Nexus Darknet Access Overview
Accessing the Nexus Darknet provides users with a gateway to a hidden layer of the internet that hosts a variety of anonymous and private services. This specialized network facilitates secure communication, data exchange, and access to information that is not available through conventional online channels. Nexus Darknet Access enables users to explore this mysterious digital environment while maintaining their privacy and security. Whether for research, personal privacy, or other reasons, understanding how to securely navigate the Nexus Darknet is essential for anyone interested in the deeper layers of the internet.
Understanding Nexus Market on the Tor Network
The Nexus darknet access provides users with a gateway to explore and navigate the complex and often hidden world of the Tor network, where various marketplaces and forums operate beyond conventional internet boundaries. Understanding the Nexus Market on the Tor Network is essential for those interested in the clandestine digital economy, as it offers insight into how these marketplaces facilitate anonymous transactions and information exchange. The Nexus darknet access aims to improve security and privacy, ensuring users can engage with these platforms with a level of confidentiality that is critical in such environments.
Nexus Market on the Tor Network serves as a hub for a wide range of goods and services, often involving sensitive or banned items. Its operation relies heavily on encryption and anonymization techniques to shield both buyers and sellers from detection and surveillance. By utilizing Nexus darknet access, users can gain entry into this concealed marketplace while maintaining privacy and security, which is fundamental to operating within these networks without exposing personal details.
To navigate the Nexus Market effectively, understanding the underlying infrastructure of the Tor network is important. The network’s decentralized nature and layered encryption help mask user identities and locations, fostering a safer environment for illicit exchanges. However, users must exercise caution and employ robust security measures to protect themselves from potential threats, such as scams or law enforcement efforts. Accessing the Nexus darknet requires a comprehensive knowledge of how these marketplaces function and the best practices for security and anonymity.

Overall, Nexus darknet access opens a window into the shadow economy facilitated by the Tor network. It provides the tools necessary for secure, anonymous participation in dark web activities while emphasizing the importance of vigilance and understanding the risks involved. As the landscape evolves, staying informed about the latest security protocols and market dynamics remains crucial for anyone engaged in or studying these clandestine digital environments.
The Role of Nexus Market in the Darknet Economy
Nexus Darknet Access provides users with a secure and reliable way to navigate the hidden layers of the internet, commonly known as the darknet. This platform offers tools and methods designed to protect user anonymity while gaining access to various marketplaces, forums, and resources that operate outside the conventional web. The importance of Nexus Darknet Access lies in its ability to enable safe exploration of a network often associated with both legitimate privacy concerns and illicit activities, ensuring users can operate with a higher level of security.
The Nexus Market plays a significant role in the darknet economy by serving as a hub for trading a wide range of goods and services. It functions as an underground marketplace where vendors and buyers engage in transactions that may include digital currencies, stolen data, hacking tools, and other illegal commodities. The presence of markets like Nexus Market highlights the complex and lucrative nature of the darknet economy, emphasizing the need for secure access methods such as Nexus Darknet Access to facilitate legal and safe engagement within this environment.
Overall, Nexus Darknet Access and the Nexus Market are integral components of the broader darknet ecosystem. They contribute to both the security of individual users seeking privacy and the functioning of underground economic activities. Understanding these elements is crucial for appreciating the dynamics of the darknet and the importance of secure navigation tools in protecting users’ identities and data.
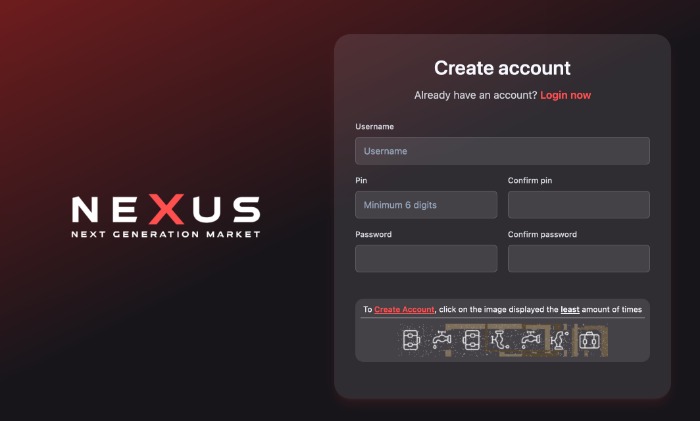
Methods of Accessing Nexus Darknet Marketplaces
Accessing Nexus Darknet Marketplaces involves navigating a specialized segment of the internet that operates beyond traditional browsing channels. These marketplaces are typically hosted on the Tor network, requiring specific tools and methods to connect securely and anonymously. Ensuring safe and reliable access is essential for users interested in the offerings of Nexus darknet access, which often involves understanding the various tools and techniques available for connecting to these hidden sites.
Official Nexus Onion Links
Accessing Nexus darknet marketplaces requires careful navigation through the specialized networks designed to provide anonymity and security for users. These marketplaces operate exclusively on the Tor network, making them accessible only through specific tools and methods tailored to maintain privacy and protect user identities. Understanding the various methods of accessing Nexus darknet marketplaces is essential for those seeking to explore this hidden part of the internet safely and securely.
To access Nexus darknet marketplaces, the primary method involves using the Tor Browser, a specialized web browser optimized for connecting through the Tor network. This browser enables users to reach onion sites that are not accessible via standard browsers. Ensuring that the Tor Browser is downloaded from official sources and kept updated is crucial to maintaining security while navigating the dark web.
Another method involves leveraging secure operating systems tailored for anonymity, such as Tails or Whonix. These operating systems are designed to route all internet traffic through the Tor network, providing an extra layer of security when accessing sensitive sites like Nexus darknet marketplaces. Users should familiarize themselves with proper configuration and security precautions to prevent leaks of personal information.
Accessing Nexus darknet marketplaces also relies on utilizing official Nexus onion links. These links are essential for connecting to the marketplaces securely and avoiding malicious sites. It is vital to verify the authenticity of these links through trusted sources or community forums to ensure safety while exploring the dark net.
Ultimately, maintaining anonymity and security when accessing Nexus darknet marketplaces demands diligent use of suitable tools, secure connections, and verification processes. By following these methods, users can navigate into the darknet world responsibly while minimizing risks associated with illegal activities or malicious threats. Proper understanding and cautious practices are the key to safely exploring the depths of the Nexus dark web environment.

Utilizing Nexus Mirrors During Downtime
Accessing Nexus darknet marketplaces requires careful navigation and awareness of different methods to ensure privacy and security. Due to the sensitive nature of darknets, users often seek reliable techniques to connect and browse these marketplaces while minimizing risks. One common strategy involves utilizing Nexus mirrors, especially during marketplace downtimes or technical issues, allowing users to maintain access and continue their activities seamlessly.
There are several methods to access Nexus darknet marketplaces effectively. The primary approaches include direct connection via Tor, using Nexus mirrors, and employing VPNs combined with anonymity tools to enhance privacy. Nexus darknet access often relies heavily on maintaining anonymity and avoiding detection by authorities or other malicious entities. By understanding and utilizing these methods, users can enhance their resilience against disruptions and maintain consistent access to essential marketplace features.
Methods of Accessing Nexus Darknet Marketplaces
- Using Tor Browser: The most basic and essential method involves accessing Nexus through the Tor network. Tor provides anonymity by routing traffic through multiple nodes, making it difficult to trace users’ locations. Users should ensure their Tor browser is up-to-date and properly configured for secure browsing.
- Utilizing Nexus Mirrors: During Nexus marketplace downtime or when the primary site is inaccessible, Nexus mirrors serve as alternative gateways. These mirror sites operate on different servers but replicate the core marketplace functions, allowing continued access without interruption.
- Employing VPNs and Privacy Tools: Combining VPN services with Tor enhances privacy by encrypting all traffic before it reaches the Tor network. This layered approach helps obscure user IP addresses and prevents fingerprinting or interception.
In practice, accessing Nexus darknet marketplaces requires a combination of secure communication methods and awareness of potential risks. Using Nexus mirrors during downtime ensures that users sustain access without relying solely on the primary site, which might be subject to takedowns or technical issues. Overall, mastering these techniques enhances the security and reliability of Nexus darknet access, supporting users in maintaining their activities in a safer manner.
Locating Trusted Nexus Darknet URLs
Accessing nexus darknet marketplaces requires careful navigation and awareness of security protocols to protect user privacy and safety. These sites typically operate on the Tor network, which provides anonymity by routing internet traffic through multiple servers. To access these marketplaces, users often need to use specialized browsers designed for anonymity, such as the Tor Browser, ensuring they can browse the dark web securely. Finding reliable and trusted Nexus darknet URLs involves exploring communities and forums that share updated links regularly, as addresses frequently change to maintain security. Using reputable sources for these URLs is critical to avoid malicious sites that could compromise personal information or security. Additionally, users should verify the credibility of the sites by checking for consistent uptime, community feedback, and reviews from trusted sources. When attempting to access nexus darknet marketplaces, employing robust security measures such as VPN usage, avoiding the use of personal information, and practicing good digital hygiene significantly reduce risks. Staying informed about the latest developments and updates within darknet communities can facilitate finding trusted Nexus darknet URLs and enhance the overall security of your browsing experience.
Nexus Market Features and Functionality
Nexus Market offers a comprehensive platform with advanced features and functionalities designed to facilitate secure and efficient trading within the darknet community. Its robust infrastructure provides users with a seamless experience, ensuring that transactions are conducted with privacy and safety as top priorities. The marketplace supports a wide range of products and services, backed by reliable encryption and user-centered design. For those interested in exploring encrypted marketplaces, Nexus darknet access serves as a gateway to a secure environment where anonymity is maintained at every step. This platform exemplifies the importance of trustworthy and feature-rich marketplaces in the dark web landscape, blending functionality with strict privacy measures to meet the needs of its users.
User Profile Customization and Settings
Nexus Darknet Access offers a comprehensive platform designed to facilitate secure and anonymous browsing within the darknet. Its features and functionalities are tailored to provide users with a seamless experience while maintaining privacy and safety. By utilizing advanced encryption and routing techniques, Nexus ensures that users can access hidden networks without exposing their identities or locations. The platform’s robust security measures make it a preferred choice for those seeking confidential communication and information exchange online.
The system boasts an array of Nexus Market features that streamline the buying and selling processes in the darknet ecosystem. Users can browse various marketplaces, access encrypted communication channels, and utilize escrow services to ensure transaction security. The intuitive interface allows users to navigate market listings efficiently, making it easier to find desired products or services while maintaining anonymity. Additionally, Nexus Market incorporates real-time updates and notifications, keeping users informed about marketplace activities and new listings.
User profile customization and settings are central to enhancing the overall experience of Nexus Darknet Access. Users can create detailed profiles that include preferences, security settings, and communication options. Customizable privacy controls enable individuals to manage their online footprint effectively, ensuring that their identity remains protected. The platform also offers options to set notification preferences, language choices, and device configurations, allowing for a tailored experience that aligns with user needs and security considerations. This level of personalization ensures that users can navigate the darknet with confidence and convenience, leveraging all the advanced features Nexus provides for a secure and efficient experience, including the special features available for Nexus Darknet Access.
Product Browsing and Search Capabilities
Nexus Darknet Access offers a comprehensive platform designed to facilitate seamless browsing and secure transactions within the dark web community. The Nexus Market features a user-friendly interface that allows users to navigate through various categories effortlessly, ensuring quick access to the products and services they seek. Its layout promotes efficient browsing, with clearly defined sections that simplify the overall user experience.
One of the key aspects of Nexus Market is its robust search functionality, enabling users to locate specific items rapidly. The search capabilities include advanced filters and keyword options that help narrow down results, making product discovery quick and straightforward. This efficient search system is particularly valuable for those engaging with Nexus Darknet Access, as it saves time and enhances safety by reducing the need for extensive browsing.
Product browsing on Nexus Market is designed to be intuitive, with listings that display essential details such as product descriptions, price points, and seller information. Users can review ratings and feedback from previous buyers, which adds an extra layer of trust and transparency. The platform’s structured approach to product display ensures that visitors can make informed purchasing decisions while maintaining anonymity and security.
Overall, Nexus Market’s features and functionality are tailored to provide a secure, efficient, and easy-to-navigate environment for accessing a wide range of darknet products and services. By integrating advanced search capabilities and streamlined browsing options, Nexus Darknet Access aims to enhance user satisfaction while prioritizing privacy and security standards.
Filtering and Navigation Tools
Nexus Market offers a sophisticated platform designed to facilitate secure and efficient access to darknet marketplaces. Its core features focus on providing users with seamless navigation, robust filtering options, and enhanced security measures, making it easier to locate desired products and services while maintaining anonymity. For those seeking to explore the nexus darknet access, understanding the market’s features and functionality is essential to ensure a smooth experience.
One of the standout aspects of Nexus Market is its advanced filtering and navigation tools. These tools allow users to refine searches based on various parameters such as product categories, vendor reputation, price ranges, and listing freshness. By enabling precise filtering, Nexus Market helps users quickly find relevant listings amidst a vast array of options. The intuitive navigation interface further enhances usability by categorizing products logically, making it simple for users to browse through different sections without confusion.
Additionally, Nexus Market employs comprehensive search capabilities that support keyword searches and advanced filters, facilitating rapid access to specific items. The platform’s filtering system is designed to be user-friendly, allowing quick adjustments to search criteria and view updates in real-time. This functionality is crucial for those interested in nexus darknet access, providing a streamlined process to locate vendors or products efficiently.
Overall, the combination of powerful filtering and navigation tools, along with secure access features, makes Nexus Market a preferred choice for users venturing into the nexus darknet access. The platform’s robust features ensure a smooth, anonymous, and efficient browsing experience, essential for navigating the complexities of darknet marketplaces.
Unique User Identification with XMR Addresses
Nexus Market offers a range of features and functionalities that cater to users seeking secure and private access to darknet markets. One of its key advantages is the integration of unique user identification through XMR (Monero) addresses, which enhances privacy and security in transactions. This system ensures that users can participate in marketplace activities without revealing their personal identities or transaction history, maintaining anonymity and protecting against surveillance.
The platform’s features include a user-friendly interface, robust security protocols, and seamless transaction capabilities. Utilizing XMR addresses for user identification helps mitigate the risks associated with conventional payment methods, such as traceability and financial profiling. This approach supports the core principles of privacy and decentralization inherent to darknet markets, making Nexus Market an attractive option for users prioritizing confidentiality.
In addition to privacy-focused payment solutions, Nexus Market provides functionalities like encrypted messaging, secure product listings, and escrow services to promote safe and reliable transactions. Its compatibility with darknet access allows users to navigate and utilize the platform effectively while maintaining their anonymity. The combination of these features with **Nexus darknet access** ensures a secure environment for exchanging goods and services without compromising user privacy.
Overall, Nexus Market’s incorporation of unique user identification via XMR addresses exemplifies its commitment to privacy-centric operations. This approach not only facilitates secure transactions but also reinforces trust within the community, making it a preferred choice for individuals seeking discreet marketplace access on the darknet.
Secure Access Practices
Securing access to sensitive networks requires stringent practices that prioritize privacy, confidentiality, and reliable authentication methods. As digital threats continue to evolve, so do the strategies to safeguard important information and maintain secure communication channels. When exploring the nexus darknet access, it is crucial to implement best practices that minimize vulnerabilities and ensure safe navigation through less accessible parts of the internet. Proper security measures enable users to access the darknet responsibly while protecting their identity and data from potential malicious actors.
- Never share your login credentials, and always verify your personal phrase at the login screen.
- This may result in some difficulty in narrowing down results by shipping locations, price or other factors.
- Markets like Nexus optimize user experience with search filters and discreet packaging guarantees, catering to global demand while maintaining operational security.
- The Tor Browser ensures your traffic is encrypted, and a VPN provides an additional layer of privacy.
- Finally, always verify you are accessing the market through the correct onion URL or a trusted mirror link to prevent phishing.
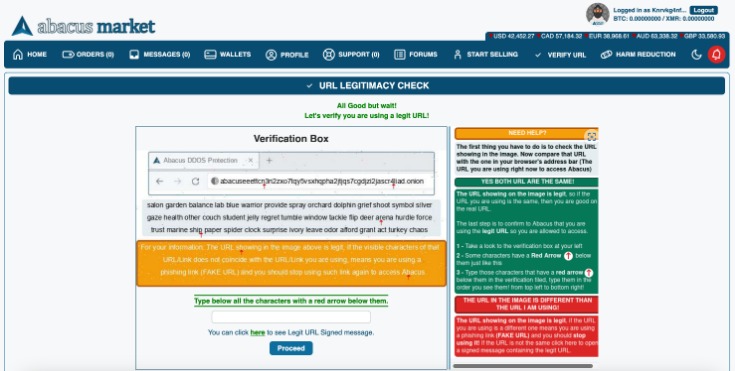
Verifying Nexus Links for Authenticity
Secure access practices are essential when navigating the nexus darknet to protect your privacy and ensure the authenticity of the links you engage with. Due to the inherently anonymous nature of the nexus darknet, verifying the legitimacy of links and sources is crucial to avoid malicious sites or scams. Implementing strict verification procedures helps users maintain security and prevent exposure to harmful content.
One important step in maintaining secure access is to verify the authenticity of nexus links before clicking or sharing. This involves examining the link structure for signs of tampering or deception, such as misspelled domain names or suspicious URL patterns. Cross-referencing links with trusted sources or community-recommended directories can also enhance confidence in their legitimacy.
Additionally, employing tools such as digital signatures or cryptographic verification methods can provide an extra layer of assurance that a link has not been altered or maliciously crafted. When accessing the nexus darknet, always ensure you’re using secure browsers and encrypted connections, such as Tor, to safeguard your identity and prevent interception of data.
Implementing these verification practices is vital for anyone seeking to access the nexus darknet safely. By diligently checking links for authenticity and following secure access protocols, users can significantly reduce risks and navigate this complex environment with greater confidence and security.
Utilizing Verification Tools and Trusted Sources
Ensuring secure access practices is essential when navigating the nexus darknet, as it involves sensitive information and potential risks. Utilizing verification tools helps confirm the authenticity of sources and prevents exposure to malicious entities. Trusted sources play a crucial role in maintaining safety by providing reliable and verified content, thereby minimizing the likelihood of encountering scams or harmful software. Employing multi-factor authentication and encryption methods further enhances security, safeguarding user identities and data integrity. When accessing the nexus darknet, it is vital to stay informed about the latest security protocols and to adopt a cautious approach, always verifying the legitimacy of the platforms and resources involved. This layered security strategy ensures that users can explore the darknet responsibly while protecting themselves from potential threats and maintaining a secure environment for their activities.
Keeping Up with Updated Nexus Links
Securing access to the Nexus darknet requires implementing robust procedures that prioritize safety and privacy. As digital environments evolve rapidly, it is essential to stay informed about the latest updates and developments related to Nexus links. Regularly monitoring trusted sources ensures users are aware of any changes or vulnerabilities, helping to prevent potential security breaches. Utilizing secure access practices involves employing strong encryption methods, practicing vigilant detection of phishing attempts, and maintaining updated software to block malicious activities. Additionally, employing multi-factor authentication can provide an extra layer of security during login processes. Staying current with updated Nexus links not only safeguards personal data but also enhances the overall integrity of interactions within the darknet ecosystem. Ultimately, adopting these practices fosters a safer experience for users navigating the complex landscape of darknet networks.
Overcoming Access Challenges
Accessing the Nexus Darknet can pose significant challenges due to its hidden nature and security measures designed to protect user anonymity. Overcoming these access difficulties requires understanding specialized tools and techniques to navigate this concealed network safely and effectively. Whether for research, privacy protection, or establishing secure communications, mastering the methods to gain entry is essential for many users interested in the Nexus darknet access. By leveraging appropriate resources and strategies, users can enhance their ability to connect securely within this complex environment, ensuring their activities remain private and protected from unwanted oversight. Recognizing these challenges and solutions is the first step toward a successful and secure darknet experience.
Dealing with Server Outages and Network Restrictions
Accessing the Nexus Darknet can pose significant challenges due to various technical and security barriers, including server outages and network restrictions. Users often encounter difficulties when trying to connect to darknet resources, especially during times of server downtime or when facing firewalls that block access to certain networks. Overcoming these access challenges requires a strategic approach to ensure reliable and secure connectivity.
One effective method to deal with server outages is to utilize multiple network pathways or mirror sites. This redundancy allows users to switch to alternative servers if the primary one becomes unavailable, maintaining continuous access to necessary resources. Regularly checking for updates or announcements from service providers can also help preemptively identify potential outages and plan accordingly.
Dealing with network restrictions often involves employing privacy-focused tools such as Virtual Private Networks (VPNs) or Tor to bypass firewalls and censorship. These tools encrypt internet traffic and route it through secure servers, masking user identities and circumventing restrictions imposed by certain networks or jurisdictions. When accessing the Nexus Darknet, ensuring that your privacy tools are up-to-date and configured correctly is crucial for maintaining security and anonymity.
Another vital aspect of overcoming access challenges involves understanding the network infrastructure and choosing the right tools to optimize connectivity. Using proxies, custom DNS settings, or secure tunneling protocols can help improve accessibility and reduce latency, enhancing the overall experience when navigating the darknet.
In conclusion, resilient access to the Nexus Darknet requires a combination of technical solutions and proactive measures. Stay informed about network conditions and utilize appropriate privacy tools to mitigate the impact of server outages and network restrictions, ensuring continuous and secure connectivity to darknet resources.
Using Mirrors and Alternative Access Points
Accessing the nexus darknet can present significant challenges due to restrictions, censorship, or technical obstacles. To navigate these hurdles effectively, users often turn to alternative methods such as mirrors or different access points that facilitate entry into the darknet environment safely and securely. Employing these strategies ensures continued connectivity and enhances browsing resilience against potential disruptions.
One common approach is utilizing mirror sites that replicate the original nexus darknet content. These mirrors provide alternative pathways for users to access necessary resources without relying solely on the primary sites, which may be blocked or down. Additionally, leveraging multiple access points can help bypass network restrictions, ensuring uninterrupted access to the darknet ecosystem.
- Use VPNs or proxy services to mask your IP address and circumvent geographical restrictions.
- Identify and connect through different entry points or gateways that may be less restricted or blocked.
- Utilize specialized tools designed for accessing darknet sites securely, such as Tor or other anonymizing networks.
- Switch between different mirrors and alternative access points frequently to reduce the risk of being permanently blocked.
- Stay informed about updates and new access methods within the darknet community to maintain reliable connectivity.
In order to maintain safe and reliable access, it is essential to stay vigilant about evolving restrictions and technical barriers. By employing mirrors and alternative access points, users can effectively navigate these challenges and access vital information or resources on the nexus darknet without interruption. This approach not only enhances security but also ensures continued connectivity in a space where censorship and filtering are common.
Strategies for Safe and Reliable Navigation
Accessing the nexus darknet can present significant challenges due to its concealed nature and the layers of security implemented to protect users and content. Overcoming these access challenges requires a combination of technical knowledge and cautious practices to ensure safe and reliable navigation. Understanding the importance of privacy and security is essential when exploring the darknet, particularly through trusted methods and tools designed to maintain anonymity while preventing potential risks.
One effective strategy for safe navigation involves using reputable VPN services to mask your IP address and encrypt your internet traffic. This helps to prevent tracking and provides an additional layer of security when attempting to reach hidden services like nexus darknet access. Employing specialized browsers such as Tor also enhances privacy by routing your connection through multiple nodes, making it significantly harder to trace your activity or location.
It is crucial to keep software and security tools updated regularly to defend against vulnerabilities that could be exploited by malicious actors. Using strong, unique passwords and enabling two-factor authentication on accounts related to darknet activities further secures your digital presence. Additionally, being cautious about the information shared and avoiding downloads or links from untrusted sources can mitigate common risks associated with darknet exploration.
For those seeking reliable navigation, consult reliable guides and community resources that offer best practices for accessing the darknet securely. Recognizing and avoiding scams or malicious sites is paramount; always verify the legitimacy of the sources and tools used to access the nexus darknet. By adopting these strategies, users can navigate the darker corners of the internet with greater safety and confidence, minimizing risks while maintaining access to vital information and services.
Preventing Risks and Ensuring Anonymity
Accessing the nexus darknet securely requires careful attention to preventing risks and ensuring user anonymity. With the increasing presence of illegal activities and cyber threats, protecting your identity and data is more important than ever. Utilizing reliable tools and practices can help minimize exposure to malicious actors and safeguard sensitive information. Understanding the best methods for nexus darknet access allows users to navigate these networks with greater confidence while maintaining privacy and security.
Best Practices for Protecting User Identity
Preventing risks and ensuring anonymity are paramount when accessing the nexus darknet, especially given the sensitive nature of its environment. Users must prioritize safeguarding their identity to avoid potential threats such as tracking, unauthorized access, or legal repercussions. Implementing robust privacy measures is essential for secure navigation and communication within this concealed network.
One of the foundational best practices is utilizing tools like Virtual Private Networks (VPNs) to mask your IP address and encrypt your internet traffic. This adds a layer of security, making it more difficult for third parties to monitor your online activity. Coupled with the use of secure browsers designed for darknet access, such as Tor, users can significantly enhance their anonymity and reduce exposure to risks.
When exploring the nexus darknet, it is crucial to avoid revealing personal information or engaging in activities that could compromise your identity. Employing pseudonyms, avoiding login credentials linked to your real identity, and refraining from sharing identifiable details are vital steps. Additionally, keeping software and security tools up to date helps mitigate vulnerabilities that could be exploited by malicious actors.
Encryption methods are also vital in ensuring data privacy. Always ensure that communication channels within the nexus darknet utilize end-to-end encryption services to protect the integrity and confidentiality of your exchanges. Furthermore, it is advisable to disconnect any devices that are not secured or that could inadvertently expose your identity, thus maintaining a safe operational environment.
As users navigate the nexus darknet, understanding and applying these best practices can greatly reduce risks and promote safer, anonymous access. Whether for research, privacy protection, or other legitimate activities, prioritizing security and anonymity is essential to preserve your digital footprint and prevent potential threats in this complex environment.
Recognizing and Avoiding Phishing Sites
Accessing the Nexus Darknet can offer various opportunities for users seeking privacy and anonymity online. However, it is essential to prioritize safety by preventing risks and ensuring the protection of your identity. Navigating this hidden part of the internet involves understanding common threats, such as malicious sites designed to deceive or harm users. Recognizing and avoiding phishing sites is a critical step in maintaining security and preserving anonymity when exploring the Nexus Darknet or similar platforms.
Phishing sites often imitate legitimate pages to steal personal information or install malicious software. These deceptive sites can appear convincing, making it vital to identify warning signs before proceeding. Ensuring your safety requires adopting best practices for digital security on the Darknet, where anonymity is paramount but also vulnerable to exploitation.
- Use Secure and Updated Tools: Always utilize trusted encryption tools and keep your browsing software updated to safeguard against known vulnerabilities.
- Verify URLs Carefully: Phishing sites often use subtle misspellings or confusing domain names. Confirm URLs before entering any personal or financial information.
- Stick to Reputable Sources: Rely on well-known platforms and communities for guidance and access to the Nexus Darknet, avoiding unknown or suspicious links.
- Utilize VPNs and Tor: Combining a Virtual Private Network with the Tor browser enhances your anonymity by encrypting traffic and anonymizing your location.
- Be Wary of Unsolicited Communications: Avoid clicking on links or providing information in response to unexpected messages or emails.
- Regularly Monitor System Security: Conduct routine scans for malware or spyware that can compromise your identity or device.
Recognizing phishing sites involves paying attention to indicators such as poor design quality, inconsistent domain names, or requests for sensitive information that legitimate sites wouldn’t ask for. Staying vigilant helps prevent falling prey to malicious actors on the Nexus Darknet or other parts of the hidden web. By following these practices, users can better protect their anonymity and reduce the risks associated with accessing the dark web.
Maintaining Privacy During Market Usage
Accessing the Nexus darknet involves navigating a complex environment where security and privacy are paramount. To prevent risks associated with such activities, it is essential to employ robust security measures, including the use of secure connections and anonymization tools. Ensuring that your online footprint remains minimal helps protect your identity and prevents potential targeted attacks.
Maintaining anonymity is crucial when using darknet networks like Nexus. Utilizing tools such as VPNs, Tor, or other anonymity-preserving technologies can obscure your IP address and location. Regularly updating your software and security protocols further reduces vulnerabilities, making it more difficult for malicious actors to trace your activities. Being cautious about sharing personal information and avoiding suspicious links also contribute to preserving your anonymity.
In addition to technical precautions, understanding the importance of data encryption during market usage is vital. Encrypting communications and transactions helps safeguard sensitive data from interception or eavesdropping. Adopting safe browsing habits and staying informed about potential threats ensures ongoing privacy protection. When accessing the Nexus darknet, these practices collectively help mitigate risks and preserve user privacy, fostering a safer and more secure environment for legitimate activities.