Understanding the Dark Web
The dark web is a concealed part of the internet that requires specialized tools and knowledge to access. Often misunderstood, it hosts a variety of sites that operate anonymously, providing a platform for both legitimate privacy-focused activities and illicit dealings. One notable aspect of the dark web is the presence of darknet sites, which are not indexed by traditional search engines and require specific browser configurations to reach. These sites can serve numerous purposes, from protecting free speech in repressive regimes to facilitating illegal transactions. Exploring a darknet site can reveal the complex ecosystem that exists beyond the surface web, offering insights into the importance of security and privacy in the digital age. For those interested in further exploration, a popular darknet site can be accessed through various anonymous networks, allowing users to delve into this hidden world safely and responsibly.
Definition of the Dark Web
The dark web is a hidden part of the internet that is not accessible through standard search engines or regular browsers. It consists of websites and online content that require specialized software, such as Tor or I2P, to access. These networks offer a layer of anonymity and privacy for users, often used for both legitimate purposes like protecting privacy and for illicit activities. The dark web is a subset of the deep web, which includes all web pages not indexed by search engines, but it is distinguished by its focus on anonymity and untraceable communications.
A darknet site typically operates on overlay networks that are intentionally hidden and require specific configurations or permissions to access. These sites often host forums, marketplaces, and communication channels where users can connect without revealing their identities. While some people use darknet sites for secure communication and privacy protection, they are also associated with illegal activities such as drug trafficking, cybercrime, and black market transactions. Understanding the dark web’s structure and purpose is crucial for recognizing its dual nature as both a tool for privacy and a hub for illegal dealings.
Differences Between Surface Web, Deep Web, and Dark Web
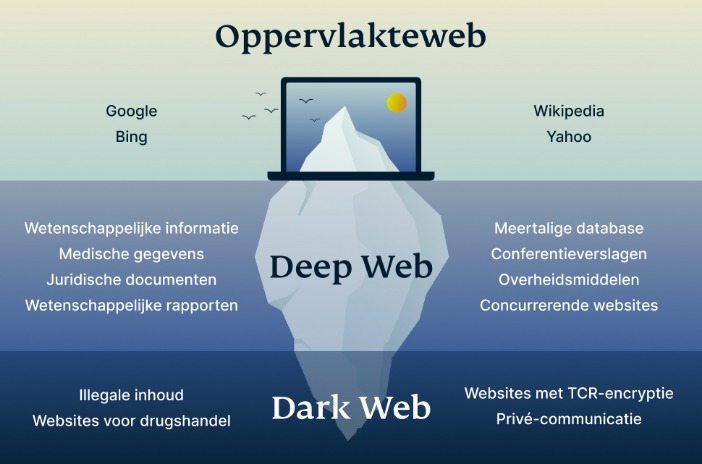
The internet is comprised of various layers, each serving different purposes and levels of accessibility. Understanding these layers is essential for navigating and recognizing the risks associated with different types of online content, particularly when it comes to darknet sites. One of these layers is the Dark Web, a hidden part of the internet that requires specific software and configurations to access, distinguishing it from the more publicly accessible parts of the web.
- By identifying and analyzing threat intelligence from the dark web, businesses can extract actionable information, leading to more accurate and high-quality alerts.
- However, China and some other countries have banned use of The Onion Router, preventing their citizens from accessing the network.
- Investigators reportedly unveiled Vallerius’ real identity through his bitcoin transactions.
- This makes it extremely fast, more than 1000x faster than R-CNN and 100x faster than Fast R-CNN.
- We’ve collected content from hundreds of relevant Tor sites, IRC channels, forums, and paste sites.
The Surface Web is the visible, easily accessible part of the internet that most users engage with daily. It includes websites that are indexed by search engines and readily available through standard browsers. In contrast, the Deep Web comprises all online content that is not indexed by search engines, such as private databases, emails, and password-protected sites. While much of the Deep Web contains innocuous or necessary information, some sections are intentionally hidden for privacy and security reasons.
The Dark Web represents a smaller, intentionally concealed part of the Deep Web. Accessed through specialized software such as Tor, it offers anonymity for both users and website operators. This environment facilitates various activities, ranging from legitimate ones like protecting privacy and journalistic work to illicit activities. Darknet sites operate within this hidden layer, often hosting marketplaces, forums, and information exchanges that are not accessible through conventional browsing methods.
Understanding the differences between these web layers is crucial for safe navigation and awareness of potential dangers. While the Dark Web and darknet sites can provide valuable tools for privacy-conscious individuals and journalists, they are also known for hosting illegal activities. Users should exercise caution and ensure they are well-informed about the legal and security implications of exploring these hidden online spaces.
Purpose and Origins of the Dark Web
The dark web is a hidden part of the internet that is not accessible through standard search engines or browsers. It consists of a collection of websites and online services that require special software, configurations, or authorization to access, often providing anonymity to its users. These sites are part of a broader network known as the darknet, which operates on overlay networks such as Tor or I2P, designed to conceal both the location of users and the sites themselves.
The purpose of the dark web varies widely. While some use it for legitimate activities like anonymous journalism, privacy protection for whistleblowers, or secure communication in oppressive regimes, it is also known for hosting illegal activities. Darknet sites can serve as marketplaces for illicit goods, forums for criminal coordination, or platforms for malicious activities. The anonymity features provided by the dark web attract both those seeking privacy and those involved in illegal transactions.
The origins of the dark web trace back to efforts in the 1990s to develop secure and private communication channels for government and military purposes. Over time, these technologies became accessible to the public, evolving into the dark web as a space for private and anonymous interactions. The development of networks like Tor was pivotal, enabling users to browse the internet without revealing their identities and allowing for the creation of darknet sites. Today, the dark web remains a complex environment, balancing privacy rights with the challenges of criminal misuse.
Accessing the Dark Web
Accessing the dark web involves navigating a hidden part of the internet that is not indexed by standard search engines. This segment, often referred to as the darknet, hosting a variety of websites that require special tools and protocols to reach. Users interested in exploring darknet sites must employ dedicated software such as Tor, which provides anonymity and security. It is important to approach this area with caution, as it can contain both legitimate and illicit content. For those seeking a specific darknet site, there are secure and well-known portals that serve as gateways to these hidden networks. To begin your journey, consider exploring trusted darknet site repositories or directories that facilitate safe and informed access to this mysterious part of the internet. For example, you might find valued resources on sites like Nexusafe to help guide your exploration safely.

Specialized Software and Tools
Accessing the dark web requires specialized knowledge and tools due to its encrypted and anonymized nature. The dark web is a subset of the internet that is not accessible through standard search engines and requires specific software to access securely. It often hosts anonymous forums, marketplaces, and other resources used for various purposes, both legitimate and illicit. Navigating this space safely necessitates understanding the proper tools and precautions to protect your privacy and security.
One of the most common methods to access the dark web is through the use of specialized software like The Onion Router (Tor). Tor directs internet traffic through a worldwide network of relays, encrypting data at each step, which conceals the user’s location and activity. This anonymity allows users to access dark web sites, which often have unique domain extensions such as “.onion.” Beyond Tor, there are additional tools like Tails and I2P that offer enhanced privacy features and access to different parts of the dark web.
Utilizing these tools effectively involves understanding their configurations and maintaining strict security hygiene. Security measures include using VPNs in conjunction with Tor, avoiding personal information disclosure, and keeping software updated. It is also important to use reputable sources for obtaining these tools to prevent malware or compromised software. Accessing a darknet site safely requires a cautious approach, awareness of legal boundaries, and a focus on privacy to protect oneself from potential threats or illegal activities that may be associated with these sites.
The Role of Tor Browser
Accessing the dark web involves navigating a segment of the internet that is not indexed by traditional search engines and requires specialized tools to ensure anonymity and security. Darknet sites often host sensitive or private information, making it a unique area of online activity. To access these sites safely, understanding the role of the Tor Browser is essential, as it provides the necessary means to browse the dark web securely and anonymously.
The Tor Browser is a modified version of Mozilla Firefox that routes your internet traffic through a global network of relays, concealing your IP address and encrypting your data. This layered approach helps protect user identity and privacy, making it possible to access darknet sites without revealing personal information. The process of accessing the dark web using Tor involves downloading the browser, installing it, and then navigating to various darknet sites that are only accessible through this network.
Using the Tor Browser to access darknet sites involves several steps:
- Download the Tor Browser from the official website to ensure safety and authenticity.
- Install the browser on your device, following the instructions provided.
- Open the Tor Browser and allow it to connect to the Tor network.
- Use the browser’s built-in search engine or enter specific onion addresses to visit darknet sites.
While exploring the darknet, it is crucial to practice caution and prioritize security by avoiding sharing personal information and refraining from engaging in illegal activities. The combination of the Tor Browser and responsible browsing habits helps maintain user anonymity and ensures a safer experience on darknet sites. This network plays an important role in facilitating privacy-conscious activities and providing a platform for free expression in restrictive environments.
Using .onion Domains for Dark Web Sites
Accessing the dark web involves navigating a hidden part of the internet that is not indexed by standard search engines. To reach darknet sites, users typically utilize specialized software such as the Tor browser, which allows for anonymous browsing by routing traffic through a global network of relays. These networks are designed to protect user privacy and maintain the anonymity of both visitors and site operators.
Darknet sites often use .onion domains, which are part of a specialized addressing system only accessible via the Tor network. These sites differ from regular websites in that their addresses are not linked to conventional IP addresses and are generated through cryptographic algorithms, making them harder to track or block. Accessing a darknet site with a .onion domain requires users to use the Tor browser, ensuring that their identity and location remain hidden during their browsing session.
While the dark web is frequently associated with illegal activities, it also hosts legitimate content such as private communications, censorship-resistant publishing platforms, and secure marketplaces. It is essential for users to exercise caution and remain aware of potential security risks when exploring darknet sites. Proper security measures, such as using VPNs and avoiding personal information disclosure, can help protect individuals while they navigate this concealed part of the internet.
Additional Access Methods and Anonymizing Tools
Accessing the dark web involves navigating a part of the internet that is not indexed by standard search engines and requires specialized tools and methods to ensure privacy and security. Darknet sites often operate on hidden networks, making them less accessible through conventional browsers. For users interested in exploring these sites, understanding the various access methods and anonymizing tools is essential to maintain confidentiality and safeguard personal information.
Several additional access methods are commonly used to reach darknet sites beyond the standard Tor browser. These include the use of Virtual Private Networks (VPNs) which help mask your IP address before connecting to the Tor network, adding an extra layer of security. Some users also utilize proxy servers to route their traffic, making it more difficult to trace activities back to them. Additionally, specialized software like I2P (Invisible Internet Project) offers alternative anonymous networks suitable for accessing specific darknet communities and sites.
Maintaining anonymity while browsing darknet sites is crucial, and a variety of tools are available to assist in this. The Tor browser remains the most popular method, designed to anonymize traffic by routing it through multiple relays. Combining Tor with a VPN can significantly enhance privacy, although it requires careful configuration. Other tools such as Tails, a live operating system, enable users to run a secure, ephemeral environment that leaves no trace on the device used. Using privacy-focused web browsers and security extensions further helps prevent tracking and unauthorized data collection.
In summary, accessing darknet sites demands both the right tools and prudent practices. By employing multiple layers of protection and staying informed about the latest anonymizing technologies, users can explore this hidden part of the internet with increased safety and confidence.
Common Types of Dark Web Sites
The dark web hosts a variety of sites that serve different purposes, ranging from illicit activities to privacy-focused communication platforms. These sites, often accessed through specialized browsers, are part of the broader darknet network. Among the common types of dark web sites are marketplaces, forums, and information portals, each catering to specific user needs. For those interested in exploring this elusive part of the internet, there are protected and secure sites such as darknet marketplaces which exemplify the diversity and complexity of darknet sites. Understanding these different types of sites helps demystify the dark web and highlights the importance of cybersecurity and legal considerations when navigating this hidden internet realm.
Legitimate and Confidential Resources
The darknet hosts a variety of websites that serve different purposes, ranging from legitimate activities to illicit operations. These sites are part of the hidden part of the internet accessible only through specialized software such as Tor, which provides anonymity for both operators and users. Among these, some darknet sites are dedicated to legitimate and confidential resources, offering services that protect privacy and promote free expression in oppressive environments.
Common types of darknet sites include forums, marketplaces, informational portals, and communication platforms. Many legitimate sites focus on privacy-conscious activities like anonymous communication, secure file sharing, and access to censored information. These sites often serve journalists, activists, and whistleblowers who require confidentiality and protection from surveillance or repression.
Additionally, there are darknet sites that are intended for confidential research and data sharing within academic or professional communities. They offer a secure environment for collaboration without exposing sensitive information. Despite the association with illegal activities, many darknet sites uphold principles of privacy and security for valid and ethical reasons.
It is essential to recognize that the darknet’s anonymity features make it a complex landscape, where legitimate and dangerous content coexist. Users seeking confidential resources should exercise caution and understand the purpose of the sites they visit. Proper knowledge about darknet sites helps distinguish between platforms meant for privacy and those involved in unlawful endeavors, ensuring a safer browsing experience.
Illegal Marketplaces and Black Markets
The dark web hosts a variety of sites, some of which are hidden from the standard internet and accessible only through specialized tools like Tor. Among these, darknet sites serve diverse purposes, ranging from privacy-focused communication to illicit activities. A significant portion of these sites are involved in illegal marketplaces and black markets, where illicit goods and services are bought and sold without oversight or regulation.
One of the most common types of darknet sites are illegal marketplaces. These marketplaces often facilitate the trade of drugs, weapons, counterfeit currency, stolen data, and other prohibited items. They operate under a layer of anonymity, making law enforcement efforts challenging. Black markets on the dark web provide a platform for vendors to reach buyers discreetly, with transactions usually conducted using cryptocurrencies for added privacy.
Other types of darknet sites include forums and communities that host discussions on controversial topics such as hacking, illegal surveillance, and illicit trade. These sites often serve as hubs for hackers and cybercriminals to exchange information, tools, and techniques. Additionally, some darknet sites focus on hosting stolen data, including credit card information, personal identities, and corporate secrets, which are then sold or leaked for financial gain.
Despite the prevalence of illegal activities, not all darknet sites are used for unlawful purposes. There are also legitimate sites dedicated to privacy, free speech, and secure communication for journalists, activists, and whistleblowers operating in restrictive environments. However, the presence of illegal marketplaces and black markets remains a significant concern, highlighting the importance of vigilance and security when navigating these hidden parts of the internet.
Mirrored and Hidden Web Services
The dark web hosts a variety of sites that operate beyond the reach of standard search engines and are often associated with both legitimate and illicit activities. Understanding the common types of dark web sites, including mirrored and hidden web services, is essential for navigating this concealed part of the internet responsibly. These sites serve different purposes and utilize specific techniques to maintain their anonymity and security.
Darknet sites can generally be categorized into several types based on their content and accessibility methods. Among these, mirrored sites and hidden web services are particularly noteworthy due to their role in maintaining accessibility and obscurity in the dark web environment.
- Dark Web Marketplaces: These are platforms where users can buy and sell goods and services, often illicit, in a secure and anonymous manner.
- Whistleblower Platforms and Forums: Sites dedicated to sharing sensitive information or discussing topics that may be suppressed or censored elsewhere.
- Dark Web News and Information Portals: Websites that publish news, blogs, or resources relevant to dark web users or broader privacy-conscious communities.
- Hidden Services: Servers or websites not indexed by standard search engines, accessible only through specific configurations or networks, often using technologies like Tor or I2P.
Mirrored sites are duplicates of original web pages that are intentionally hosted on multiple servers, sometimes across different regions, to ensure accessibility even if one source is blocked or taken offline. In the context of the dark web, mirroring helps protect critical information and maintain service continuity for darknet sites like darknet sites, which often encounter censorship or shutdowns.
Hidden web services refer to sites and resources that are deliberately concealed and cannot be accessed through traditional browsing. These services often use encryption and anonymization technologies, making them difficult to detect or shut down. They include anonymous forums, covert data repositories, and clandestine marketplaces. The use of specialized networks such as Tor allows users to access these hidden services securely while maintaining privacy and anonymity.
Understanding these various dark web site types is vital for anyone exploring this environment, whether for research, privacy protection, or awareness of online security threats. Stay informed about the technologies and techniques used to access and protect access to these hidden corners of the internet.
Directories and Indexes (e.g., Hidden Wiki)
The darknet hosts a variety of sites designed to operate quietly and securely, often hidden from regular search engines and requiring specific configurations to access. These sites serve diverse purposes, ranging from legitimate privacy-focused communication to illicit activities. Understanding the common types of dark web sites, including directories and indexes, can help users navigate this complex environment more safely and effectively.
One prevalent type of darknet site is the directory or index service, which acts as a centralized hub for discovering other hidden services. These directories organize links to various dark web sites, making it easier for users to find resources without knowing exact addresses. A well-known example is a site that aggregates links to legal and illegal content, offering categorized listings to facilitate browsing.
Another common type is community forums and marketplaces, where users can discuss topics, share information, or buy and sell goods and services—often illegally. These marketplaces are typically highly secure and anonymous, using encryption technologies to protect the identities of participants. Darknet sites like these serve as vital nodes in the underground economy, offering everything from stolen data to counterfeit documents.
Additionally, the darknet hosts a range of info-hosting sites and blogs, which provide tutorials, news, and commentary on various topics, including privacy techniques, encryption tools, or current events impacting the darknet community. Many of these sites also function as darknet directories, listing other hidden services or archives for easier access.
Darknet sites like the Hidden Wiki exemplify the directory type, offering links to numerous other sites, including forums, marketplaces, and informational resources. These indexes are essential gateways for both new users seeking to understand the darknet environment and seasoned users expanding their activities. While they can be valuable sources of information, caution is advised due to the presence of illegal or malicious sites among legitimate ones.
Dark Web Marketplaces and Commerce
The dark web has become a complex and clandestine part of the internet, where anonymous marketplaces facilitate a wide range of trade activities. Darknet site markets often host illicit transactions, from illegal drugs to stolen data, making them a focal point for both criminal operations and law enforcement investigations. Understanding how these darknet sites operate is crucial for grasping the broader landscape of online commerce behind the veil of anonymity. Many of these marketplaces rely heavily on advanced encryption and peer-to-peer networks to maintain user privacy and security. For those interested in exploring some of these hidden markets, resources like this darknet marketplace offer insight into the structure and scope of online commerce on the dark web. Navigation through these sites requires caution and awareness of their risks and legal implications.
Popular Dark Web Marketplaces
The darknet marketplace scene is a complex and often controversial aspect of online commerce, operating within the hidden layers of the internet. These sites are accessed via specialized software that anonymizes user identities and locations, providing a platform for various types of transactions, some legal and some illicit. This environment attracts a diverse user base and features a wide array of products and services that are not readily available on the surface web.
Popular darknet marketplaces in recent years have gained notoriety due to their extensive product catalogs, robust security features, and user-friendly interfaces. Many of these sites facilitate the sale of goods ranging from digital assets to physical items, often requiring cryptocurrencies for transactions to enhance anonymity. Despite their reputation for illegal activities, some marketplaces focus on legitimate vendors, offering various services that benefit from privacy and security enhancements inherent to the darknet.
The darknet site 1 serves as a prime example of how these platforms operate, combining advanced encryption technologies with community-driven moderation to create a relatively safer environment for participants. While law enforcement agencies continuously monitor and attempt to shut down these marketplaces, new sites frequently emerge, adapting to evolving security measures and user demands. Understanding the dynamics of darknet marketplaces is crucial for appreciating their role in global online commerce, whether for illicit trades or privacy-focused transactions.
Types of Goods and Services Offered
Darknet sites, often accessed through specialized browsers, serve as platforms for a variety of online activities that are not visible on traditional the surface web. Among these sites, dark web marketplaces are known for their role in facilitating the anonymous exchange of goods and services, often operating beyond legal boundaries. These marketplaces leverage encryption and anonymization tools to protect the identities of both buyers and sellers, creating a unique environment for commerce.
Dark web marketplaces typically feature a broad range of goods and services, some of which are legally dubious or outright illegal. Commonly traded items include illicit drugs, weapons, stolen data, counterfeit currency, and hacking tools. In addition to physical products, these platforms also facilitate transactions involving stolen financial information and sophisticated cybercrime services. The anonymity provided by darknet sites makes it easier for vendors to operate without fear of detection, attracting a wide array of illegal activities.
Beyond tangible goods, dark web marketplaces also host a variety of services. These can encompass illegal hacking and cyberattack solutions, forged documents, illegal gambling, and even contract-based criminal activities. Such services cater to individuals seeking to evade law enforcement or conduct illicit activities with a degree of discretion. This diverse ecosystem underscores the importance of understanding the risks associated with these sites and the ongoing efforts by authorities to disrupt illegal operations.
While some users turn to these dark web marketplaces for illegal purposes, others are interested in the implications for cybersecurity and law enforcement. The clandestine nature of these platforms makes them difficult to monitor and shut down, posing ongoing challenges for authorities worldwide. As technology evolves, so do the methods employed by criminals operating on darknet sites, emphasizing the need for continued vigilance and awareness of the complex landscape of dark web commerce.
Methods of Payment, Focus on Cryptocurrency
Darknet sites, often associated with the deep and dark web, are hidden destinations on the internet that require special software and configurations to access. These sites are frequently employed for anonymous communication and transactions, attracting a variety of users engaging in both legitimate and illicit activities. One prominent aspect of these marketplaces is their commercial operations, which facilitate the buying and selling of goods and services outside traditional online platforms.
Markets operating on the dark web utilize a range of methods for payments, with cryptocurrencies being the dominant choice. The inherent pseudonymity and decentralization offered by cryptocurrencies like Bitcoin, Monero, and others make them particularly attractive for transactions that seek to preserve privacy and evade detection. These digital currencies enable users to conduct exchanges without revealing personal identities, providing a layer of anonymity essential for both lawful privacy concerns and illicit transactions.
Cryptocurrency payments in dark web marketplaces are typically executed through secure, encrypted channels to protect user identities and transaction details. This enhances the confidentiality of both buyers and sellers, complicating efforts by authorities to track and regulate such activities. The widespread adoption of cryptocurrency as a payment method continues to influence the operation of darknet marketplaces, making them resilient to traditional financial surveillance and enforcement efforts.
Overall, the focus on cryptocurrency as a method of payment underscores the importance of privacy and security in darknet site commerce. While these platforms can be used for legitimate purposes, their association with illegal goods and services remains a concern, prompting ongoing efforts to monitor and regulate dark web activities. As technology and law enforcement strategies evolve, the landscape of darknet site commerce and its reliance on cryptocurrency continue to develop in complex ways.
Case Study: The Silk Road and Its Impact
The Dark Web has become a controversial and complex frontier for online commerce, with marketplaces that operate beyond the reach of traditional law enforcement and regulatory frameworks. These darknet sites provide a platform for anonymous transactions, often facilitating the exchange of illegal goods and services. Among the most infamous examples is The Silk Road, a pioneering darknet marketplace that gained notoriety for its role in enabling the sale of illicit substances and other illegal items. Its existence highlighted both the potential of anonymous online commerce and the severe challenges in regulating and policing such activities.
The Silk Road operated as a hidden marketplace utilizing encryption and cryptocurrencies to maintain user anonymity and facilitate transactions outside the conventional financial system. Its founder aimed to create a decentralized platform free from government interference, which initially attracted a broad user base seeking discreet ways to buy and sell across borders. However, this focus on privacy and anonymity also made it a hub for illegal activities, including drug trafficking, weapons sales, and other illicit dealings.
The impact of the Silk Road on darknet markets and online commerce was profound. It demonstrated the viability and scale of anonymous marketplaces, inspiring a wave of similar platforms that emerged following its shutdown. Law enforcement agencies worldwide faced significant hurdles in combating these sites, as their decentralized and encrypted nature made monitoring and intervention particularly challenging. The rise of darknet sites like the Silk Road underlined the need for new approaches to cybersecurity, legal enforcement, and international cooperation.
Furthermore, the Silk Road case raised awareness about the importance of cybersecurity measures, digital footprints, and the ethics surrounding online anonymity. It also sparked debates on the balance between privacy rights and the need for regulation in digital spaces. As darknet sites continue to evolve, understanding their dynamics and the lessons from early marketplaces remains crucial for policymakers, technologists, and law enforcement professionals aiming to manage illegal online activities while respecting legitimate privacy concerns.
Risks and Dangers of the Dark Web
The dark web presents a complex and often dangerous realm within the internet, characterized by its anonymous and unregulated nature. Accessing darknet sites can expose users to a variety of risks, including illegal activities, scams, and malicious threats. The hidden layers of the dark web make it difficult to monitor and control, increasing the potential for harm. Navigating this shadowy part of the internet requires awareness and caution, especially considering the various dangers associated with darknet sites. For those interested in exploring this area securely, it is essential to understand these risks and take appropriate safety measures.
Malware and Infection Risks
The dark web, often associated with anonymous browsing and hidden marketplaces, also presents significant risks and dangers that users should be aware of. Accessing darknet sites can expose individuals to various security threats, including malware, viruses, and other malicious infections. These dangers are frequently embedded within seemingly legitimate or enticing content, making it critical to approach such sites with caution.
One of the primary risks associated with the dark web is the rampant spread of malware. Cybercriminals often use darknet sites to distribute malicious software disguised as legitimate files or links. Visiting these sites without proper security measures can lead to infections that compromise personal data, login credentials, and financial information. Malware infections can also include ransomware, which encrypts users’ files and demands payment for their release.
In addition to malware, darknet sites can be hotspots for scams and fraudulent activities designed to steal personal information or financial assets. Users may unknowingly download infected attachments or click on malicious links, leading to infections that can spread across devices or networks. The risk intensifies when using unsecured networks or outdated security systems, making protective measures such as updated antivirus software and firewall protection essential.
Engaging with darknet sites also poses dangers related to illegal activities and exposure to harmful content. The anonymity provided by such sites can tempt malicious actors to conduct illegal trades, distribute illegal substances, or promote other illicit behaviors. This environment increases the probability of encountering dangerous scams or even being targeted for cyberattacks.
In summary, entering the darknet through sites that are often associated with illicit activities carries inherent risks of malware infection, scams, and exposure to harmful content. Protecting oneself involves employing strong cybersecurity practices, avoiding suspicious downloads or links, and being cautious of the potential dangers lurking behind darknet sites. Staying informed about these threats helps mitigate the risks involved and ensures safer browsing experiences.
Cybersecurity Threats and Exploits
The dark web, often accessed through specialized networks such as the darknet site, presents a range of significant risks and dangers for users. While it offers anonymity and privacy for various legitimate purposes, it is also a haven for illegal activities and malicious actors. Engaging with darknet sites can expose users to cybersecurity threats that can compromise personal data, financial information, and digital assets. Cybercriminals frequently exploit vulnerabilities on these platforms to distribute malware, conduct scams, and perform identity theft. The clandestine nature of the dark web makes it challenging for authorities to monitor and shut down illegal activities, increasing the danger for unwary visitors.
One of the primary cybersecurity threats associated with darknet sites is the spread of malicious software. Hackers often deploy malware to infect devices accessing these sites, which can lead to data breaches or the hijacking of sensitive information. Exploits targeting security flaws in browsers or operating systems are common, creating opportunities for attackers to gain unauthorized access. Furthermore, darknet sites are often used for illegal trade, including the sale of stolen data, forged documents, and illicit substances. This commercial activity attracts cybercriminals who employ sophisticated exploits to conceal their identities and operations, increasing the overall threat landscape.
Users should be aware that simply visiting a darknet site can introduce vulnerabilities or expose them to scams and phishing schemes. Cybercriminals frequently create fake darknet sites to lure unsuspecting visitors into revealing personal information or downloading malicious files. The danger is compounded by the difficulty in verifying the legitimacy of these sites, as anonymity tools provide little assurance of authenticity. Overall, the darknet site environment poses serious cybersecurity risks, and individuals must exercise extreme caution if they choose to explore it, understanding the associated exploits and dangers involved.
Scams, Phishing, and Fraudulent Activities
The darknet, often accessed through specialized software, is known for hosting a wide range of illicit activities that pose significant risks to users. Among the most concerning dangers are scams, phishing attacks, and various fraudulent schemes that proliferate on darknet sites. These activities are designed to deceive users, steal personal and financial information, and ultimately lead to financial loss or identity theft. Users should exercise extreme caution when exploring dark web content, as not all sites are legitimate or safe.
One of the primary risks associated with darknet sites is the prevalence of scams crafted to exploit unsuspecting visitors. These scams often involve fake marketplaces, counterfeit currencies, or false investment opportunities, luring users into giving away sensitive data or money. Additionally, phishing schemes are common, with malicious actors creating convincing fake login pages to capture login credentials for various accounts. Once compromised, these credentials can be used for further criminal activities or sold on illicit markets.
Fraudulent activities on the dark web extend beyond scams and phishing. Darknet site operators or users may engage in illegal trade of stolen data, illegal substances, or counterfeit documents. Engaging with these activities not only risks legal repercussions but also exposes individuals to potential scams or malicious malware. Malicious software distributed via darknet sites can infect devices, leading to further security breaches or ransomware infections that encrypt data and demand ransom payments.
It is vital for anyone considering exploring the darknet to be aware of these risks and dangers. Navigating these sites without proper knowledge and safety measures can result in compromised privacy, financial loss, or legal issues. Staying informed and exercising caution can help mitigate these risks while online activities remain within the boundaries of legality and security.
Legal and Physical Dangers
The dark web, often accessed through specialized networks like the darknet site, presents a range of risks and dangers that users should be aware of. While it offers anonymity and access to hidden content, it also exposes individuals to significant legal and physical hazards. Navigating this part of the internet requires caution, as illegal activities such as drug trafficking, stolen data exchanges, and illicit services frequently occur on darknet sites, increasing the likelihood of encountering criminal behavior.
Legal dangers are among the most pressing concerns associated with the dark web. Engaging in activities such as purchasing illegal substances, hacking services, or stolen data can lead to severe criminal charges. Authorities actively monitor darknet sites to identify and prosecute offenders, making unwary users vulnerable to prosecution even if they did not intend to commit a crime. Furthermore, simply accessing certain darknet content may be illegal in some jurisdictions, potentially resulting in penalties or fines.
In addition to legal risks, physical dangers also pose a significant threat. Darknet sites often facilitate transactions that involve physical exchange, such as drugs or weapons. Those involved in these activities may face violence, scams, or intimidation from other criminal entities operating within the darknet. Moreover, users who attempt to buy goods from darknet sites can become victims of fraud, receiving counterfeit or dangerous products, or they may expose themselves to hacking, identity theft, or malware that can compromise personal safety and security.
Overall, while the darknet offers anonymity and access to discreet information, it is fraught with hazards that can have serious legal and physical consequences. Individuals should exercise extreme caution and be fully aware of these risks before exploring darknet sites or engaging with their contents.
Protecting Yourself on the Dark Web
Navigating the dark web can pose significant security risks, but understanding how to protect yourself is essential for maintaining your privacy and safety. The darknet, a hidden part of the internet accessible via specialized networks, often hosts sites that require extra caution due to illegal activities and malicious actors. By taking appropriate security measures, such as using secure connections and avoiding sharing personal information, you can reduce the chances of falling victim to scams or cyber threats. For those exploring or operating on darknet sites, it is crucial to understand the risks and employ best practices to safeguard your identity and data. Knowledge about how to stay protected can include using trusted privacy tools and accessing reputable darknet sites through secure, anonymized connections like Tor, which ensures enhanced anonymity when browsing such sites.
Best Practices for Safe Navigation
Exploring the dark web can be intriguing for many, but it also poses significant risks to personal security and privacy. Navigating darknets such as darknet sites requires careful attention to safety measures to protect yourself from scams, hacks, and malicious activities. Understanding how to stay secure is essential for maintaining your anonymity and safeguarding your sensitive information while accessing these hidden parts of the internet.
To ensure safe navigation on the dark web, consider adopting these best practices:
- Use a reliable Virtual Private Network (VPN) to hide your IP address and encrypt your internet connection, providing an extra layer of anonymity when accessing darknet sites.
- Download and utilize the Tor Browser, which is specifically designed for accessing darknets securely and anonymously. Always keep it updated to benefit from the latest security patches.
- Avoid revealing personal information or engaging in transactions that could compromise your identity. Handle any dealings discreetly and with caution.
- Ensure your device has reputable security software installed, including antivirus and anti-malware tools, to detect and prevent potential threats.
- Stay vigilant for suspicious links or messages that could lead to phishing sites or malware downloads, which are common tactics used to compromise users on darknet sites.
- Be cautious about the content you access; illegal or untrustworthy darknet sites can contain malicious scripts or scams designed to steal information or damage your device.
- Regularly clear your browser data and use privacy settings to minimize digital footprints and prevent tracking.
- Educate yourself about common scams and threats encountered on the dark web to recognize warning signs early and avoid falling victim.
- If possible, avoid using personal accounts or email addresses when navigating darknets to maintain anonymity.
- Stay informed about the latest security updates and best practices for dark web navigation to continuously enhance your online safety measures.
By following these guidelines, users can better protect themselves while exploring darknet sites. Maintaining caution, staying informed, and employing robust security measures are key to a safer experience on the dark web.
Use of VPNs and Additional Security Measures
Engaging with darknet sites can expose individuals to a variety of security risks, making it essential to implement robust protection measures. The dark web, often associated with anonymous transactions and confidential exchanges, requires heightened vigilance to safeguard personal information and digital assets. Using a reliable VPN is one of the most effective ways to enhance your security when navigating these hidden parts of the internet. A VPN encrypts your internet connection, masking your IP address and location, thereby preventing cyber threats and unauthorized tracking.
In addition to using a VPN, adopting other security measures can significantly reduce your vulnerability. Regularly updating your operating system and software ensures that known security flaws are patched promptly. Employ strong, unique passwords for every account and consider using password managers to keep track of them securely. Enabling two-factor authentication adds an additional layer of protection, making it more difficult for malicious actors to access your accounts.
If you are exploring darknet sites, it’s crucial to maintain a cautious digital footprint. Avoid sharing personal information or engaging in activities that could compromise your security. Using privacy-focused tools such as Tor can help anonymize your browsing, but remember that no tool guarantees complete safety. Combining these precautions with vigilance and responsible browsing practices can help protect you from scams, malware, and other cyber threats present in the dark web environment.
Understanding Anonymity and Privacy Protections
Exploring the darknet can be a way to access hidden corners of the internet, but it also poses significant privacy and security risks. When navigating darknet sites, it is crucial to understand how to protect your identity and personal information from malicious actors and surveillance. Ensuring your anonymity requires implementing specific strategies and tools designed to safeguard your digital footprint.
One of the fundamental steps to protect yourself on the darknet is understanding the importance of anonymity and privacy protections. Using specialized browsing tools, such as the Tor network, allows users to conceal their IP addresses and encrypt their communications, making it difficult for third parties to track their activities. Beyond using Tor, employing comprehensive privacy practices can significantly reduce the likelihood of identification or data breaches.
Here are several essential tips for maintaining your privacy while exploring darknet sites:
- Use the Tor Browser: This tool is crucial for accessing dark web content securely and anonymously by routing your traffic through multiple servers.
- Avoid revealing personal information: Never share personal details such as your real name, address, phone number, or email account on darknet sites.
- Utilize cryptocurrency carefully: When engaging in transactions, use secure and privacy-focused cryptocurrencies to reduce traceability.
- Implement strong security practices: Use unique, complex passwords and enable two-factor authentication whenever possible.
- Maintain operational security: Do not disable security settings or download files from untrusted sources, as these actions can compromise your identity.
Remember that the darknet, while offering privacy protections, also contains many risks. Staying vigilant, utilizing secure tools, and practicing good operational security are essential to protect yourself when exploring or conducting activities on darknet sites.
Recognizing and Avoiding Scams and Malicious Links
Interacting with darknet sites can expose individuals to various security risks, including scams and malicious links. Protecting yourself while navigating these hidden parts of the internet requires awareness and vigilance. Since darknet sites often operate anonymously, scammers may exploit this anonymity to deceive users through fraudulent schemes or misleading links. Recognizing common signs of scam activity, such as offers that seem too good to be true or unexpected requests for personal information, is essential for maintaining safety.
To avoid falling victim to scams on darknet sites, always verify the credibility of sources before engaging or sharing any sensitive data. Be cautious of clicking on links that appear suspicious or unfamiliar, as they may lead to malicious websites designed to infect your device or steal your information. Using reputable security tools, such as updated antivirus software and VPNs, can further mitigate risks by providing an additional layer of protection against malware and tracking attempts. Remember, vigilance and skepticism are your best defenses when exploring the darker corners of the internet.
Additionally, it is advisable to keep your software up to date and avoid downloading files from untrusted sources on darknet sites. If you encounter a suspicious link or encounter a potential scam, exit immediately and avoid engaging further. Educating yourself about common scams and threat tactics associated with darknet sites can help you recognize threats early. Staying cautious and being prepared ensures your online safety while exploring this complex and often unpredictable part of the web.
Legal and Ethical Considerations
Engaging with darknet sites involves navigating a complex landscape of legal and ethical considerations that are crucial for responsible use. These underground platforms often facilitate a range of activities, some of which may violate laws or ethical standards. Understanding the boundaries and potential repercussions is essential for anyone exploring or interacting with darknet environments. It is important to recognize the privacy and security risks involved, as well as the legal implications associated with accessing certain content or services, such as darknet sites like Darknet marketplace. Ensuring compliance with applicable laws and maintaining ethical integrity can help protect individuals from legal action and ethical dilemmas.
Legal Status of Dark Web Activities
Engaging with darknet sites involves navigating a complex landscape of legal and ethical considerations that are crucial for users to understand. The darknet, a part of the internet accessible only through specialized anonymizing software, hosts a wide range of activities, some of which are lawful while others are illegal. It is important to recognize that many activities associated with the darknet, particularly those involving illicit content or transactions, can have severe legal repercussions.
Legally, the status of activities on darknet sites varies significantly depending on jurisdiction. While browsing or using the darknet for lawful purposes may not be illegal in itself, participating in illegal activities such as drug trafficking, illegal weapons trading, or distribution of copyrighted materials can lead to criminal charges. Law enforcement agencies worldwide actively monitor such activities, and individuals involved in illegal operations risk prosecution, penalties, and imprisonment.
From an ethical standpoint, users should consider the implications of their actions on the darknet. Even if certain activities are not explicitly illegal, they can still raise moral concerns, especially if they contribute to harmful practices or exploit vulnerable populations. The darknet site environment often attracts illicit activities, and engaging with such content can inadvertently support criminal enterprises, raising significant ethical questions.
Understanding the legal status of darknet activities is fundamental for anyone exploring this part of the internet. Compliance with local laws, awareness of the potential risks, and adherence to ethical standards are essential to navigate the darknet responsibly and avoid unintended legal or moral consequences.
Risks of Engaging in Illegal Activities
Engaging with darknet sites involves navigating a complex landscape where legal and ethical considerations are paramount. These sites often host content that can be highly sensitive, controversial, or illegal, making it essential to understand the potential consequences of involvement. Accessing or participating in activities on darknet sites without proper knowledge can inadvertently lead to serious legal ramifications.
One of the primary risks associated with darknet sites is the potential for involvement in illegal activities such as drug trafficking, counterfeit goods exchange, or cybercrime operations. Engaging in such activities not only violates local and international laws but can also result in criminal charges, heavy fines, and imprisonment. Law enforcement agencies worldwide actively monitor illegal activities on the darknet to combat these issues, making clandestine operations increasingly risky.
From an ethical standpoint, participating in an illegal darknet site can contribute to harm and exploitation. Many of these sites facilitate activities that violate human rights, promote violence, or enable fraudulent schemes. Supporting or enabling such operations can tarnish personal and professional reputations and raise moral concerns about contributing to criminal enterprises.
Moreover, there are significant security risks when dealing with darknet sites. These platforms are often riddled with scams, malware, and hacking attempts designed to steal personal information or financial data. Users who engage in illegal activities may become targets of law enforcement sting operations or cybercriminal attacks, leading to financial loss or legal action.
Ultimately, venturing into darknet sites without awareness of the legal and ethical boundaries can have devastating consequences. It is crucial to prioritize lawful and morally responsible behavior, ensuring that online activities align with both legal standards and ethical principles to avoid severe penalties and support a safer digital environment.
Ethical Use and Responsible Behavior
Engaging with a darknet site requires careful consideration of legal and ethical responsibilities to ensure responsible behavior. The darknet often hosts content that can be legally sensitive or legally prohibited in many jurisdictions. It is essential to understand local laws and regulations to avoid unintended legal consequences. Responsible use involves ensuring that any activities undertaken are lawful and do not contribute to harmful behaviors or illegal transactions, such as the trade of forbidden substances, stolen data, or illicit services.
Respecting privacy and confidentiality is vital when navigating these environments. Users should be cautious about the information they share and avoid participating in or endorsing unlawful activities. Ethical conduct extends beyond legality, encompassing honesty, integrity, and respect for others’ rights and safety. Engaging ethically on a darknet site means abstaining from malicious actions, such as hacking, spreading malware, or facilitating illegal trade, which can harm individuals and society at large.
Moreover, it is important to be aware of the potential risks involved, including exposure to scams, malicious software, or law enforcement surveillance. Practicing responsible behavior helps protect oneself and others from harm and contributes to maintaining a safer digital environment. Upholding these standards ensures that engagement with darknet sites remains within the bounds of legality and morality, promoting a secure and respectful online space for all users.
Conclusion and Future Outlook
As the landscape of the internet continues to evolve, darknet sites remain a complex facet of online activity, offering both opportunities and challenges. Understanding the conclusion and future outlook for these hidden networks is essential for gaining insights into their role within cybersecurity, privacy, and illegal operations. With advancements in technology and increasing awareness, the darknet is expected to adapt and develop in new ways, influencing various sectors and raising important questions about regulation and security. Exploring reputable darknet sites like Nexusafe can provide valuable perspectives on this ever-changing environment. Staying informed about the latest trends and tools will be crucial for navigating the future of darknet sites responsibly and securely.

The Evolving Nature of the Dark Web
The Dark Web continues to be a constantly evolving virtual space, characterized by its ability to adapt to technological advancements and shifting security measures. As a hidden part of the internet, it offers both opportunities and challenges, serving as a platform for anonymous communication, legitimate privacy-focused activities, as well as illicit transactions. The emergence of new tools and anonymizing technologies marks an ongoing transformation, making it increasingly difficult for authorities to monitor and regulate activity within darknet sites. This dynamic landscape necessitates continuous innovation in security protocols and investigative techniques to ensure safety and legality.
Looking ahead, the future of the Dark Web is likely to involve a delicate balance between safeguarding privacy rights and preventing illegal activities. Advances in encryption and decentralized networks could further enhance user anonymity but may also complicate efforts to combat cybercrime and terrorism. Policymakers, cybersecurity experts, and technology developers must collaborate to establish effective strategies that protect users’ privacy without compromising security. As darknet sites become more sophisticated, staying informed about these developments will be essential for maintaining a secure and responsible digital environment.
Technological Advances and Security Developments
The landscape of darknet sites continues to evolve rapidly, shaped by ongoing technological advancements and increasing security measures. As users navigate this clandestine part of the internet, it is crucial to understand emerging trends and the future trajectory of this digital environment.
Technological advances are playing a significant role in enhancing the accessibility and resilience of darknet sites. Innovations such as decentralized hosting platforms, improved encryption protocols, and anonymous communication tools are making it easier for users to access and maintain these sites while reducing the risk of detection and shutdown. The integration of blockchain technology and decentralized networks further bolsters the security and censorship resistance of darknet platforms, ensuring their continued existence despite legal and governmental interventions.
Security developments are also at the forefront, with heightened emphasis on privacy-preserving technologies. Advanced encryption techniques, multi-layered anonymity systems, and automated threat detection help protect both site operators and users from cyber threats and law enforcement incursions. This relentless focus on security ensures that darknet sites remain a sanctuary for illicit activities, though it also complicates efforts to combat illegal operations conducted through these platforms.
- Emerging technologies such as artificial intelligence and machine learning are being utilized to detect suspicious activity and monitor network vulnerabilities, further strengthening security measures.
- The future of darknet sites is likely to see increased use of cryptocurrencies for anonymous transactions, reinforcing the privacy of users and operators.
- Advances in hardware and software are expected to improve the usability and reliability of darknet sites, making them more accessible to a broader user base.
- Legal and regulatory frameworks are anticipated to adapt, attempting to address the challenges posed by these sites while balancing concerns related to privacy and free expression.
In conclusion, the future outlook of darknet sites involves a complex interplay of technological innovation and security enhancements. As these platforms become more sophisticated and resilient, ongoing efforts by law enforcement and cybersecurity professionals will be essential to address the challenges they pose. Continuous advancements are shaping a landscape where darknet sites, including darknet site platforms, are likely to persist as a controversial yet integral part of the digital ecosystem.
Impact on Society and Cybersecurity Landscape
The landscape of darknet sites continues to evolve rapidly, reflecting broader changes in internet usage, technology, and societal dynamics. As these hidden networks expand, they pose both opportunities and challenges for users and authorities alike. The future of the darknet is likely to see increased integration of advanced encryption and anonymization tools, making access more secure but also complicating efforts to monitor and regulate illicit activities.
Looking forward, innovations such as decentralized platforms and blockchain technology could further shape the darknet, enhancing privacy and resilience against takedowns. This ongoing development will have profound implications for law enforcement, regulatory agencies, and cybersecurity professionals, requiring them to adapt swiftly to emerging threats and vulnerabilities.
The impact on society is multifaceted. On one hand, darknet sites provide a space for free expression and privacy preservation, especially for those in oppressive regimes or vulnerable communities. On the other hand, they also facilitate illegal activities like illicit trade, cybercrime, and trafficking, which can harm individuals and destabilize social order. As a result, balancing the rights to privacy with the need for security remains a critical challenge.
Within the cybersecurity landscape, protecting against threats originating from darknet sites has become a priority. Organizations are investing more in threat intelligence, monitoring tools, and defensive strategies to detect and mitigate malicious activities linked to these hidden networks. Understanding the complex ecosystem of darknet sites, including their role in the cybercrime ecosystem, is essential for developing effective policies and technological solutions to safeguard public and digital security.