it involves harm to others or exploitation.
- Privacy vs. Legality: While darknet sites often prioritize user anonymity, this does not grant immunity from legal scrutiny, and authorities employ advanced techniques to identify and prosecute offenders.
In summary, users must be vigilant about the legal and ethical boundaries surrounding darknet websites. Compliance with applicable laws and ethical standards is essential to avoid serious legal consequences and to promote responsible use of digital anonymity tools. Recognizing the importance of international regulations helps users understand the broader implications and risks associated with engaging with darknet content.
Responsible and Ethical Use of Darknet Services

Darknet websites serve as gateways to an often hidden segment of the internet, offering privacy and anonymity for various users. While this technology has legitimate purposes such as protecting free speech in oppressive regimes and securing sensitive communications, it also presents significant ethical and legal challenges. Navigating the darknet requires a clear understanding of the boundaries set by laws and ethical standards to ensure responsible use and prevent harm.
Legal considerations are paramount when accessing or utilizing darknet websites. Many activities associated with the darknet, including illicit trade, hacking, and distribution of copyrighted material, are illegal in numerous jurisdictions. Engaging in such activities risks severe legal consequences, including fines and imprisonment. Users and operators must be aware of the laws applicable in their locations and refrain from engaging in illegal operations. Respecting intellectual property rights, privacy laws, and regulations surrounding data security is essential to maintaining lawful conduct.
Beyond legality, ethical considerations emphasize the importance of responsible behavior on darknet platforms. Users should prioritize respecting the privacy and safety of others, avoiding participation in or endorsement of harmful actions such as cyberbullying, scam schemes, or the distribution of illegal content. It is vital to recognize that despite the anonymity provided by darknet websites, actions can still have real-world impacts on individuals and communities. Promoting transparency, honesty, and respect within online interactions contributes to a safer environment for all users.
Operators and service providers on the darknet must also adhere to ethical standards, ensuring that their services do not facilitate criminal activity or harm. Implementing security measures, monitoring content responsibly, and cooperating with law enforcement when necessary help in maintaining a responsible online ecosystem. Users should exercise caution and discernment, seeking information from reputable sources and avoiding engagement in activities that may compromise their integrity or lead to legal issues.
In conclusion, engaging with darknet websites can offer valuable benefits when approached responsibly and ethically. Upholding legal standards, respecting individual rights, and promoting safe and honest interactions are critical components for ensuring that the dark web remains a tool for protection and privacy rather than a platform for harm. Awareness of and adherence to these considerations foster a more secure and ethical online environment for everyone involved.
Monitoring and Law Enforcement Efforts
Darknet websites operate within a unique digital environment characterized by heightened privacy and anonymity, raising complex legal and ethical considerations. While some users access the darknet for legitimate purposes such as privacy protection, journalists’ work, or activism, others exploit these platforms for illicit activities. Navigating this landscape demands careful attention to the boundaries between lawful conduct and criminal behavior, as well as the responsibilities of law enforcement and stakeholders to uphold ethical standards.
Legal considerations surrounding darknet websites primarily involve the enforcement of laws related to illegal activities such as drug trafficking, weapons sales, hacking, and human trafficking. Authorities must balance the need to investigate and shut down illicit platforms with respecting the privacy rights of users. The clandestine nature of the darknet complicates efforts to monitor and regulate activity, raising questions about jurisdiction, due process, and the extent of surveillance permissible under law.
Ethically, law enforcement agencies and online watchdogs face dilemmas about how to effectively combat criminal activities without infringing on individual rights and freedoms. Excessive monitoring or invasive tactics may lead to violations of privacy and civil liberties, undermining public trust. Conversely, insufficient action could allow illegal operations to persist, causing harm to individuals and communities.
In considering these issues, key points include:
- The importance of clear legal frameworks that define permissible and forbidden activities on the darknet to guide enforcement actions.
- The need for proportional and transparent monitoring methods that respect user privacy and uphold ethical standards.
- The responsibility of stakeholders to differentiate between illegal activities and lawful uses of pseudonymous platforms for protected purposes such as free expression.
- The role of international cooperation, given the borderless nature of darknet websites, in combating cross-jurisdictional crimes.
Overall, addressing the legal and ethical challenges associated with darknet websites requires a balanced approach that prioritizes public safety while safeguarding fundamental rights. Continuous dialogue among lawmakers, law enforcement, technology providers, and civil society is essential to develop effective and responsible strategies for managing the complex issues posed by the darknet.